Google Spyware Vendors Behind 50 Percent Of Zero Days Exploited In 2023

Google’s Threat Analysis Group (TAG) and Google subsidiary Mandiant said they’ve observed a significant increase in the number of zero-day vulnerabilities exploited in attacks in 2023, many of them linked to spyware vendors and their clients.
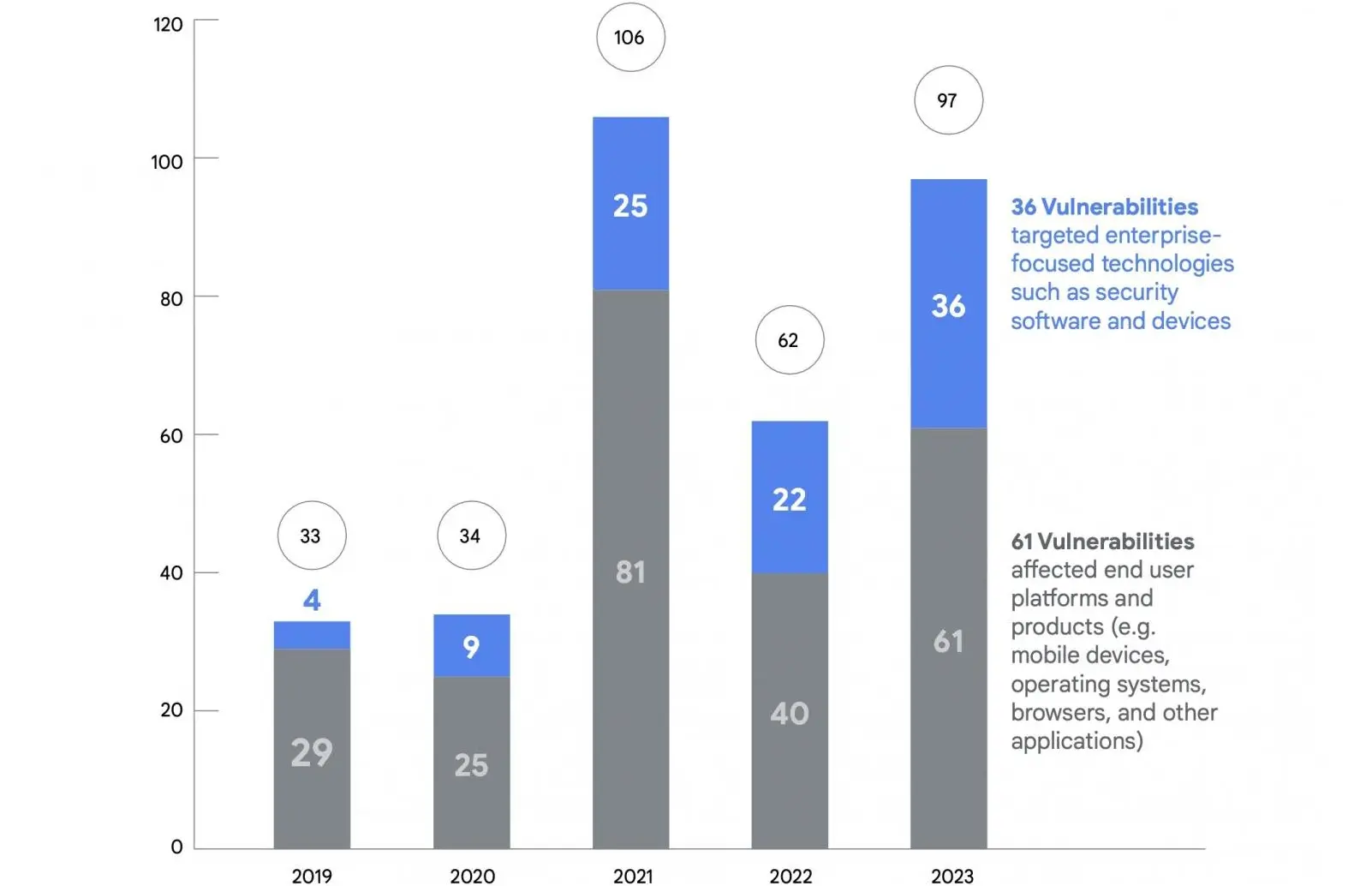
Last year’s count reached 97 zero-days exploited in attacks, representing a surge of over 50 percent compared to the previous year’s 62 vulnerabilities. Despite this rise, the figure remains below the peak of 106 zero-day bugs exploited in 2021.
Mandiant and TAG collectively discovered 29 instances out of 97 vulnerabilities, with 61 affecting end-user platforms and products (including mobile devices, operating systems, browsers, and various other apps).
The remaining 36 vulnerabilities were used to target enterprise-focused technologies such as security software and devices.
“On the enterprise side, we see a wider variety of vendors and products targeted, and an increase in enterprise-specific technologies being exploited,” Google warned [PDF].
“Over the years we’ve learned that the quicker we discover and patch attackers’ bugs, the shorter the lifespan of the exploit, and the more it costs attackers to maintain their capabilities.”
Last year, financially motivated actors used ten zero-day vulnerabilities, less than what was observed in 2022. Among these, the FIN11 threat group exploited three separate zero-day vulnerabilities, while at least four ransomware groups exploited another four zero-days.
China was linked to the most government-backed attacks, with Chinese cyber espionage groups exploiting 12 zero-day vulnerabilities in 2023, a notable increase from seven in 2022 and a trend observed in recent years.
Spyware behind 50% of all zero-days exploited in 2023
However, in 2023, commercial surveillance vendors (CSVs) were behind most zero-day exploits targeting Google products and Android ecosystem devices.
They were responsible for 75% of known zero-day exploits targeting these platforms (13 out of 17 vulnerabilities). Additionally, these vendors were linked to 48 zero-day exploits exploited in attacks last year, amounting to roughly 50% of all such flaws used in the wild in 2023.
Lastly, of the 37 zero-day vulnerabilities in browsers and mobile devices exploited in 2023, Google linked over 60% to CSVs that sell spyware capabilities to government customers.
“Ultimately, CSVs, and their government customers using these capabilities, conducted half of attributed zero-day exploitation by government actors in 2023 (24 of 48 vulnerabilities),” Google said.
“Private sector firms have been involved in discovering and selling exploits for many years, but we have observed a notable increase in exploitation driven by these actors over the past several years.”
In February, Google disclosed that most of the zero-day vulnerabilities discovered by its TAG group last year were traced back to mercenary spyware makers.
The company also associated spyware vendors with 35 out of 72 known zero-day exploits used in the wild over the past decade.
Some spyware vendors highlighted in Google’s February report include:
- Cy4Gate and RCS Lab: Italian maker of the Epeius and Hermit spyware for Android and iOS.
- Intellexa: Alliance of spyware firms led by Tal Dilian that combines technologies like Cytrox’s “Predator” spyware and WiSpear’s WiFi interception tools.
- Negg Group: Italian CSV with international reach known for Skygofree malware and VBiss spyware targeting mobile users via exploit chains.
- NSO Group: Israeli firm behind the Pegasus spyware and other commercial espionage tools.
- Variston: Spanish spyware maker linked to the Heliconia framework and known for working with other surveillance vendors on zero-day exploits.
To defend against zero-day attacks, Google advised high-risk users to enable the Memory Tagging Extension (MTE) on Pixel 8 devices and Lockdown mode on iPhone smartphones.
The company also recommended Chrome high-risk users to toggle on “HTTPS-First Mode” and disable the v8 Optimizer to get rid of potential security vulnerabilities to eliminate potential security vulnerabilities introduced by JIT (Just-in-Time) compilation which could enable attackers to manipulate data or inject malicious code.
Additionally, Google has suggested that high-risk users enroll in its Advanced Protection Program (APP), which provides enhanced account security and built-in defenses designed to protect against state-backed attackers.
The Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned Predator spyware operators Cytrox, Intellexa, Thalestris, and the Intellexa Consortium’s Israeli founder, Tal Jonathan Dilian, earlier this month.
In February, the U.S. State Department also announced a new visa restriction policy targeting individuals linked to commercial spyware, which will prohibit them from entering the United States.
