Mandiants X Account Hacked By Crypto Drainer As A Service Gang

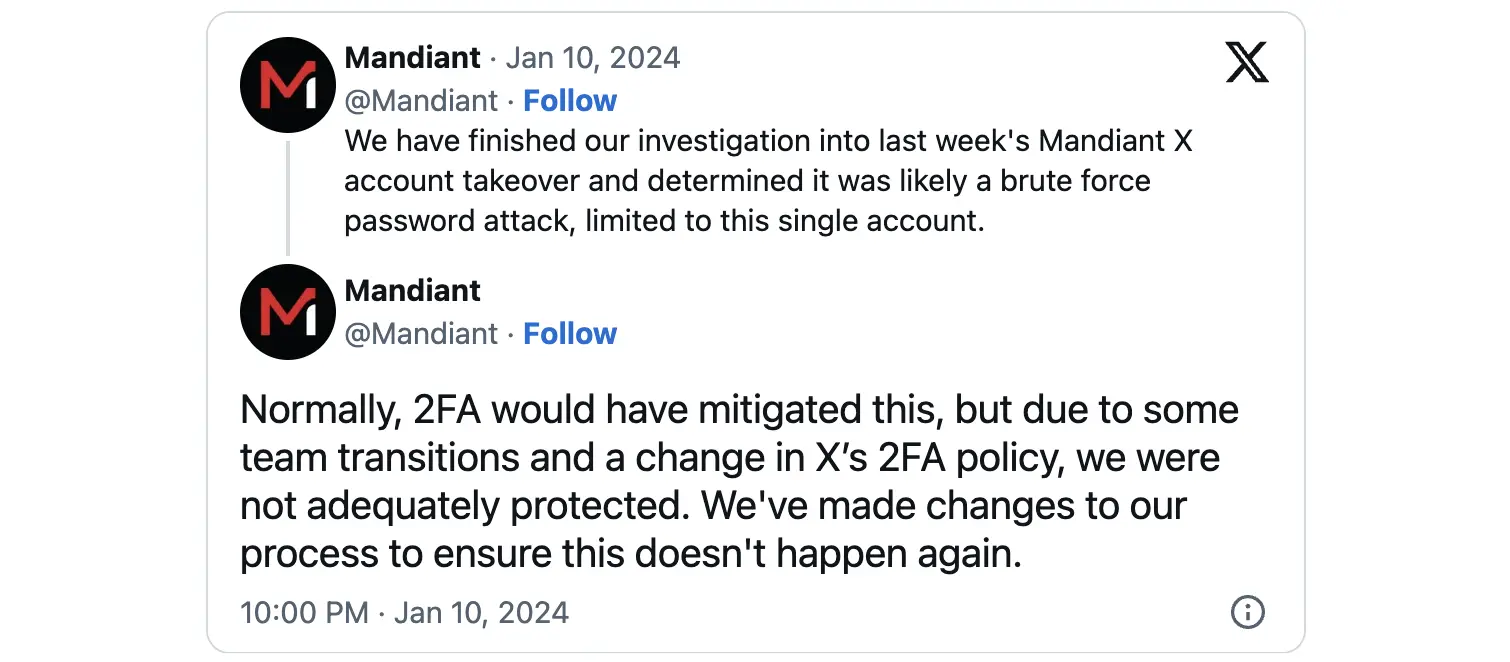
Cybersecurity firm and Google subsidiary Mandiant says its Twitter/X account was hijacked last week by a Drainer-as-a-Service (DaaS) gang in what it described as “likely a brute force password attack.”
“Normally, 2FA would have mitigated this, but due to some team transitions and a change in X’s 2FA policy, we were not adequately protected. We’ve made changes to our process to ensure this doesn’t happen again,” the company said.
The threat actor who took over Mandiant’s X social media account used it to share links, redirecting the company’s over 123,000 followers to a phishing page to steal cryptocurrency.
“Working with X, we were able to regain control of the account and, based on our investigation over the following days, we found no evidence of malicious activity on, or compromise of, any Mandiant or Google Cloud systems that led to the compromise of this account,” the company added.
As Mandiant found during a follow-up investigation into the incident, the attacker used a wallet drainer dubbed CLINKSINK. This same drainer has been used since December to steal funds and tokens from users of Solana (SOL) cryptocurrency as part of a large-scale campaign involving at least 35 affiliate IDs linked to a shared drainer-as-a-service (DaaS).
The affiliates use drainer scripts to steal cryptocurrency and are expected to give the operators a 20% share of all stolen funds. They use hijacked X and Discord accounts to share cryptocurrency-themed phishing pages impersonating Phantom, DappRadar, and BONK with fake token airdrop themes.
Targets visiting these malicious pages are asked to link their crypto wallets to claim the token airdrop, allowing the malicious actors to siphon their funds if they authorize a transaction to the drainer service.
The estimated value of assets stolen in these recent attacks totals a minimum of $900,000, according to Mandiant.
“The identified campaigns included at least 35 affiliate IDs that are associated with a common drainer-as-a-service (DaaS), which uses CLINKSINK,” Mandiant said.
“The operator(s) of this DaaS provide the drainer scripts to affiliates in exchange for a percentage of the stolen funds, typically around 20%.”
X users under attack
Since the start of the year, a massive wave of account breaches has impacted X users, with verified organizations getting hacked to spread cryptocurrency scams and links to wallet drainers.
Yesterday, the X @SECGov social media account for the U.S. Securities and Exchange Commission was also compromised to post a fake announcement regarding the approval of Bitcoin ETFs (exchange-traded funds) on security exchanges, which led to Bitcoin prices briefly spiking.
X’s Safety team later said the takeover was due to the hijack of a phone number associated with the @SECGov account in a SIM-swapping attack. X also noted that the SEC’s account did not have two-factor authentication (2FA) enabled at the time the account was hacked.
Previously, the Netgear and Hyundai MEA X accounts were also hijacked to promote fake cryptocurrency sites pushing wallet drainers, with the X account of Web3 security firm CertiK getting hacked one week before for the same malicious goal.
Additionally, threat actors are increasingly taking over verified government and business X accounts with ‘gold’ and ‘grey’ checkmarks to give legitimacy to tweets redirecting users to cryptocurrency scams, phishing sites, and sites spreading crypto drainers.
X users are also under a ceaseless flood of malicious cryptocurrency ads leading to fake airdrops, various scams, and, of course, cryptocurrency and NFT drainers.
As ScamSniffer blockchain threat experts said in December, a single waller drainer known as ‘MS Drainer’ was used to steal roughly $59 million worth of cryptocurrency from 63,000 people in an X ad push between March and November.