Ransomware Payments Drop To Record Low As Victims Refuse To Pay

The number of ransomware victims paying ransom demands has dropped to a record low of 29% in the final quarter of 2023, according to ransomware negotiation firm Coveware.
This trend became apparent in mid-2021 when the payment rate dropped to 46% after previously being 85% at the start of 2019.
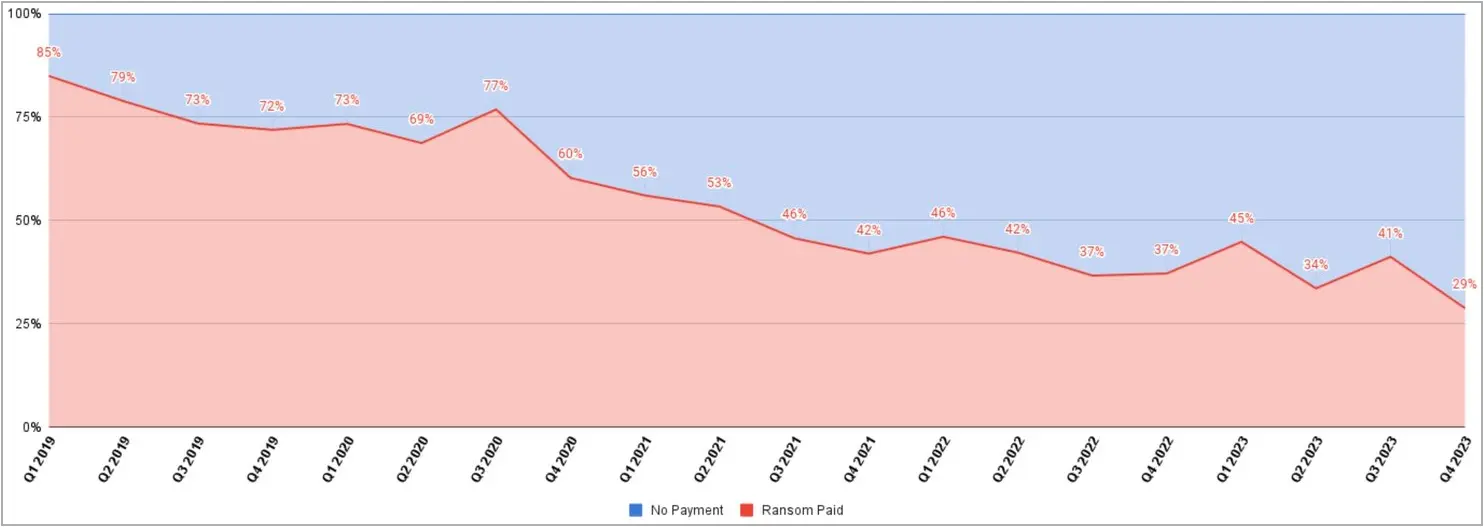
Source: Coveware
According to Coveware, the reason for this continual drop is multifaceted, including better preparedness by organizations, a lack of trust towards cybercriminals promising not to publish stolen data, and legal pressure in some regions where paying a ransom is illegal.
Coveware has found that even when data is stolen in cyberattacks, the payment rate was just 26% in the last quarter.
Not only have the number of victims paying ransomware dropped but also the dollar amounts of actual ransom payments.
Coveware says that ransom payments in Q4 2023 had an average amount of $568,705, a 33% drop from the previous quarter, while the median ransom payment was $200,000.
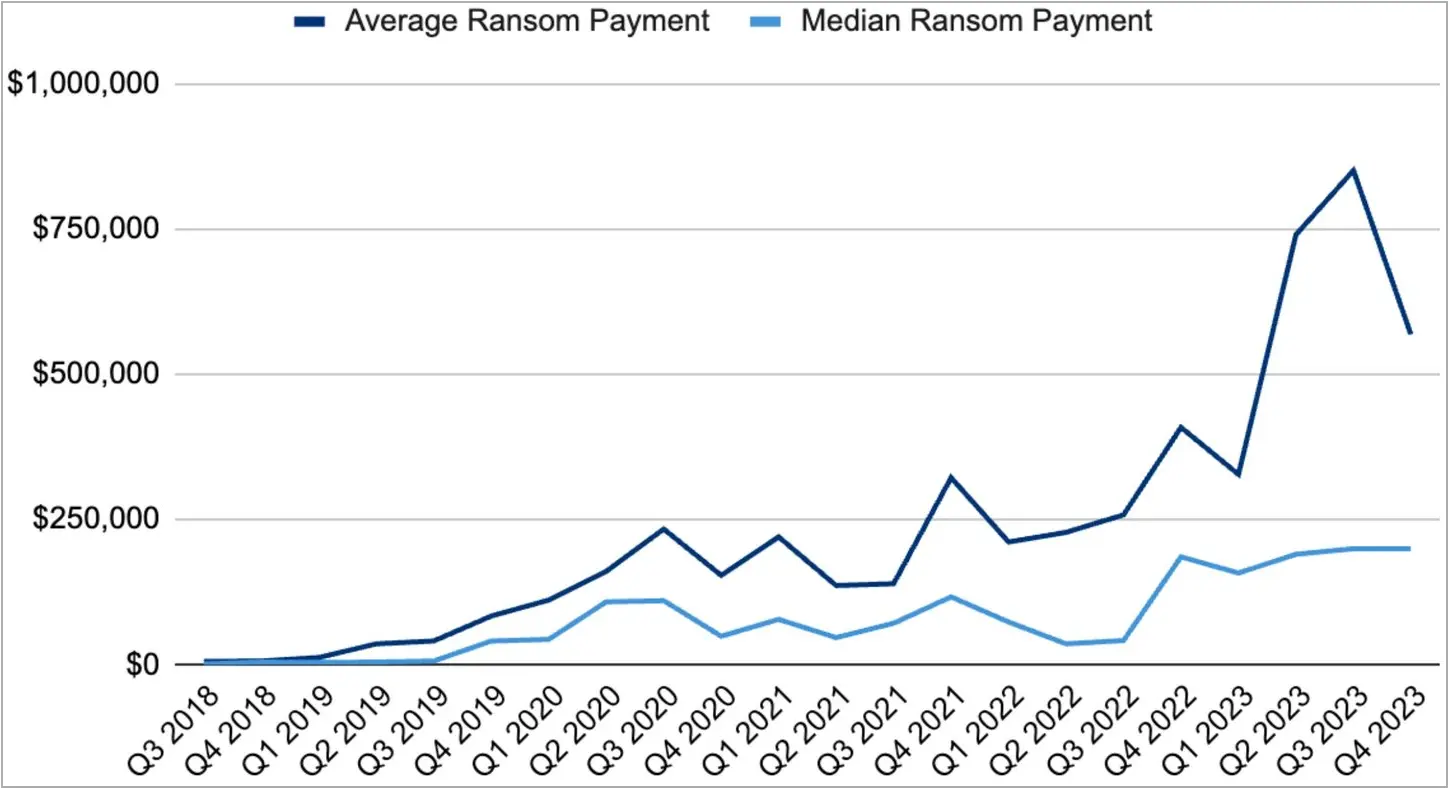
Source: Coveware
The median size of victimized organizations dropped in Q4 ’23, reversing a trend that started in Q2 ’22 when attackers anticipating a drop in payment rates opted to target larger companies for more significant payouts to make up the difference.
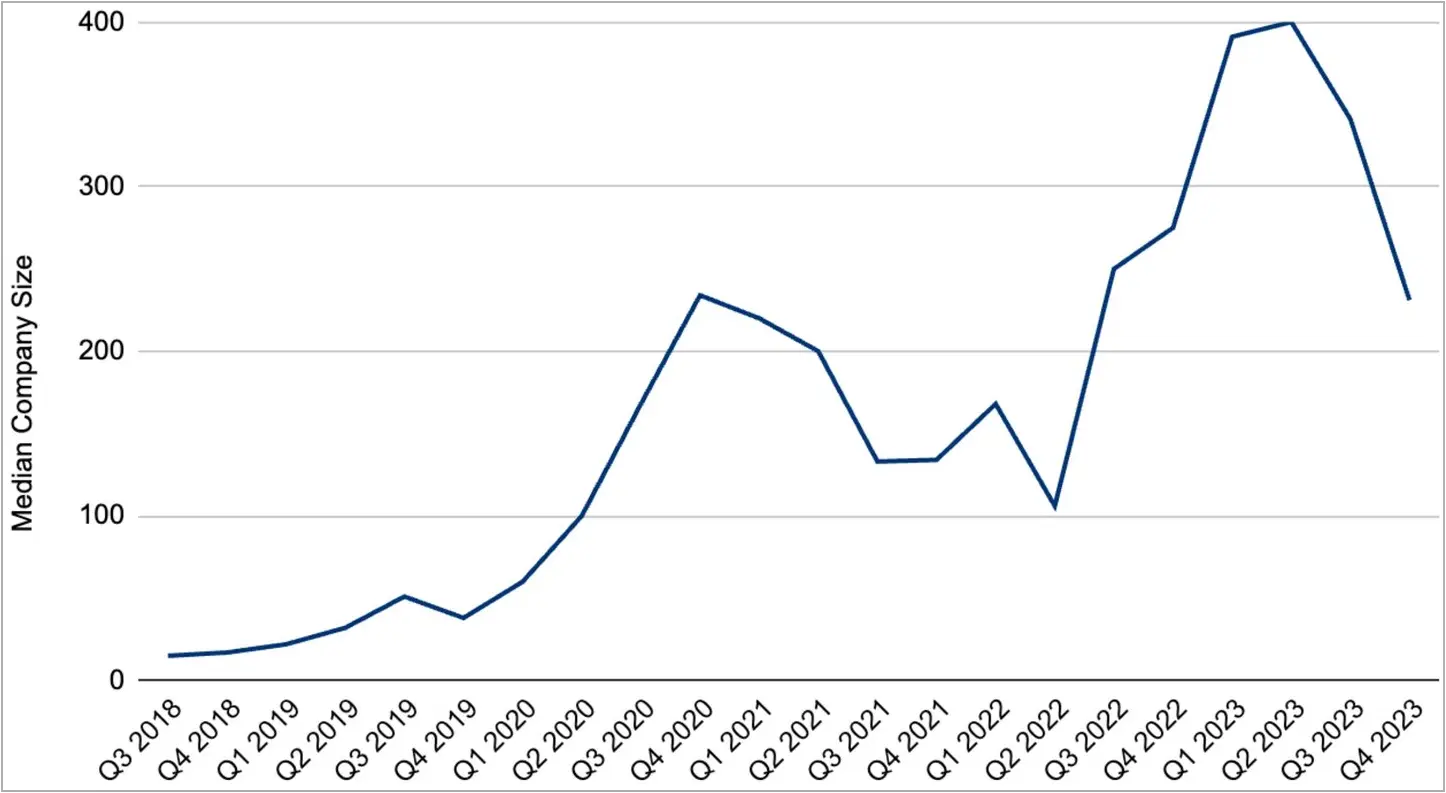
Source: Coveware
Banning ransom payments
Apart from the above stats, Coveware’s report touches on the controversial subject of ransom payment bans and how these could affect targeted organizations and the cybercrime community.
As the cybersecurity company elaborates, although bans seem like a good idea theoretically, they are far from straightforward in practice.
Coveware suggests that if national bans were imposed in the U.S. or other highly-targeted countries, companies would most likely stop reporting these incidents to the authorities and deal with their problem using shady service providers as intermediaries.
The firm forecasts that if such a law were enacted, a large illegal market would be created overnight, and all progress made in bringing victims and law enforcement agencies closer would be reversed.
“A substantial proportion of these victims would do the quick math on the risk (company badly damaged vs. risk of fines and penalties), and then proceed to navigate the illegal market of service providers,” reads Coveware’s report.
“Some companies would still report to be sure, but any victim that even contemplated paying or chose to pay would absolutely keep it quiet as they would be admitting to a crime if they reported.”
Coveware suggests instead to double down on some of the existing mechanisms and initiatives that make profiting from ransomware increasingly harder, including:
- Strengthen reporting frameworks and due diligence for ransom payments, encouraging detailed disclosure and decision-making frameworks.
- Offer safe harbors for proactive reporting and compliance, coupled with mandatory reporting requirements to foster cooperation with law enforcement.
- Impose significant fines for non-disclosure of incidents while avoiding personal liability for CISOs to maintain a secure talent pool.
- Emphasize long-term collaboration with law enforcement and define clear, long-term reporting obligations for effective investigations.
- Focus on strategic measures to reduce the attractiveness and ease of ransom payments, thereby diminishing the viability of ransomware as a profitable attack method.
Unfortunately, as we enter 2024, ransomware remains a major global cybersecurity challenge, demonstrating a remarkable resilience against existing solutions.
Despite this, the observed drop in ransom payment rates signifies a positive trend, indicating that the concerted efforts to combat this issue are steering the situation in the right direction.
