njRAT : Uncovered
In the past thirty days an increase attack activity has been observed using the “njRAT” malware. This remote access trojan (RAT) has capabilities to log keystrokes, access the victim’s camera, steal credentials stored in browsers, open a reverse shell, upload/download files, view the victim’s desktop, perform process, file, and registry manipulations, and capabilities to let the attacker update, un-install, restart, close, disconnect the RAT and rename its campaign ID. Through the Command & Control (CnC) server software, the attacker has capabilities to create and configure the malware to spread through USB drives.
“njRAT” is currently leveraged by advanced threat actors in the Middle East, in particular when delivered via HTTP (i.e. Phishing attack or Drive-by download). It has also been observed that attackers are delivering “njRAT” embedded in other applications (i.e. L517 v.0.994 Word List Generator), and compressed with EZIRIZ .NET Reactor/.NET protector. Obfuscation with the use of compressors or protectors is a technique used by attackers to prevent detection by network based and host-based security defences.
It seems at present this RAT is being directed at Middle East organisations. Mostly government, telecommunications and the energy sector. But this tool can be downloaded freely on the internet if you know where to look and can be used against anyone. When this tool was analysed, many of the top Anti-Virus tools did not detect it.
Some of the file names of carrier files or njRAT samples observed were:
- L517 v0.994.exe
- RealUpgrade.exe
- password hotmail cracker 2013.exe
- elisa.exe
- Crack All Games.exe
- fresh cccvv all info 2013_txt.scr
- spoolsv.exe
- Hack Origin Game’s.exe
- Authorization form may – 2013 – 115444.scr
- Authorization.exe
The “njRAT” is a robust remote access trojan that once it reaches and infects the end-point, allows the attacker to have full control over the Victim system. With this access, the attacker can start scanning other systems in the victim network to perform lateral movement.
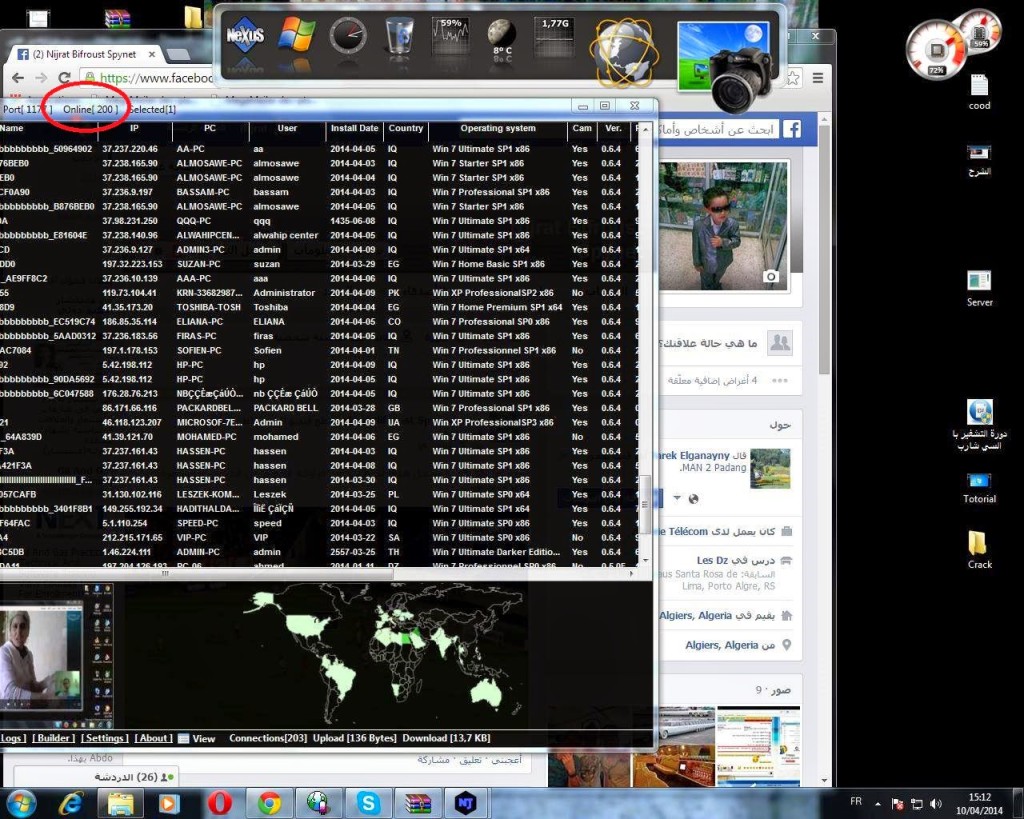
When the malware connects to the Command & Control (CnC) server, the attacker is able to perform the following actions from the njRAT CnC server GUI:
- Open a ‘File Manager’ window to manipulate files
- Open a ‘Run File’ window
- Open a ‘Remote Desktop’ window
- Open a ‘Remote Cam’ window
- Open a ‘Remote Shell’ window
- Open a ‘Process Manager’ window
- Open a ‘Registry’ window
- Open a ‘Keylogger’ window
- Open a ‘Get Passwords’ window
- Open a ‘Server’ window
- Open an ‘Open Folder’ window
As you can see above this is a particularly nasty Remote Access Tool. One of the ways to stay safe is to be careful with what you download. Warez and Cracks are easy ways to get infected.
For a full excellent breakdown and advanced analysis of this njRAT, please visit
http://threatgeek.typepad.com/files/fta-1009—njrat-uncovered-1.pdf
source:threatgeek.typepad.com


![Cobalt Strike Beacon Detected - 119[.]45[.]29[.]172:8089 4 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
