Spear phishing 101: what you need to know
Phishing, a cyberattack method as old as viruses and Nigerian Princes, continues to be one of the most popular means of initiating a breach against individuals and organizations, even in 2020. The tactic is so effective, it has spawned a multitude of sub-methods, including smishing (phishing via SMS), pharming, and the technique du jour for this blog: spear phishing.
But first, a quick parable.
A friend of mine received a blitz of emails over the course of a few days, all geared toward their Netflix account.
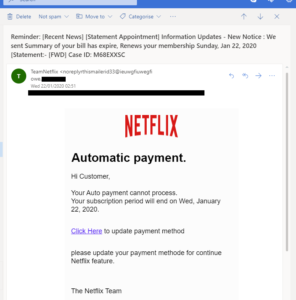
Click to enlarge
The clues indicating something wasn’t quite right were numerous:
- There were half a dozen emails instead of just one.
- All of them required payment information, but each mail gave a different reason as to why.
- There were spelling mistakes galore.
- The emails were not personalised in any way.
Even without spotting the utterly bogus, non HTTPS URL linked from the email body, this friend would never have fallen for it. Granted, they have a decent knowledge of security basics. However, consider if the attacker had done this:
- Grabbed some personal details from a data dump
- Hunted online for accounts belonging to this person, perhaps on social media
- Checked to see if they had an account with Netflix
- Crafted an imitation Netflix email address
- Addressed the potential victim directly by name
- Included some or all of their home address
- Made use of spell check
- Set up a free HTTPS website
- Used the most current version of Netflix’s logo
See the difference? While the first set of emails wouldn’t pass muster with a marginally knowledgeable user, the second would be much more difficult to screen as fake.
And that is what’s known in the business as spear phishing.
What is spear phishing?
Spear phishing’s sole purpose is to get inside the recipient’s head and make them think the messages they’re responding to are 100 percent legitimate—achieved due to personal touches designed to make them think what they’re dealing with is the real deal.
While you could argue alarm bells should ring when being asked for credit card details, in all honesty, once the scammer has thrown a few personal details into the mix like name and address, it may well be too late.
Imagine if the scammer monitored social media feeds to see which shows their target liked, then said something like, “Please ensure your details are correct to continue enjoying The Witcher.” Now add a picture of Henry Cavill looking cool.
Game. Over.
As you might expect, this kind of attack is rather difficult to combat. It doesn’t help when utterly random nonsense such as the poorly-made Netflix phishing attempt regularly inflict huge losses on organisations across the globe, despite being pretty terrible.
How many times have we seen healthcare facilities and even local municipal governments fall foul to ransomware via pretend spreadsheet attachments in fake HR tax emails? Make no mistake, this is a very real and immediate problem for those caught out.
With generic phishing already causing huge headaches for businesses and consumers alike, cybercriminals using data dumps expertly combined with professional social engineering techniques have an ever higher likelihood of success. And that’s before you consider other forms of spear phishing, such as conversation hijacking (more on this later), or attacks that use the spear phish as a launching pad for infecting networks with malware and other digital nasties.
Shall we take a look at some numbers?
Watch those verticals
A few years ago, the average cost of spear phish prevention over 12 months was $319,327 versus the significantly higher cost of any successful attack, which weighed in at $1.6 million. In 2019, the stats leaning heavily towards spear phishing speak for themselves, and huge payouts for scammers are the order of the day.
Payouts of $40 million, $50 million, and even $70 million and beyond are common, and that’s before you get to the cost of the cleanup and class action lawsuits. Throw in a little reputation damage and a PR firestorm, and you have all the ingredients for a successful breach. For the victims, not so much.
With spear phishing, the slightest piece of information can bring about an organisation’s downfall as it slices through all its otherwise fully functional security defences.
Evolution of the spear phish
Spear phishing isn’t only left to the realm of emails. Highly-targeted attacks also branch out into other areas, especially ones full of self volunteered information. Hijacking customer support conversations on Twitter is a great example of this: scammers set up imitation support accounts then barge into the conversation, leading the victim to phishing central. It’s a slick move.
It’s debatable how much of these scams are targeted, considering they’re making their attack up on the fly, instead of wading in with pre-gained knowledge. The difference here is the recon is aimed at the person the potential victim is being helped by, as opposed the victim themselves. Making note of when the customer support account is active, looking at initial Tweets so they can pretend to be the same person who helped before, and adopting some of their speech mannerisms/corporate speak all help to create a convincing illusion.
At that point, all we’re really dealing with is a perfectly-crafted imitation email but in human form, and with the ability to interact with the victim. Has spear phishing ever seen such a potent way to go on the offensive? When people are happy to weaponise customer support to use them against you, it’s really something to sit down and consider.
Fighting the rising tide of spear phishing
Anybody can be a target, but executives, especially at the CEO level, is where it’s at in terms of big scores for criminals (a form of targeting sometimes called whaling). By necessity, most organisations’ executives are set up to be publicly visible, and scammers take advantage of this. As has been mentioned, this is one of the toughest forms of attack to defend against.
If the social engineering component is designed to open the network to malware abuse, then we also need to consider the overall security infrastructure. Security software, updates, firewalls, and more all become important tools in the war against spear phishing—especially given what can come after the initial foot in the door attack.
Tools such as spam filtering and detection are great for random, casual attacks, but given the direct nature of spear phishing, it may well be a bridge too far for automation to flag as suspicious. Dedicated, ongoing training is important at all levels of the business, alongside not getting into the habit of blaming employees and third parties when things go wrong (and they will, eventually). You don’t want people less likely to report incidents out of fear of getting into trouble—it’s not productive and won’t help anybody.
Tools to aid in reporting spear phishing attacks, either dedicated apps or something web-based inside the network, are always useful. It’s also good to ensure departments have at least some idea how important business processes work in other departments. Securing the organization is a little easier when unrelated department A is an additional layer of defence for unrelated department B. Pay attention to HR, accounting, and top line exec interaction.
If your organisation hasn’t considered what to lock down yet, there’s never been a better time. Europol’s EC3 report on spear phishing was released late last year and contains a wealth of information on the subject for those wanting to dive deeper.
Ponder all forms of phishing, see which one(s) may be the biggest danger to your organisation and your employees, and start figuring out how best to approach the issue. You won’t regret it—but the scammers certainly will.
The post Spear phishing 101: what you need to know appeared first on Malwarebytes Labs.

