Fakebat Delivered Via Several Active Malvertising Campaigns
February was a particularly busy month for search-based malvertising with the number of incidents we documented almost doubling. We saw similar payloads being dropped but also a few new ones that were particularly good at evading detection.
One malware family we have been tracking on this blog is FakeBat. It is very unique in that the threat actor uses MSIX installers packaged with heavily obfuscated PowerShell code. For weeks, the malvertiser helping to distribute this malware was abusing the same URL shortener services which may have made the attack somewhat predictable. We saw them experimenting with new redirectors and in particular leveraging legitimate websites to bypass security checks.
Another interesting aspect is the diversity of the latest campaigns. For a while, we saw the same software brands (Parsec, Freecad) being impersonated over and over again. With this latest wave of FakeBat malvertising, we are seeing many different brands being targeted.
All the incidents described in this blog have been reported to Google.
New redirection chain
During the past several weeks, FakeBat malvertising campaigns used two kinds of ad URLs. As observed in other malvertising campaigns, they were abusing URL/analytics shorteners which are ideal for cloaking. That practice enables a threat actor to use a ‘good’ or ‘bad’ destination URL based on their own defined parameters (time of day, IP address, user-agent, etc.).
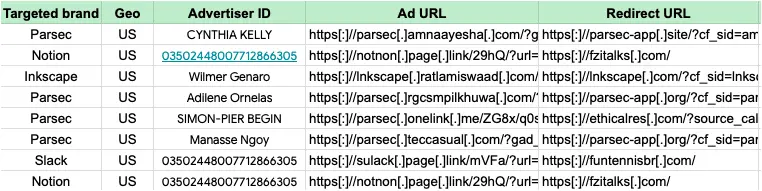
The other type of redirect was using subdomains from expired and sitting .com domains reassigned for malicious purposes. This is a common trick to give the illusion of credibility. However, in the most recent malvertising campaigns we see the threat actor abusing legitimate websites that appear to have been compromised.
It’s worth noting that the few examples we found were all Argentinian-based (.ar TLD):
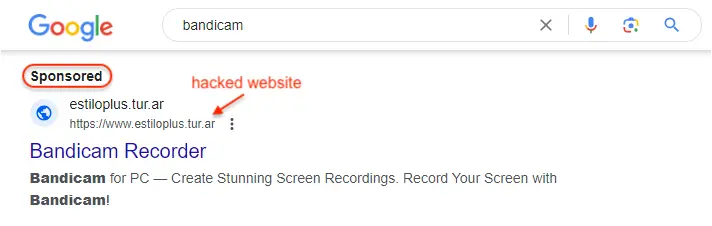
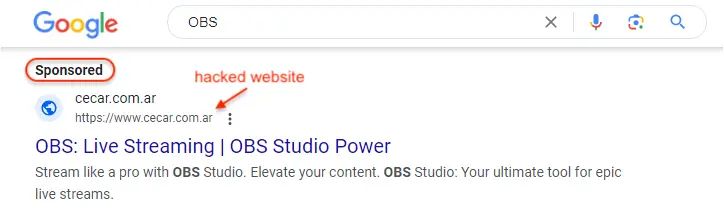


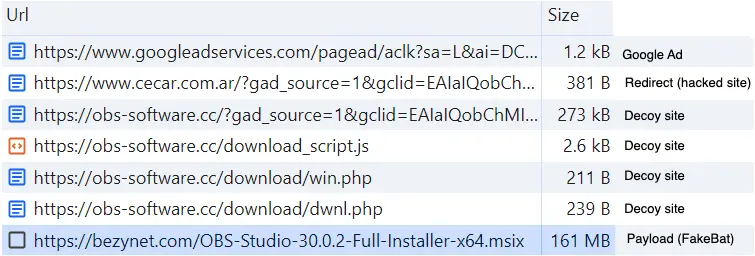
Victims click on the ad which sends a request to those hacked sites. Because the request contains the Google referer, the threat actor is able to serve a conditional redirect to their own malicious site:
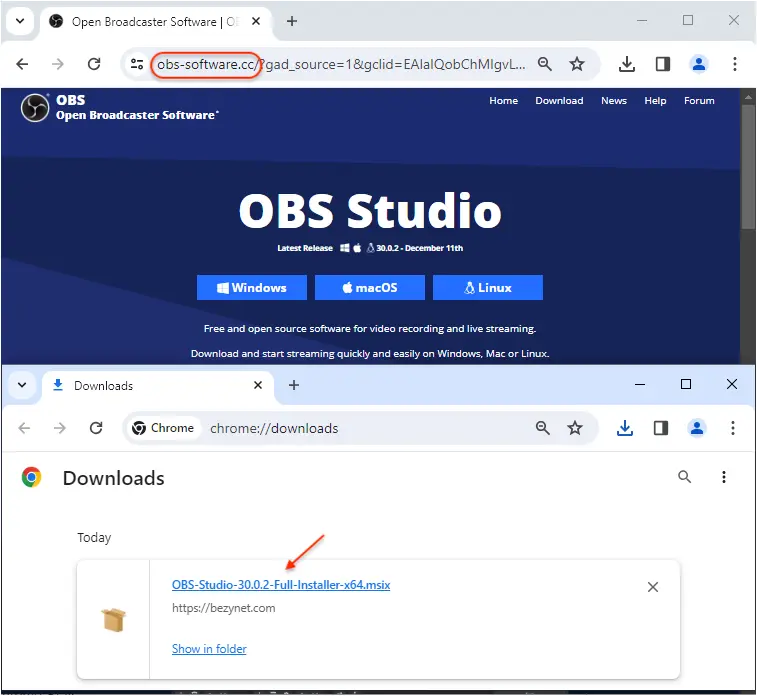
The full infection chain can be summarized in the web traffic image seen below:
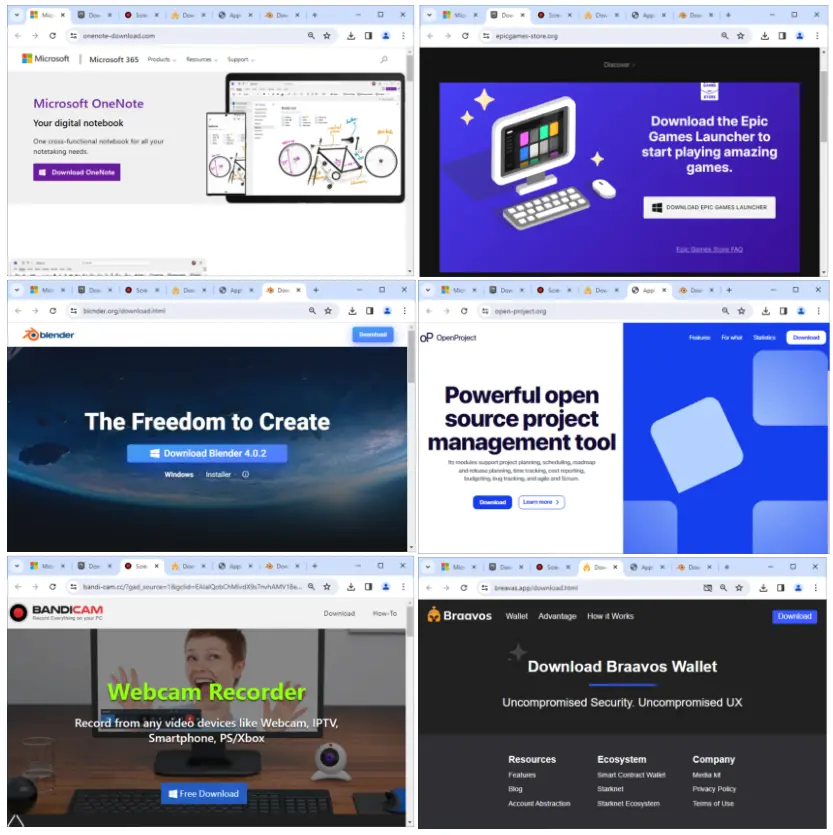
Several active brand impersonations
There are currently several campaigns running including OneNote, Epic Games, Ginger and even the Braavos smart wallet application. A number of those malicious domains can be found on Russian-based hoster DataLine (78.24.180[.]93).
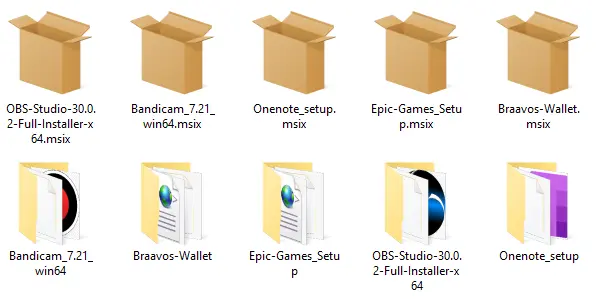
Each downloaded file is an MSIX installer signed with a valid digital certificate (Consoneai Ltd).
Once extracted, each installer contains more or less the same files with a particular PowerShell script:
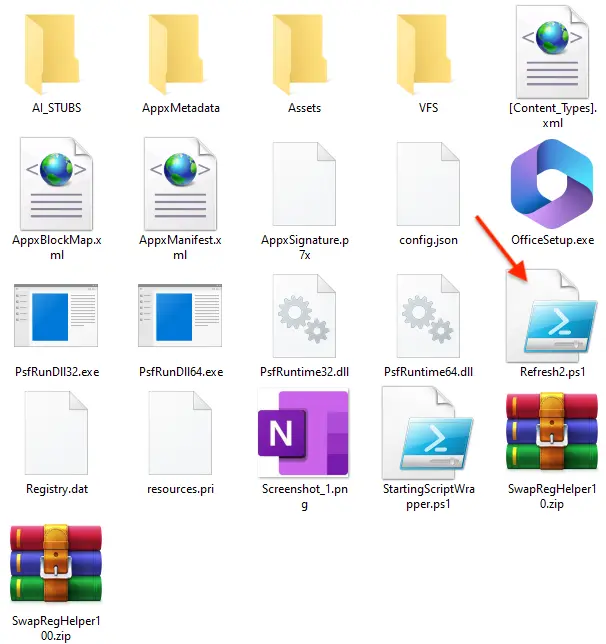
When the installer is ran, this PowerShell script will execute and connect to the attacker’s command and control server. Victims of interest will be cataloged for further use. ThreatDown EDR detects the PowerShell execution and creates an alert:

Conclusion
FakeBat continues to be a threat to businesses via malicious ads for popular software downloads. The malware distributors are able to bypass Google’s security checks and redirect victims to deceiving websites.
It is as important to defend against the supporting infrastructure as the malware payloads. However, that is not always easy since legitimate websites may be used to defeat domain blocklists. As always, blocking ads at the source via system policies such as ThreatDown DNS Filter, remains one the most effective ways to stop malvertising attacks in their tracks.
Indicators of Compromise
Hacked sites
cecar[.]com[.]ar estiloplus[.]tur[.]ar disenoymas[.]com[.]ar barcala[.]com[.]ar elchubutense[.]com[.]ar argentec[.]com[.]ar culturabritanicacba[.]org[.]ar starfirematafuegos[.]com[.]ar tecnologiaag[.]com[.]ar anelli[.]com[.]ar
Decoy sites
obs-software[.]cc bandi-cam[.]cc breavas[.]app open-project[.]org onenote-download[.]com epicgames-store[.]org blcnder[.]org trelconf[.]com trelconf[.]net noitons[.]net
Download URLs
bezynet[.]com/OBS-Studio-30[.]0[.]2-Full-Installer-x64[.]msix bezynet[.]com/Bandicam_7[.]21_win64[.]msix church-notes[.]com/Braavos-Wallet[.]msix church-notes[.]com/Epic-Games_Setup[.]msix church-notes[.]com/Onenote_setup[.]msix avr-energie[.]com/Trello-Full-Installer-x64.msix avr-energie.com/Notion%20Setup%203.2.1.msix
File hashes
07b0c5e7d77629d050d256fa270d21a152b6ef8409f08ecc47899253aff78029 0d906e43ddf453fd55c56ccd6132363ef4d66e809d5d8a38edea7622482c1a7a 15ce7b4e6decad4b78fe6727d97692a8f5fd13d808da18cb9d4ce51801498ad8 40c9b735d720eeb83c85aae8afe0cc136dd4a4ce770022a221f85164a5ff14e5 f7fbf33708b385d27469d925ca1b6c93b2c2ef680bc4096657a1f9a30e4b5d18 d6a6b73c273c508417898c02a142c496158ad2d0432495bff3a4f94f574d5bc4 b2e8277064af7791a3a73479ff2f2c45be3591c96567addb9421faed3dc7e2be
Command and control servers
62.204.41[.]98 ads-pill[.]xyz ads-pill[.]top ads-tooth[.]top ads-tooth[.]xyz ads-analyze[.]top ads-analyze[.]xyz ads-analyze[.]site ads-eagle[.]xyz ads-eagle[.]top ads-hoop[.]top ads-hoop[.]xyz ads-creep[.]xyz ads-creep[.]top ads-moon[.]top ads-moon[.]xyz ads-work[.]top ads-work[.]site ads-work[.]xyz ads-star[.]top ads-star[.]xyz ads-star[.]online ads-star[.]site ads-strong[.]site ads-strong[.]online ads-strong[.]top ads-strong[.]xyz ads-change[.]online ads-change[.]top ads-change[.]xyz ads-change[.]site
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


