DrSemu – Malware Detection And Classification Tool Based On Dynamic Behavior
Dr.Semu runs executables in an isolated environment, monitors the behavior of a process, and based on Dr.Semu rules created by you or the community, detects if the process is malicious or not.
whoami: @_qaz_qaz
With Dr.Semu you can create rules to detect malware based on dynamic behavior of a process.
Isolation through redirection
Everything happens from the user-mode. Windows Projected File System (ProjFS) is used to provide a virtual file system. For Registry redirection, it clones all Registry hives to a new location and redirects all Registry accesses.
See the source code for more about other redirections (process/objects isolation, etc).
MonitoringDr.Semu uses DynamoRIO (Dynamic Instrumentation Tool Platform) to intercept a thread when it’s about to cross the user-kernel line. It has the same effect as hooking SSDT but from the user-mode and without hooking anything.
At this phase, Dr.Semu produces a JSON file, which contains information from the interception.
Detection
After terminating the process, based on Dr.Semu rules we receive if the executable is detected as malware or not.
Dr.Semu Rules/Detections
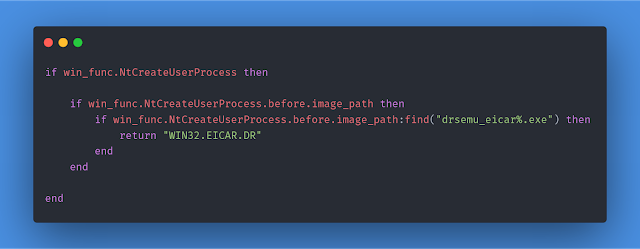
Dr.Semu rules
They are written in Python or LUA (located under dr_rules) and use dynamic information from the interception and static information about the sample. It’s trivial to add support of other languages.
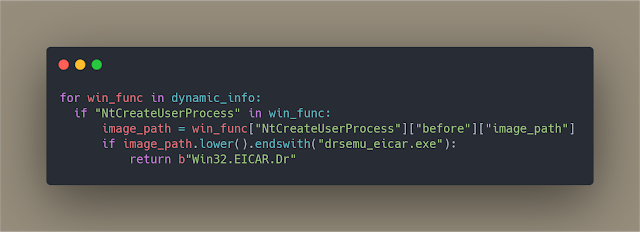

Example (Python): https://gist.github.com/secrary/ac89321b8a7bde998a6e3139be49eb72
Example (Lua): https://gist.github.com/secrary/e16daf698d466136229dc417d7dbcfa3
Usage
- Use
PowerShellto enableProjFSin an elevatedPowerShellwindow:
Enable-WindowsOptionalFeature -Online -FeatureName Client-ProjFS -NoRestart
- Download and extract a zip file from the releases page
- Download
DynamoRIOand extract intoDrSemufolder and rename todynamorio - Install Python 3 x64
DrSemu.exe --target file_pathDrSemu.exe --target files_directory
DEMO
BUILD
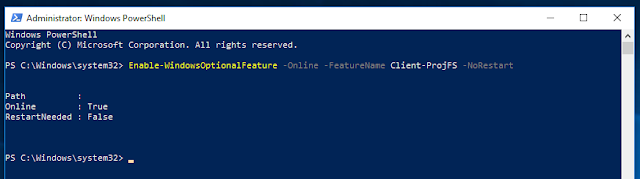
- Use
PowerShellto enableProjFSin an elevatedPowerShellwindow:
Enable-WindowsOptionalFeature -Online -FeatureName Client-ProjFS -NoRestart

- Install Python 3 x64
- Download
DynamoRIOand extract intobinfolder and rename todynamorio - Build
pe-parser-library.liblibrary:- Generate VS project from
DrSemushared_libspe_parseusing cmake-gui - Build 32-bit library under
build(shared_libspe_parsebuildpe-parser-libraryRelease) and 64-bit one underbuild64 - Change run-time library option to
Multi-threaded(/MT)
- Generate VS project from
- Set
LauncherCLIAs StartUp Project
TODO
- Solve isolation related issues
- Improve synchronization
- Update the description, add more details
- Create a GUI for the tool
Limitations
- Minimum supported Windows version:
Windows 10, version 1809 (due toWindows Projected File System) - Maximum supported Windows version:
Windows 10, version 1809 (DynamoRIOsupportsWindows 10versions until1809)

