Pro Ukraine Hackers Breach Russian Isp In Revenge For Kyivstar Attack

A pro-Ukraine hacktivist group named ‘Blackjack’ has claimed a cyberattack against Russian provider of internet services M9com as a direct response to the attack against Kyivstar mobile operator.
Kyivstar is Ukraine’s largest telecommunications service provider and its services were severely disrupted in mid-December by what was later revealed to be an attack from Russian hackers.
An investigation of the Security Service of Ukraine (SSU) revealed that the Russians initially breached Kyivstar in May last year and had been preparing for the attack in December that culminated with simultaneous wiping of thousands of virtual servers and computers.
Earlier this week, the Blackjack hacker group announced on Telegram that they had breached M9com, a major internet service provider (ISP) in Moscow.
The hacktivists claimed that they not only managed to disrupt M9com’s internet services but also stole confidential data from the company.
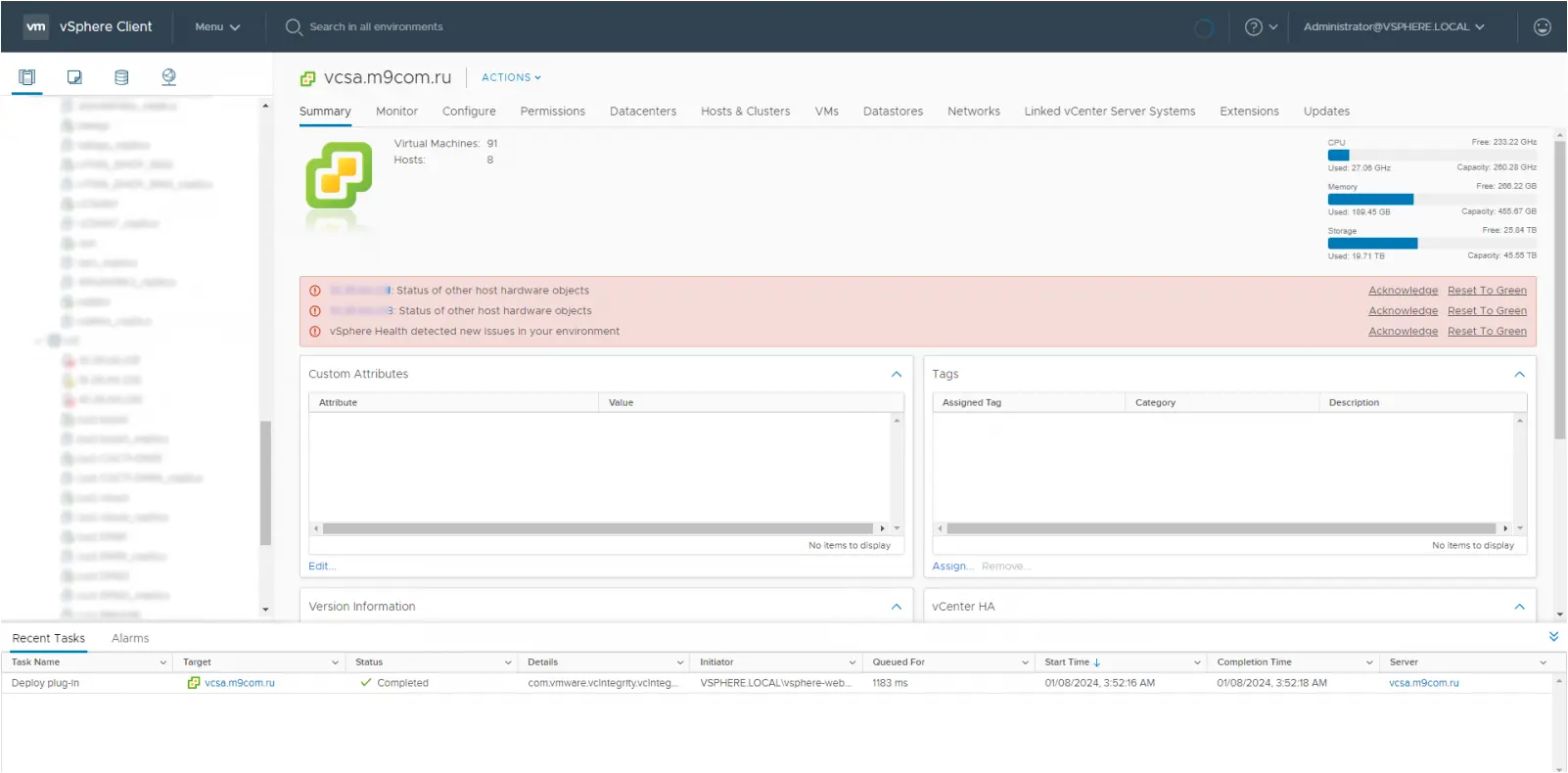
The group shared a Tor URL for three ZIP archives with images that allegedly prove their access to M9com’s systems, texts with account credentials of employees and customers, and 50GB of call data.
Several screenshots show FTP command execution to delete server files, wiping of data from a backup device, removal of configuration files, the RIPE database and billing portal, a snapshot of the vSphere client, and the dashboard for the Resource Public Key Infrastructure (RPKI).
Some of the leaked text files contain full names, usernames, email addresses, passwords in cleartext form, and other confidential details.
BleepingComputer reached out to M9com with a request to comment on the authenticity and validity of the leaked information but we received no answer at publishing time.
It appears that Blackjack also defaced M9com’s official website.
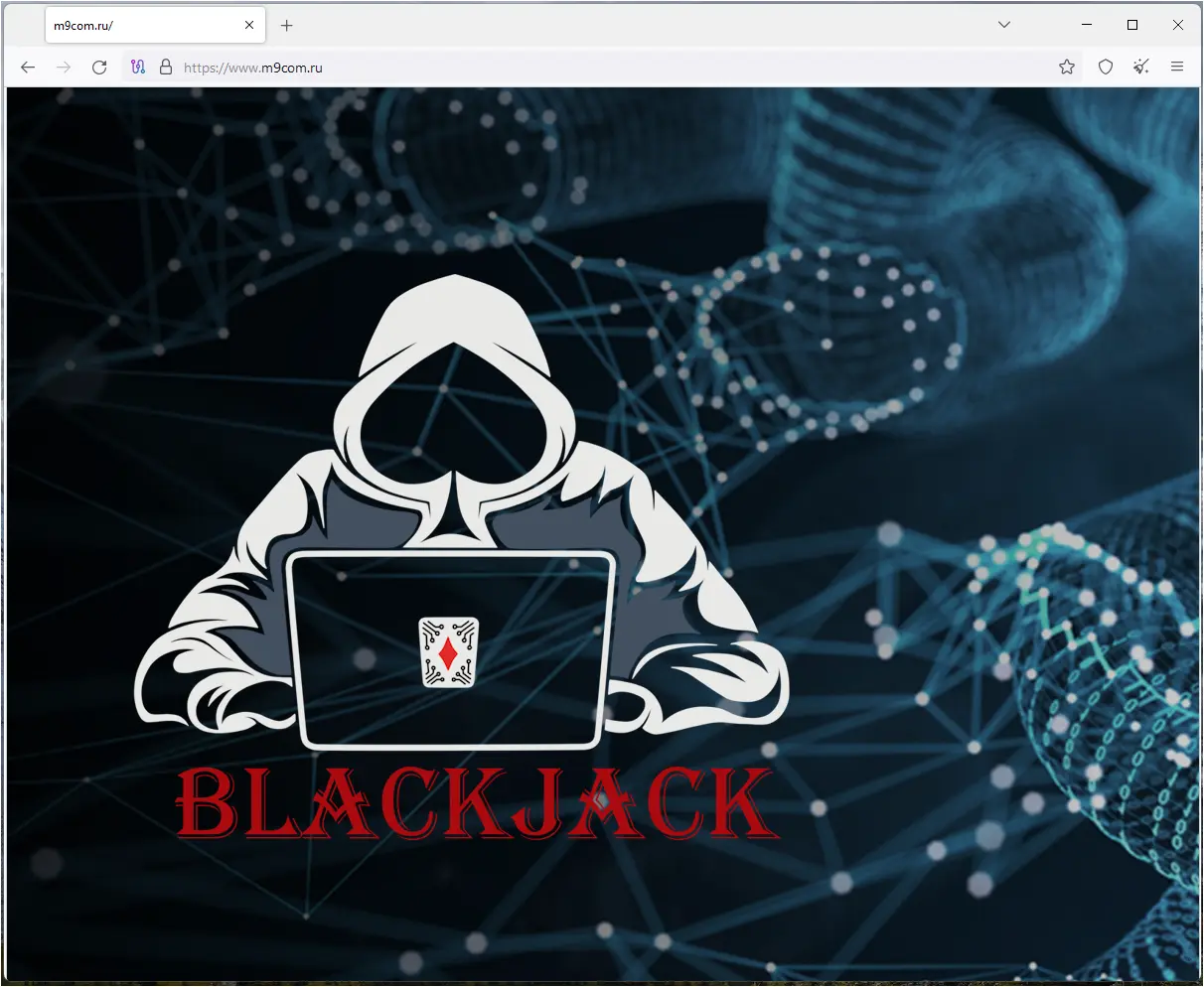
In a public message, Blackjack promises this to be just the first of a barrage of attacks they are planning in response to the Kyivstar hack.
While many pro-Russian hacktivist attacks are typically aiming to take down services (distributed denial-of-service), the Blackjack group’s activity has a greater impact as recovery from wiped servers is more difficult, especially if backups have also been destroyed.
According to Ukrinform citing “a source from Ukraine’s law enforcement agencies,” the Blackjack group is “likely related to the SBU” (the Security Service of Ukraine) and they deleted around 20 terabytes of data during the attack.
