Cisa Orders Federal Agencies To Disconnect Ivanti Vpn Appliances By Saturday

CISA has ordered U.S. federal agencies to disconnect all Ivanti Connect Secure and Policy Secure VPN appliances vulnerable to multiple actively exploited bugs before Saturday.
This required action is part of a supplemental direction to this year’s first emergency directive (ED 24-01) issued last week that mandates Federal Civilian Executive Branch (FCEB) agencies to urgently secure all ICS and IPS devices on their network against two zero-day flaws in response to extensive exploitation in the wild by multiple threat actors.
Ivanti appliances are currently targeted in attacks chaining the CVE-2023-46805 authentication bypass and the CVE-2024-21887 command injection security flaws since December as zero-days.
The company also warned of a third actively exploited zero-day (a server-side request forgery vulnerability tracked as CVE-2024-21893), allowing threat actors to bypass authentication on vulnerable ICS, IPS, and ZTA gateways.
On Wednesday, Ivanti released security patches for some software versions affected by the three flaws, and it also provides mitigation instructions for devices still waiting for a patch or that can’t be secured immediately against ongoing attacks.
Yesterday, Ivanti urged customers to factory reset vulnerable appliances before patching to thwart attackers’ attempts to gain persistence on their network between software upgrades.
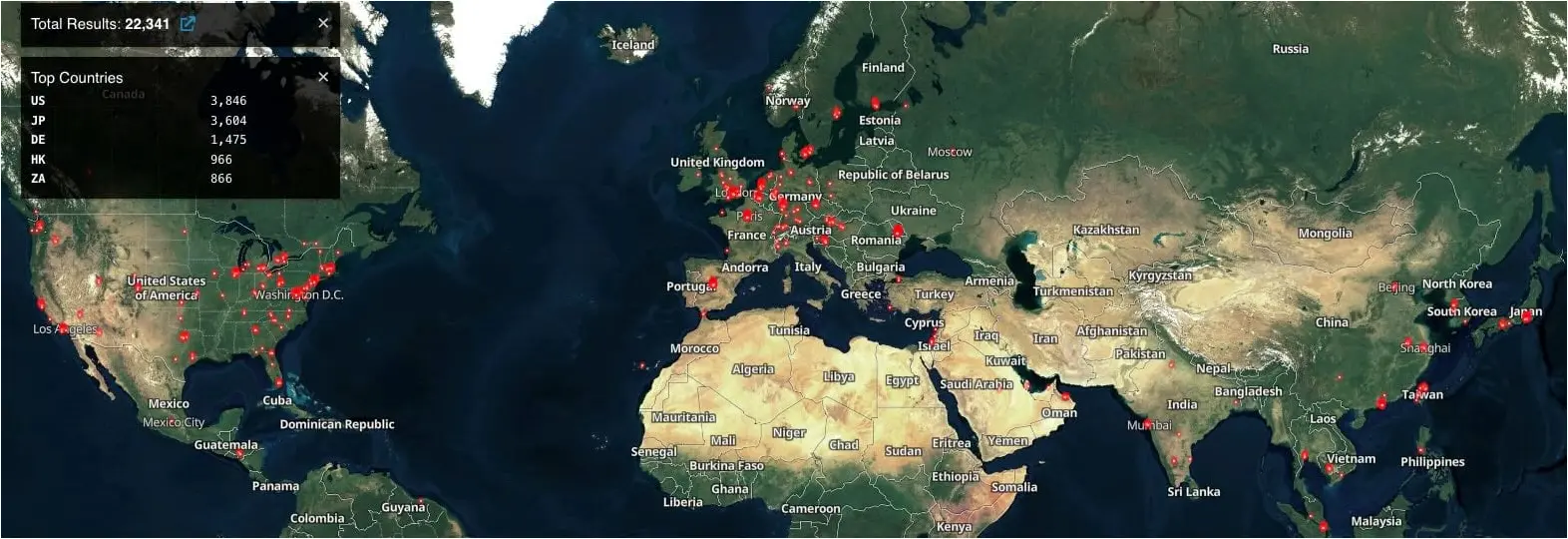
Shodan currently sees over 22,000 Ivanti ICS VPNs exposed online, while threat monitoring platform Shadowserver tracks more than 21,400.
Shadowserver also monitors the number of Ivanti VPN instances compromised worldwide daily, with almost 390 hacked devices discovered on January 31.
CISA: Disconnect all Ivanti VPNs by Saturday
In response to the “substantial threat” and significant risk of security breaches posed by compromised Ivanti VPN appliances, CISA now mandates all federal agencies to “disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure solution products from agency networks,” “as soon as possible” but no later than 11:59 PM on Friday, February 2.
After the devices are removed from the network, the agencies must also keep hunting for signs of compromise on systems linked to, or recently connected to, the disconnected Ivanti devices.
Furthermore, they must continue monitoring authentication or identity management services susceptible to exposure, isolating enterprise systems, and auditing privilege-level access accounts.
To bring the Ivanti appliances back online, the agencies must export their configuration, factory reset them, rebuild them using patched software versions, reimport the backed-up configs, and revoke all connected or exposed certificates, keys, and passwords.
In the next stage, federal agencies that had impacted Ivanti products on their networks should also assume that all linked domain accounts were compromised and disable joined/registered devices (in cloud environments) or perform a double password reset for all accounts and revoke Kerberos tickers and cloud tokens (in hybrid setups).
After each recovery stage, agencies must report their status across all required actions to CISA using a CyberScope template provided by the cybersecurity agency. They’ll also have to give updates on their progress upon CISA’s request or when all actions are complete.
“This Supplemental Direction remains in effect until CISA determines that all agencies operating affected software have performed all required actions from this Direction or the Direction is terminated through other appropriate action,” CISA said.
