Why ‘Never Expire’ Passwords Can Be a Risky Decision
Password resets can be frustrating for end users. Nobody likes being interrupted by the ‘time to change your password’ notification – and they like it even less when the new passwords they create are rejected by their organization’s password policy. IT teams share the pain, with resetting passwords via service desk tickets and support calls being an everyday burden. Despite this, it’s commonly accepted that all passwords should expire after a set period of time.
Why is this the case? Do you need password expiries at all? Explore the reason expiries exist and why setting passwords to ‘never expire’ might save some headaches, but not be the best idea for cybersecurity.
Why do we have password expiries?
The traditional 90-day password reset policy stems from the need to protect against brute-force attacks. Organizations typically store passwords as hashes, which are scrambled versions of the actual passwords created using cryptographic hash functions (CHFs). When a user enters their password, it’s hashed and compared to the stored hash. Attackers attempting to crack these passwords must guess the correct one by running potential passwords through the same hashing algorithm and comparing the results. The process can further be complicated for attackers by techniques like salting, where random strings are added to passwords before hashing.
Brute-force attacks depend on several factors, including the computational power available to the attacker and the strength of the password. The 90-day reset period was considered a balanced approach to outpace brute-force attacks while not burdening users with too frequent changes. Advances in technology, however, have reduced the time required to crack passwords, prompting a re-evaluation of this policy. Despite this, the 90-day expiry remains a recommendation in many compliance standards, including PCI.
Why have some organizations got rid of expiries?
One of the main arguments against regular password expiry is that it can lead to the reuse of weak passwords. Users often make slight changes to their existing passwords, such as changing ‘Password1!’ to ‘Password2!’. This practice undermines the security benefits of password changes. The real issue here though is not the act of resetting passwords but rather the organization’s policy that allows weak passwords in the first place.
The bigger reason organizations have opted for ‘never expire’ passwords is reducing IT and service desk burden. The cost and burden of password resets on IT help desks are significant. Gartner estimates that 20-50% of IT help desk calls are related to password resets, with each reset costing around $70 in labor according to Forrester. This adds up, especially when users frequently forget their passwords after being forced to create new ones.
Some organizations may therefore be tempted to force end users into creating one very strong password and then setting the passwords to ‘never expire’ in order to cut down on IT burden and reset costs.
What are the risks with ‘never expire’ passwords?
Having a strong password and never changing it might give someone a false sense of security. A strong password isn’t immune to threats; it can be vulnerable to phishing schemes, data breaches, or other types of cyber incidents without the user realizing it. The Specops Breached Password Report found 83% of passwords that were compromised met the regulatory standards for length and complexity.
An organization might have a strong password policy where every end user is forced to create a strong password that’s resistant to brute force attacks. But what happens if the employee decides to reuse their password for their Facebook, Netflix, and all other personal applications too? The risk of the password being compromised increases a lot, regardless of the internal security measures the organization has in place. A survey by LastPass found 91% of end users understood the risk of password reuse – but 59% did it anyway.
Another risk with ‘never expire’ passwords is that an attacker could use a set of compromised credentials for a long period of time. The Ponemon Institute found that it typically takes an organization about 207 days to identify a breach. While mandating password expiration could be beneficial here, it’s likely that an attacker would have already achieved their objectives by the time the password expires. Consequently, NIST and other guidelines advise organizations to only set passwords to never expire if they have mechanisms to identify compromised accounts.
How to detect compromised passwords
Organizations must adopt a comprehensive password strategy that goes beyond regular expiry. This includes guiding users to create strong passphrases of at least 15 characters. Such a policy can significantly reduce vulnerability to brute-force attacks. Encouraging end users to create longer passwords can also be achieved through length-based aging, where longer, stronger passwords are allowed to be used for extended periods before expiring. This approach eliminates the need for a one-size-fits-all expiry time, provided users adhere to the organization’s password policy.
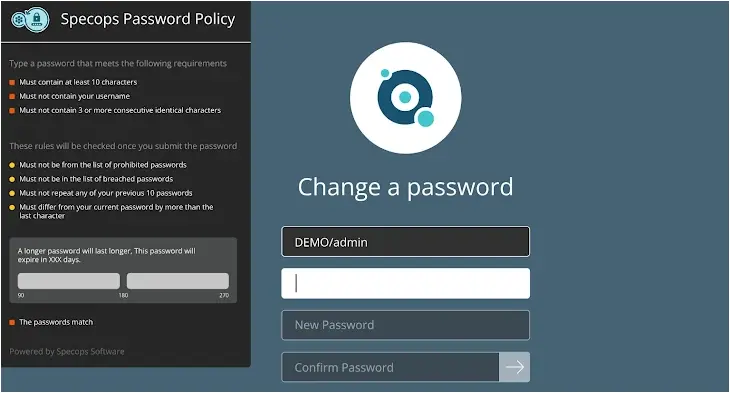 |
| Picture show with building stronger passwords and length-based ageing |
However, even strong passwords can be compromised and there need to be measures in place to detect this. As once compromised, the cracking time for a password in the bottom right of the above table turns to ‘instantly.’ Organizations need a joined-up strategy to make sure they are covering themselves against both weak and compromised passwords.
If you’re interested in managing all of the above in an automated way from a simple-to-use interface within Active Directory, Specops Password Policy could be a valuable tool in your cybersecurity armory. Through its Breached Password Protection service, Specops Password Policy can continuously check and block the use of more than 4 billion unique known compromised passwords. See for yourself with a live demo.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![Cobalt Strike Beacon Detected - 179[.]43[.]186[.]234:80 2 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
![[PLAY] - Ransomware Victim: All Book Covers 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)