Attackers Targeting Fortinet Devices and SAP Applications


The following blog was co-authored by Caitlin Condon and Bob Rudis, also known (in his own words) as “some caveman from Maine.”
Last week, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the FBI published a joint alert to warn users that APT threat actors were likely exploiting unpatched Fortinet FortiOS devices to gain initial access to government, commercial, technology, and other organizations’ networks. The alert highlighted three FortiOS vulnerabilities, all of which were previously known, and at least one of which (CVE-2018-13379) has been broadly exploited for more than 18 months. This week, CISA published an additional alert amplifying a threat report from security firm Onapsis, which describes ongoing attacks against SAP applications.
Rapid7 has previously analyzed a number of the highest-severity vulnerabilities enumerated in this latest set of alerts. The CVEs included in these reports have been detailed below, along with recommendations for organizations seeking to defend themselves against ongoing exploitation. Notably, none of these vulnerabilities are new—many of them are a year or more old, which underscores the need for a regular patch cycle, as well as a defined patch cycle exception process.
FortiOS vulnerabilities
Fortinet devices are what we call network pivots—that is, the position they occupy in organizations’ networks gives external attackers the ability to access internal networks if exploited successfully, which in turn allows for a range of secondary attacks and other nefarious activities. If at all possible, defenders should strongly consider implementing a “zero-day” patch cycle for internet-exposed and other network pivot products, including (but not only) Fortinet and other VPNs. InsightVM and Nexpose customers can assess their exposure to all three FortiOS CVEs below with vulnerability checks.
- CVE-2018-13379 is a pre-authentication information disclosure vulnerability that arises from a path traversal flaw in the web portal component of FortiOS SSL VPNs. The vulnerability allows external attackers to download FortiOS system files through specially crafted HTTP resource requests and has been exploited in the wild since 2019. Read our full analysis of CVE-2018-13379 and its history here.
- CVE-2019-5591 is a default configuration vulnerability in FortiOS that allows an unauthenticated attacker on the same subnet to intercept sensitive information by impersonating the LDAP server.
- CVE-2020-12812 is an improper authentication vulnerability in SSL VPN in FortiOS 6.4.0, 6.2.0 to 6.2.3, 6.0.9 and below that gives a user the ability to log in successfully without being prompted for the second factor of authentication (FortiToken) if that user changes the case of their username.
Since the beginning of March, Rapid7 Labs’ Heisenberg Honeypot fleet has seen nearly 60 IP addresses attempting common, known single GET request exploits against Fortinet devices (we’ve grouped the IP addresses up to the hosting provider/ISP level):
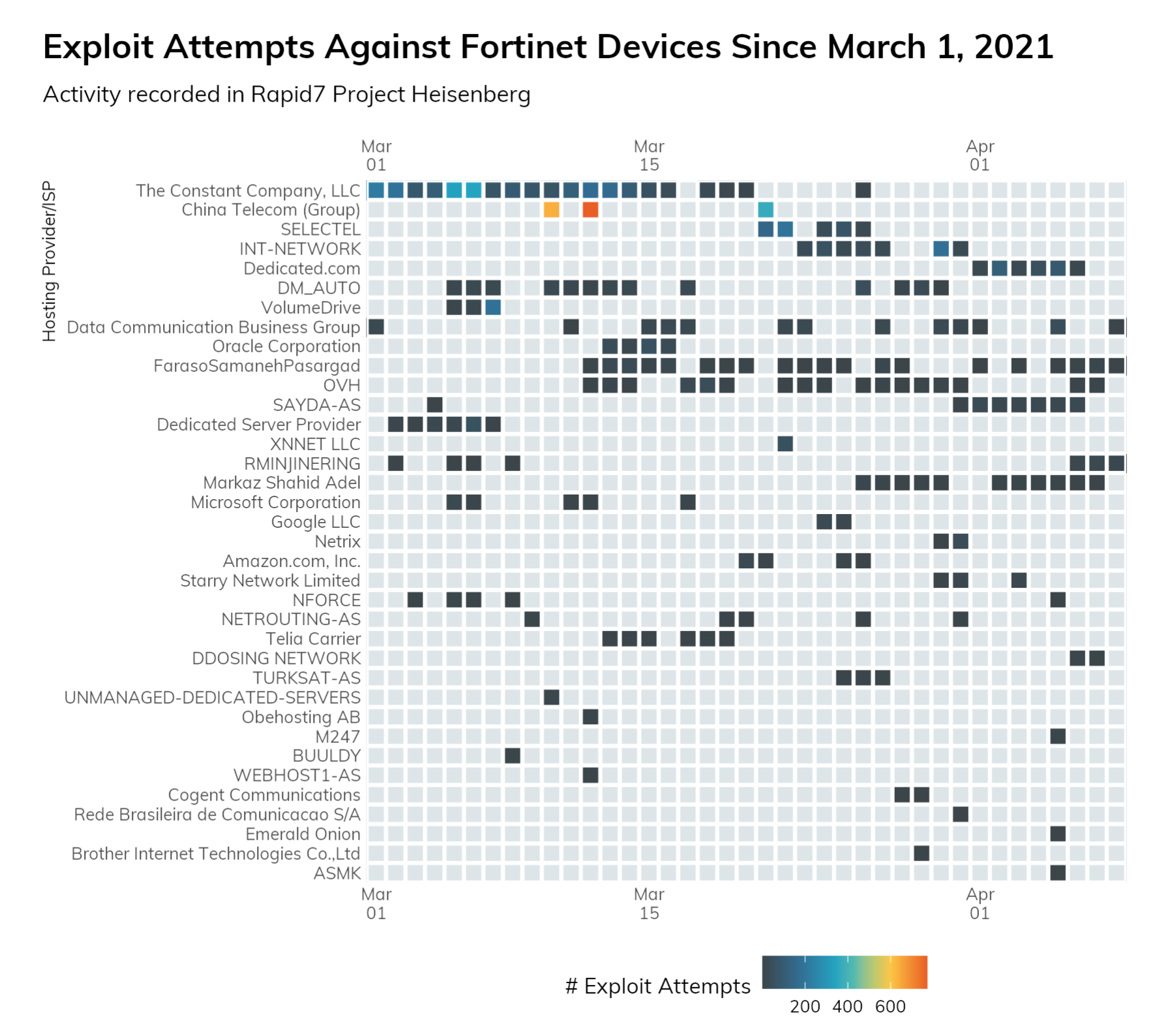

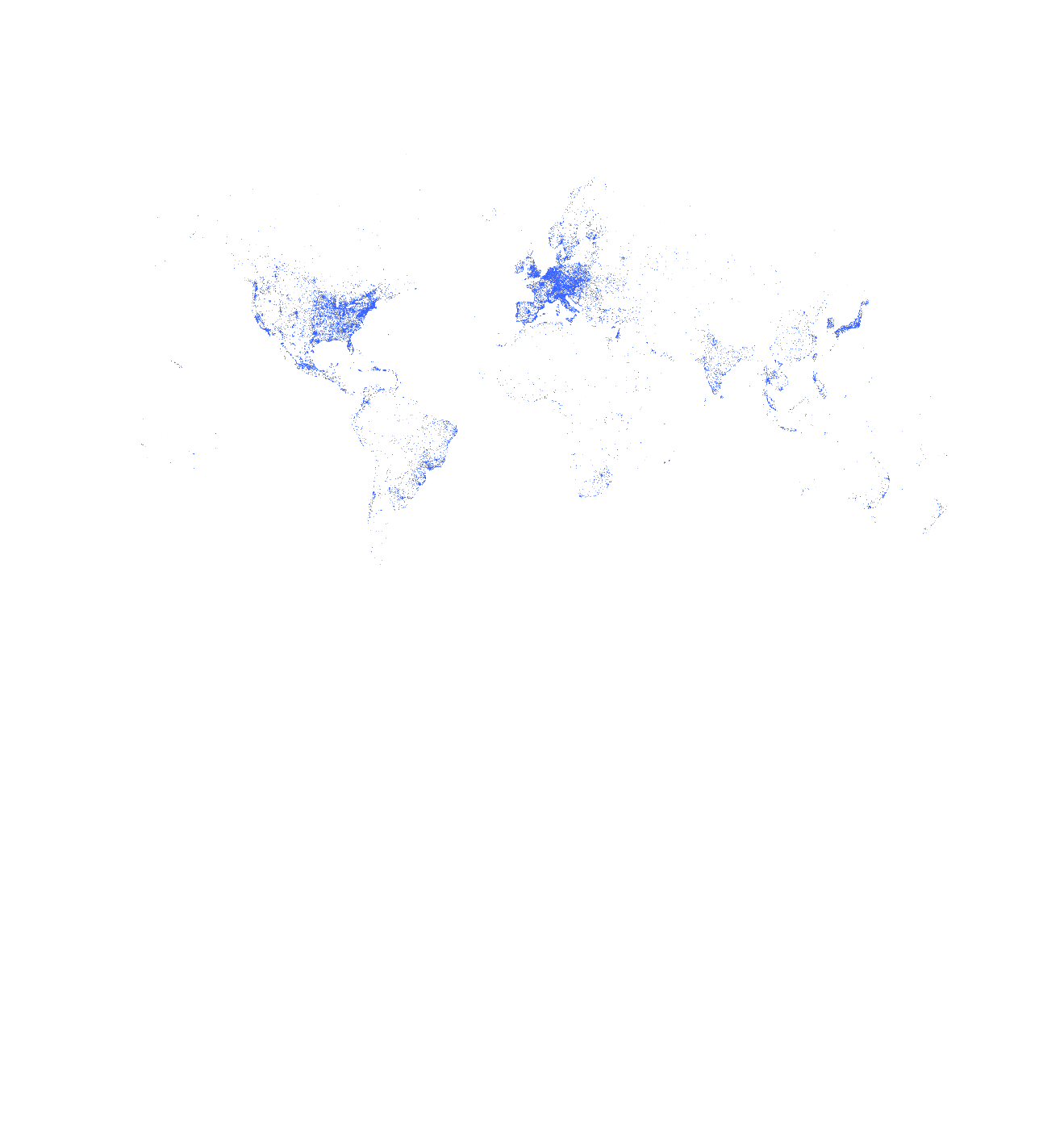
Unfortunately, our fleet does not emulate Fortinet devices. Since these devices are fairly easy to distinguish on the internet (nearly 1 million of them in the image, below)—due to the common, vendor SSL certificate they use—it is surprising to see opportunistic exploit attempts versus just inventory/discovery scans.

That last sentence should help organizations underscore why CISA and the FBI raised the Fortinet exploitation campaign to the level of a joint alert: Attackers can easily identify legitimate Fortinet endpoints on the internet, and it takes virtually no time from discovery to exploit if a target system is not patched and configured properly.
On April 3, 2021, Fortinet published a post on patch and vulnerability management where they outlined their emergency response and patch release practices new alignment to ISO standards and further emphasized the need to keep internet-exposed Fortinet devices patched. They have a special knowledge base article on how to keep notified about Fortinet patch releases and provide multiple ways for organizations to say current on Fortinet security updates.
As Fortinet notes in that post, these weaknesses have had patches available for quite some time, so if you’re just getting around to fixing them, you may need to dedicate some further cycles to some forensic activity, as it is very likely one or more attackers have already taken advantage of these vulnerabilities.
To learn more about other vulnerabilities that functioned as network pivots for attackers, read Rapid7’s 2020 Vulnerability Intelligence Report.
Actively exploited SAP vulnerabilities
The two most recent SAP vulnerabilities detailed in Onapsis’ threat report are CVE-2020-6287, a CVSS-10 vulnerability in the SAP NetWeaver Application Server (AS) Java component LM Configuration Wizard that has been actively exploited in the wild since July 2020, and SAP Solution Manager CVE-2020-6207. Both of these vulnerabilities allow broad compromise of SAP applications and environments.
- CVE-2020-6287 is present by default in SAP applications running on top of SAP NetWeaver AS Java 7.3 and any newer versions (up to SAP NetWeaver 7.5). It allows remote, unauthenticated attackers to exploit and fully compromise vulnerable SAP installations. Exploitation of CVE-2020-6287 through the HTTP interface allows for modification or extraction of highly sensitive information and disruption of critical business processes. For a list of affected applications and additional guidance, read Rapid7’s full analysis here.
- CVE-2020-6207 arises from a missing authentication check in version 7.2 of SAP’s Solution Manager product, allowing attackers to completely compromise all SMDAgents connected to the Solution Manager.
SAP customers should pay close attention to their access logs and monitor for unauthorized user account creation; they should also ensure that web services in general do not run using privileged accounts. InsightVM and Nexpose customers can assess their risk to CVE-2020-6287 with a remote vulnerability check. A check for CVE-2020-6207 is currently under development.
Other SAP vulnerabilities noted as being exploited in the wild include:
- CVE-2018-2380 affects SAP CRM versions 7.01, 7.02, 7.30, 7.31, 7.33, and 7.54. The vulnerability allows an attacker to exploit insufficient validation of path information provided by users, letting characters representing “traverse to parent directory” pass through to the file APIs.
- CVE-2016-9563 is a vulnerability in SAP NetWeaver Application Server (AS) Java 7.5 that allows remote authenticated users to conduct XML External Entity (XXE) attacks via the sap.com~tc~bpem~him~uwlconn~provider~web/bpemuwlconn URI.
- CVE-2016-3976 is a directory traversal vulnerability in SAP NetWeaver AS Java 7.1 through 7.5 that allows remote attackers to read arbitrary files via a .. (dot dot backslash) in the fileName parameter to
CrashFileDownloadServlet. - CVE-2010-5326 is a CVSS-10 vulnerability in the
InvokerServlet on SAP NetWeaver Application Server Java platforms that arises from a lack of authentication and allows remote attackers to execute arbitrary code via an HTTP or HTTPS request. It was used in attacks from 2013 to 2016.
Attackers have used these vulnerabilities to establish persistence, escalate privileges, and evade detection. It is also possible that threat actors may build exploit chains that extend access beyond SAP applications to underlying operating systems. Further information and recommendations is available from Onapsis here.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Cobalt Strike Beacon Detected - 52[.]231[.]10[.]139:8080 6 Cobalt Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)