Metasploit Tips and Tricks for HaXmas 2020

For this year’s HaXmas, we’re giving the gift of Metasploit knowledge! We’ll cover a mix of old, new, or recently improved features that you can incorporate into your workflows. Some of our readers may already know these tips and tricks for using Metasploit, but for the others who aren’t aware of them, it’s your lucky day!
Debugging failed HTTP Modules
There’s nothing more upsetting than not getting a Meterpreter session due to the misconfiguration of module options. I have found that the quickest way to sanity-check failed HTTP Modules is to set the HTTPTrace option to true before running your module:
set HTTPTrace true
This will enable the logging of raw HTTP requests and responses:
msf6 > use scanner/http/title
msf6 auxiliary(scanner/http/title) > set RHOSTS 127.0.0.1
RHOSTS => 127.0.0.1
msf6 auxiliary(scanner/http/title) > set HttpTrace true
HttpTrace => true
msf6 auxiliary(scanner/http/title) > run
####################
# Request:
####################
GET / HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
####################
# Response:
####################
HTTP/1.0 200 OK
Server: SimpleHTTP/0.6 Python/2.7.16
Date: Wed, 16 Dec 2020 01:16:32 GMT
Content-type: text/html; charset=utf-8
Content-Length: 178
<!DOCTYPE html PUBLIC “-//W3C//DTD HTML 3.2 Final//EN”><html>
<title>Directory listing for /</title>
<body>
<h2>Directory listing for /</h2>
<hr>
<ul>
</ul>
<hr>
</body>
</html>
[+] [127.0.0.1:80] [C:200] [R:] [S:SimpleHTTP/0.6 Python/2.7.16] Directory listing for /
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/title) >
This is a great way to quickly see why your modules have failed. In some scenarios, you may find that you’ve simply forgotten to specify the TARGETURI or VHOST options correctly, and after rerunning the module, you might even have a session.
Inline run options
Did you know that you can inline Metasploit’s options when running a module? When paired with your terminal’s reverse-i-search ctrl+r capabilities, it can be a real time-saver when wanting to rerun Metasploit modules again with the same options:
msf6 > use scanner/http/title
msf6 auxiliary(scanner/http/title) > run RHOSTS=127.0.0.1
[+] [127.0.0.1:80] [C:200] [R:] [S:SimpleHTTP/0.6 Python/2.7.16] Directory listing for /
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/title) >
Providing inlined options can also be useful for quickly enabling the HttpTrace functionality or verbose mode of a module:
msf6 auxiliary(scanner/http/title) > run HttpTrace=true VERBOSE=true
####################
# Request:
####################
GET / HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
####################
# Response:
####################
HTTP/1.0 200 OK
Server: SimpleHTTP/0.6 Python/2.7.16
Date: Wed, 16 Dec 2020 01:16:32 GMT
Content-type: text/html; charset=utf-8
Content-Length: 178
<!DOCTYPE html PUBLIC “-//W3C//DTD HTML 3.2 Final//EN”><html>
<title>Directory listing for /</title>
<body>
<h2>Directory listing for /</h2>
<hr>
<ul>
</ul>
<hr>
</body>
</html>
[+] [127.0.0.1:80] [C:200] [R:] [S:SimpleHTTP/0.6 Python/2.7.16] Directory listing for /
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/title) >
This year, we improved on these capabilities even further, thanks to this pull request. Metasploit now supports tab completion for both option names and values, too! Just use the tab key on your keyboard and you’ll be good to go:
set <tab><tab>
set RHOSTS=<tab><tab>
Note that this is a lesser-used piece of Metasploit’s functionality, so if you run into any issues, be sure to create an issue and send the details our way.
Quickly interacting with new sessions
Metasploit provides support for quickling interacting with the most recently created session by using a session ID of -1, for instance:
msf6 > sessions -i -1
[*] Starting interaction with 4…
Note that this trick also works when running post modules:
use modules/post/multi/manage/screenshare
set SESSION -1
set SRVHOST vmnet8
set URIPATH /
run
But wait, there’s more! Thanks to this pull request a few years ago, you can save additional characters by omitting the -i flag when you want to interact with a session:
msf6 > sessions -1
[*] Starting interaction with 4…
meterpreter > sessions 1
[*] Backgrounding session 4..
[*] Starting interaction with 1…
Skipping msfvenom’s boot time
Name a more iconic duo than msfvenom and exploit/multi/handler. I’ll wait.
In the meantime, though, did you know that you can generate payloads and create handlers without even leaving the Metasploit console? Just open up Metasploit and run through the payload generation and handler creation steps directly from the payload module:
# Use the payload module:
use windows/meterpreter/reverse_https
set LHOST 127.0.0.1
set LPORT 4443
set SessionCommunicationTimeout 0
set ExitOnSession false
# Create the executable, as an alternative to msfvenom:
generate -o reverse_windows.exe -f exe
# Create a handler, as an alternative to exploit/multi/handler
to_handler
We’ve found that this workflow can be faster in comparison to using msfvenom directly, which can be slow in comparison to a warmed-up Metasploit console.
Resource scripts
Resource scripts are great for streamlining your repetitive workflows. For instance, if we wanted to turn the above workflow of “using a module, generating a particular payload, and creating a handler” into a reusable resource script, simply create a file my_workflow.rc with the commands that you’d like to run:
➜ cat my_workflow.rc
use windows/meterpreter/reverse_https
set LHOST 127.0.0.1
set LPORT 4443
set SessionCommunicationTimeout 0
set ExitOnSession false
generate -o reverse_windows.exe -f exe
to_handler
Running a resource file from the command line is simple—just use the resource command. Metasploit will load this file, then execute each line one at time:
msf6 > resource /example/my_workflow.rc
[*] Processing /example/my_workflow.rc for ERB directives.
resource (/example/my_workflow.rc)> use windows/meterpreter/reverse_https
resource (/example/my_workflow.rc)> set LHOST 127.0.0.1
LHOST => 127.0.0.1
resource (/example/my_workflow.rc)> set LPORT 4443
LPORT => 4443
resource (/example/my_workflow.rc)> set SessionCommunicationTimeout 0
SessionCommunicationTimeout => 0
resource (/example/my_workflow.rc)> set ExitOnSession false
ExitOnSession => false
resource (/example/my_workflow.rc)> generate -o reverse_windows.exe -f exe
[*] Writing 73802 bytes to reverse_windows.exe…
resource (/example/my_workflow.rc)> to_handler
[*] Payload Handler Started as Job 2
By default Metasploit will run any resource scripts found within its config directory at ~/.msf4/msfconsole.rc, or you can even specify resource scripts to be run when msfconsole starts up. This can be useful for setting options such as global logging, or default LHOST values:
msfconsole -r /example/my_workflow.rc
Writing resource scripts can sometimes be a chore, which is why Metasploit also provides the ability to save recently executed commands directly to a specified resource script location:
# Viewing the makerc command usage:
msf6 > help makerc
Usage: makerc <output rc file>
Save the commands executed since startup to the specified file.
# Saving the last commands to reusable resource script:
msf6 > makerc example.rc
[*] Saving last 4 commands to examplerc …
For the power users of Metasploit, resource scripts also support the ability to run arbitrary Ruby code. This functionality makes it possible to interact directly with Metasploit’s Framework object programmatically:
use windows/meterpreter/reverse_https
<ruby>
# Run arbitrary ruby code which can interact with the Metasploit framework object
puts “Currently running with Metasploit version: #{framework.version}!”
</ruby>
If you didn’t know, there’s also a treasure trove of hidden resource scripts buried deep within Metasploit Framework repository that you may not be aware of: https://github.com/rapid7/metasploit-framework/tree/master/scripts/resource.
Refining search results
This year, we made improvements to the search functionality of Metasploit. Specifying additional search terms will now continue to refine your search results.
Previously, when using the command search postgresql login, all modules matching either postgresql or login would be returned:
msf6 > search postgresql login
Matching Modules
================
# Name Disclosure Date Rank Check Description
– —- ————— —- —– ———–
0 auxiliary/admin/appletv/appletv_display_image normal No Apple TV Image Remote Control
1 auxiliary/admin/appletv/appletv_display_video normal No Apple TV Video Remote Control
… many modules later …
248 post/windows/manage/sticky_keys normal No Sticky Keys Persistance Module
249 post/windows/manage/wdigest_caching normal No Windows Post Manage WDigest Credential Caching
Interact with a module by name or index, for example use 249 or use post/windows/manage/wdigest_caching
Now with the newly updated search command running search postgresql login – Metasploit will only return modules matching both postgresql and login:
msf6 > search postgresql login
Matching Modules
================
# Name Disclosure Date Rank Check Description
– —- ————— —- —– ———–
0 auxiliary/scanner/postgres/postgres_login normal No PostgreSQL Login Utility
Interact with a module by name or index, for example use 0 or use auxiliary/scanner/postgres/postgres_login
This functionality works well with the search keywords, too:
msf6 > search cve:2020 type:aux tomcat ghostcat
Matching Modules
================
# Name Disclosure Date Rank Check Description
– —- ————— —- —– ———–
0 auxiliary/admin/http/tomcat_ghostcat 2020-02-20 normal No Ghostcat
Interact with a module by name or index, for example use 0 or use auxiliary/admin/http/tomcat_ghostcat
Developing modules?
There are lots of great workflow capabilities built into Metasploit for our users, but there’s also a few useful tricks for developers!
Let’s start our journey with file reloading. It turns out that the best improvement to a developer’s productivity is the ability to reload files in Metasploit without having to close and reopen it. As a result, these commands will save you a lot of time:
reload: Reload the latest version of the active module from the file system.reload_lib -a: Reload any changed files that are in your current Git working tree, other than modules. This is perfect for changing core library files.reload_all: Reload all modules from all configured module paths.
There are also a few extra commands that you might find useful when modifying a developing a new Metasploit module:
rerun: After reloading the module the currently active module, run theruncommand.recheck: After reloading the currently active module, run thecheckcommand.edit: Edit the currently open module within your local editor. This can also edit arbitrary filesedit <file_path>.
Finally, placing a breakpoint in your code can be a great way to immediately get to the root cause of issues. Just place the following snippet wherever you wish to enter into an interactive debugging environment:
require ‘pry’; binding.pry
This will pause the execution of the currently running code code when the breakpoint is hit:
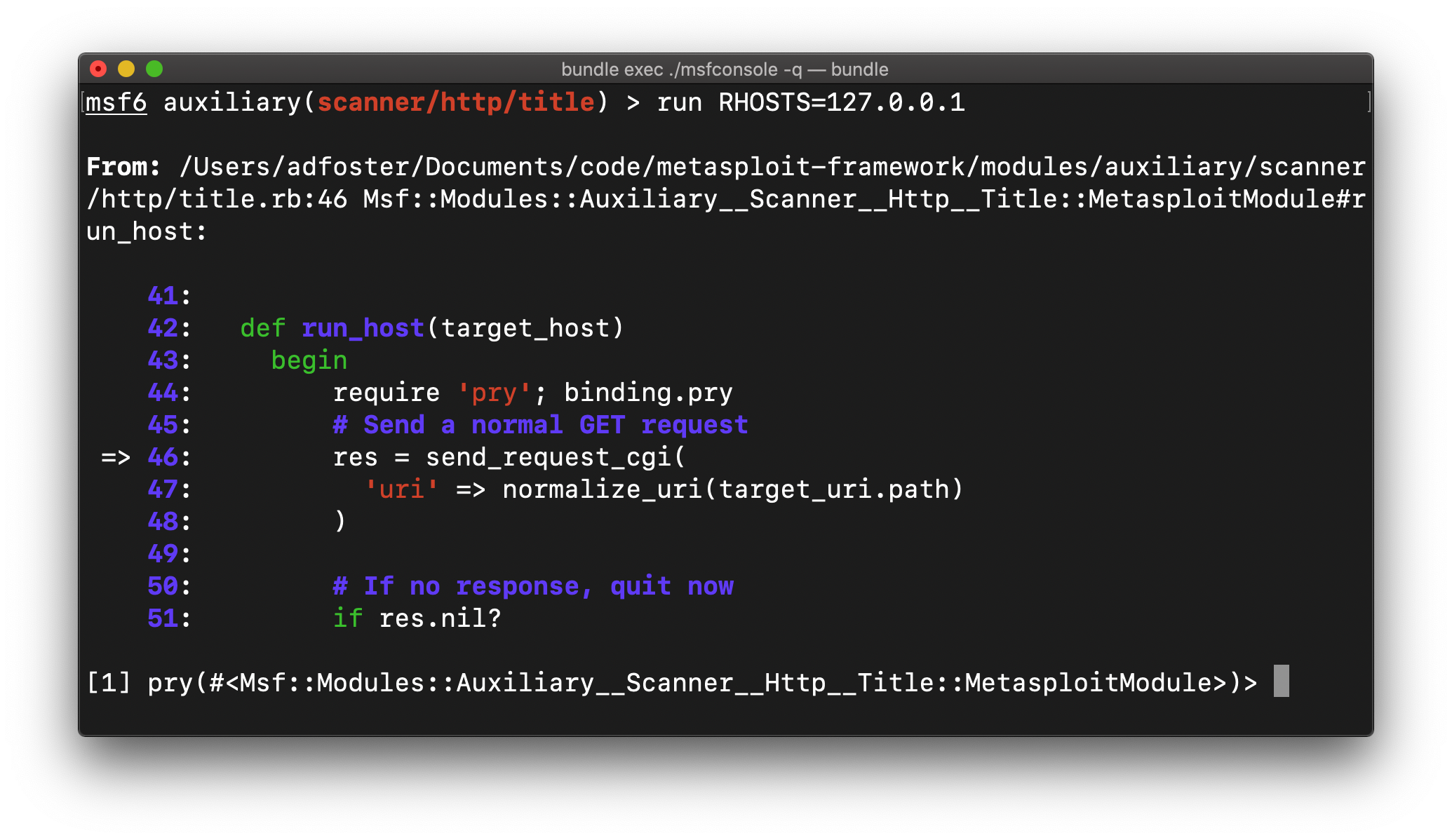
There are a lot of useful commands to help explore the issue from here, for instance:
backtrace: Show the current call stackup/down: Navigate the call stackstep: Move forward by a single execution stepnext: Move forward by a single linewhereami: Show the current breakpoint location againhelp: View all of the available commands and options
Ruby’s runtime introspection can also be great to help with debugging. This will help you explore the available methods, classes, and variables within the current Ruby environment:
self: To find out what the current object isself.methods: Find all available methodsself.methods.grep /send/: Searching for a particular method that you’re interested in. This can be great to explore unknown APIs.self.method(:connect).source_location: Find out which file, and which line, defined a particular methodself.class.ancestors: For complex modules, this can be useful to see what mixins a Metasploit module is currently using
Even more tips!
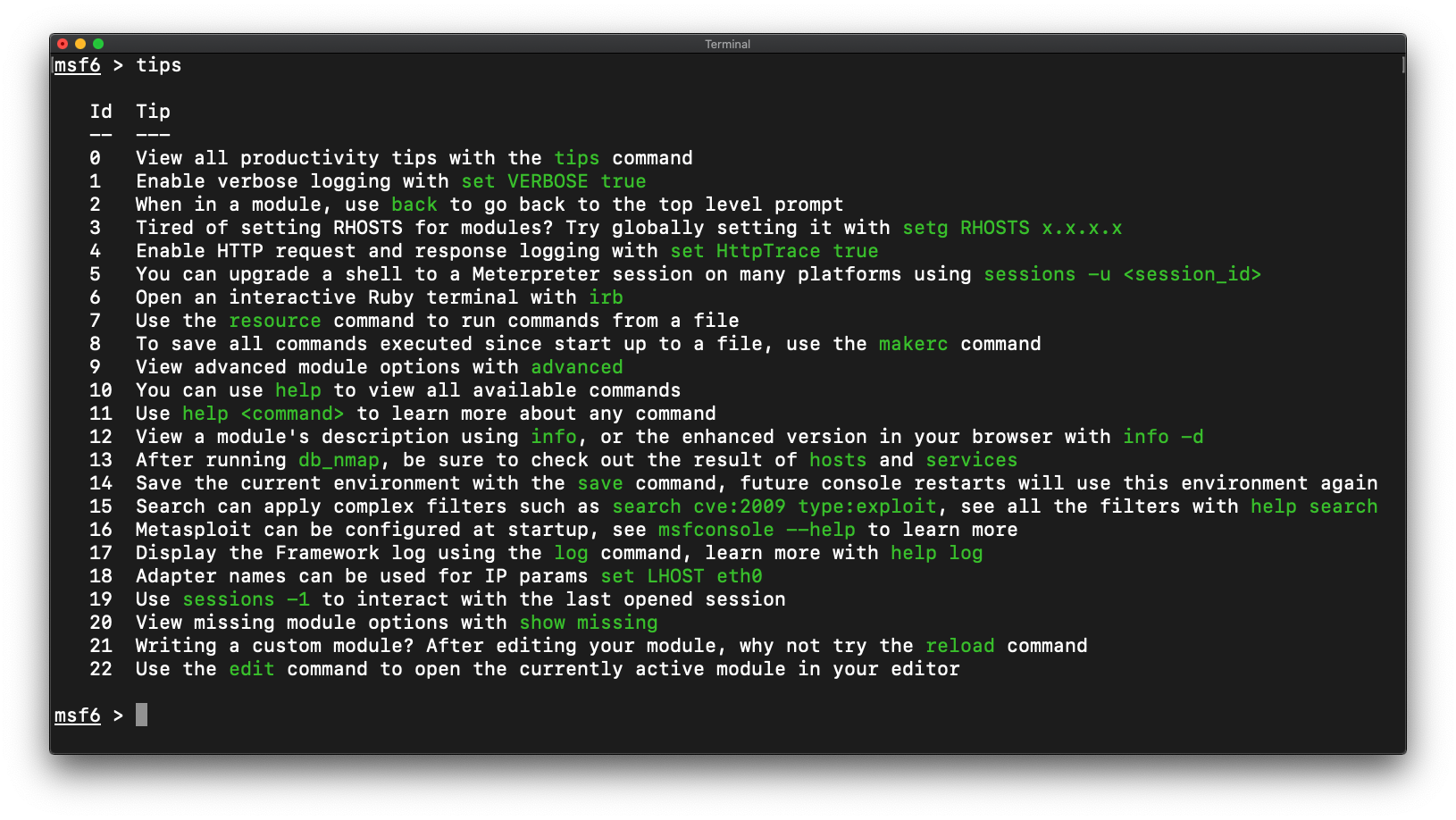
Did you know that the Metasploit console has an inbuilt tips command? It will show you even more useful workflow tips to check out! See any tips that we’re missing? Simply create a pull request to help us improve the list:
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Cobalt Strike Beacon Detected - 8[.]219[.]161[.]236:48899 5 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
