JBS says it is recovering quickly from a ransomware attack
This week another major supplier reported it had been hit with ransomware. After the Colonial Pipeline attack last month, this time the victim is the world’s largest meatpacker, JBS. JBS halted cattle slaughter at all its US plants on Tuesday after the attack caused their Australian operations to shut down on Monday. Some plant shifts in Canada were also canceled Monday and Tuesday. The company’s operations in Mexico and the UK were not impacted and are conducting business as normal.
JBS
JBS is the second largest meat and poultry processor in the US. JBS controls about 20 percent of the slaughtering capacity for US cattle and hogs. It owns the Swift brand, and most of chicken processor Pilgrim’s Pride Co. Due to the attack, US meatpackers slaughtered 22 percent fewer cattle than a week earlier. There are early fears that ongoing shutdowns of JBS plants could raise meat prices further for American consumers.
The attack
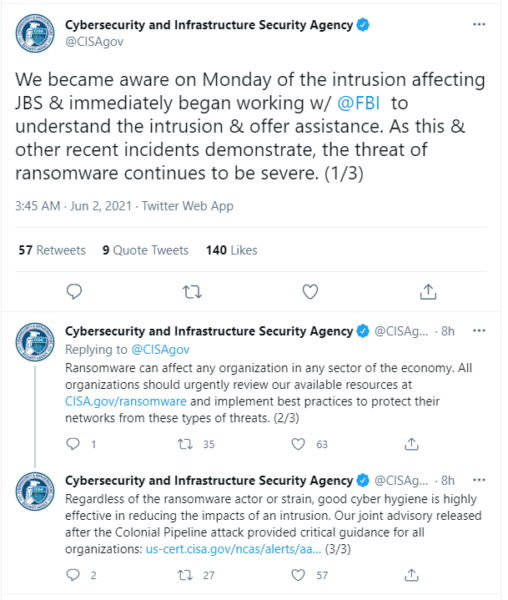
The initial press statement by JBS mentioned an “organized cybersecurity attack,” affecting some of the servers supporting its North American and Australian IT systems. Soon after it became clear that the company was dealing with a ransomware attack because a ransom demand came in. This was later confirmed by some tweets from the Cybersecurity and Infrastructure Security Agency (CISA).
At the moment of writing it is unclear which ransomware family was involved or how the attack took place, although early reporting indicates the cybercrime group responsible is REvil. The same early reporting also indicates that, if REvil was indeed responsible for the attack, the group has not written about the attack publicly on its darkweb blog called “Happy Blog.”
Recovery
According to JBS, they have made significant progress in resolving the cyberattack that has impacted the company’s operations.
“Our systems are coming back online and we are not sparing any resources to fight this threat. We have cybersecurity plans in place to address these types of issues and we are successfully executing those plans. Given the progress our IT professionals and plant teams have made in the last 24 hours, the vast majority of our beef, pork, poultry and prepared foods plants will be operational tomorrow.”
A one-day recovery time is remarkably fast, as many organizations takes weeks and sometimes even months to become fully operational after suffering a ransomware attack. We have even seen companies go bankrupt over the costs.
International intervention
What is also notable about this incident, as well as the attack on Colonial Pipeline, is the fact that the Biden administration has sent another warning to Russia, which is believed to be the origin of the cyberattacks. White House principal deputy press secretary Karine Jean-Pierre said:
“The White House is engaging directly with the Russian government on this matter and delivering the message that responsible states do not harbor ransomware criminals.”
Biden is scheduled to meet with Russian President Vladimir Putin in Geneva later this month.
Supply chains and critical infrastructure
The attacks on critical infrastructure—especially in supplies that we need on a daily basis—are very disruptive and it is no wonder that governments are likely to get involved. But it makes us wonder why the supply chains for food and oil seem to be a higher priority than other critical services like healthcare, schools, and emergency services, all of which have suffered countless attacks without political intervention. On the other hand, Colonial Pipeline and JBS represent suppliers for whom there are no immediate replacements if they shut down for a long time.
Of course, it is also possible that these attacks are done under the guise of ransomware attacks, but are in reality probes to see how vulnerable our infrastructure is, especially when major targets like Colonial Pipeline and JBS are involved.
The need to better secure the nation’s supply chains prompted the Department of Homeland Security last month to issue new security directives to regulate the pipeline industry for the first time. Maybe we can expect something similar for major food suppliers soon.
Ransomware Task Force
JBS reportedly informed the government about the ransomware attack, which is exactly the kind of behavior that the Ransomware Task Force would like to see of ransomware victims. The Ransomware Task Force (RTF), is a think tank composed of more than 60 volunteer experts who represent organizations encompassing industries and governments. The RTF has recently pushed out a comprehensive and strategic plan for tackling the increasing threat and evolution of ransomware.
Stay safe, everyone!
The post JBS says it is recovering quickly from a ransomware attack appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[CLOAK] - Ransomware Victim: Pe*************[.]lk 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)