Gophish Framework Used in Phishing Campaigns to Deploy Remote Access Trojans
Russian-speaking users have become the target of a new phishing campaign that leverages an open-source phishing toolkit called Gophish to deliver DarkCrystal RAT (aka DCRat) and a previously undocumented remote access trojan dubbed PowerRAT.
“The campaign involves modular infection chains that are either Maldoc or HTML-based infections and require the victim’s intervention to trigger the infection chain,” Cisco Talos researcher Chetan Raghuprasad said in a Tuesday analysis.
The targeting of Russian-speaking users is an assessment derived from the language used in the phishing emails, the lure content in the malicious documents, links masquerade as Yandex Disk (“disk-yandex[.]ru”), and HTML web pages disguised as VK, a social network predominantly used in the country.
Gophish refers to an open-source phishing framework that allows organizations to test their phishing defenses by leveraging easy-to-use templates and launch email-based campaigns that can then be tracked in near real-time.
The unknown threat actor behind the campaign has been observed taking advantage of the toolkit to send phishing messages to their targets and ultimately push DCRat or PowerRAT depending on the initial access vector used: A malicious Microsoft Word document or an HTML embedding JavaScript.
When the victim opens the maldoc and enables macros, a rogue Visual Basic (VB) macro is executed to extract an HTML application (HTA) file (“UserCache.ini.hta”) and a PowerShell loader (“UserCache.ini”).
The macro is responsible for configuring a Windows Registry key such that the HTA file is automatically launched every time a user logs into their account on the device.
The HTA file, for its part, drops a JavaScript file (“UserCacheHelper.lnk.js”) that’s responsible for executing the PowerShell Loader. The JavaScript is executed using a legitimate Windows binary named “cscript.exe.”
“The PowerShell loader script masquerading as the INI file contains base64 encoded data blob of the payload PowerRAT, which decodes and executes in the victim’s machine memory,” Raghuprasad said.
The malware, in addition to performing system reconnaissance, collects the drive serial number and connects to remote servers located in Russia (94.103.85[.]47 or 5.252.176[.]55) to receive further instructions.
“[PowerRAT] has the functionality of executing other PowerShell scripts or commands as directed by the [command-and-control] server, enabling the attack vector for further infections on the victim machine.”
In the event no response is received from the server, PowerRAT comes fitted with a feature that decodes and executes an embedded PowerShell script. None of the analyzed samples thus far have Base64-encoded strings in them, indicating that the malware is under active development.
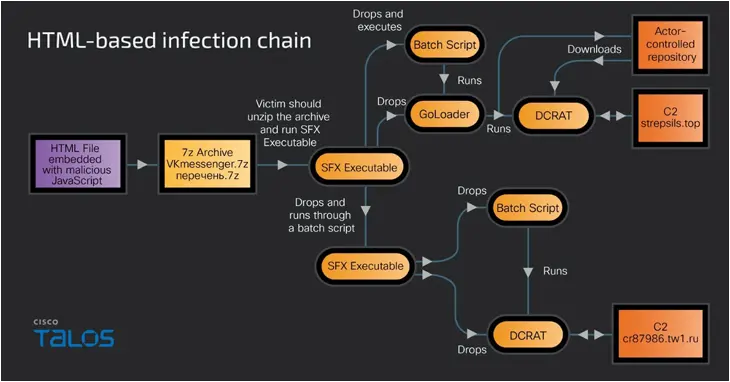
The alternate infection chain that employs HTML files embedded with malicious JavaScript, in a similar vein, triggers a multi-step process that leads to the deployment of DCRat malware.
“When a victim clicks on the malicious link in the phishing email, a remotely located HTML file containing the malicious JavaScript opens in the victim machine’s browser and simultaneously executes the JavaScript,” Talos noted. “The JavaScript has a Base64-encoded data blob of a 7-Zip archive of a malicious SFX RAR executable.”
Present within the archive file (“vkmessenger.7z”) – which is downloaded via a technique called HTML smuggling – is another password-protected SFX RAR that contains the RAT payload.
It’s worth noting that the exact infection sequence was detailed by Netskope Threat Labs in connection with a campaign that leveraged fake HTML pages impersonating TrueConf and VK Messenger to deliver DCRat. Furthermore, the use of a nested self-extracting archive has been previously observed in campaigns delivering SparkRAT.
“The SFX RAR executable is packaged with the malicious loader or dropper executables, batch file, and a decoy document in some samples,” Raghuprasad said.
“The SFX RAR drops the GOLoader and the decoy document Excel spreadsheet in the victim machine user profile applications temporary folder and runs the GOLoader along with opening the decoy document.”
The Golang-based loader is also designed to retrieve the DCRat binary data stream from a remote location through a hard-coded URL that points to a now-removed GitHub repository and save it as “file.exe” in the desktop folder on the victim’s machine.
DCRat is a modular RAT that can steal sensitive data, capture screenshots and keystrokes, and provide remote control access to the compromised system and facilitate the download and execution of additional files.
“It establishes persistence on the victim machine by creating several Windows tasks to run at different intervals or during the Windows login process,” Talos said. “The RAT communicates to the C2 server through a URL hardcoded in the RAT configuration file […] and exfiltrates the sensitive data collected from the victim machine.”
The development comes as Cofense has warned of phishing campaigns that incorporate malicious content within virtual hard disk (VHD) files as a way to avoid detection by Secure Email Gateways (SEGs) and ultimately distribute Remcos RAT or XWorm.
“The threat actors send emails with .ZIP archive attachments containing virtual hard drive files or embedded links to downloads that contain a virtual hard drive file that can be mounted and browsed through by a victim,” security researcher Kahng An said. “From there, a victim can be misled into running a malicious payload.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.