BlackBasta is the latest ransomware to target ESXi virtual machines on Linux
BlackBasta, an alleged subdivision of the ransomware group Conti, just began supporting the encryption of VMware’s ESXi virtual machines (VM) installed on enterprise Linux servers. Because more and more organizations have begun using VMs for cost-effectiveness and easier management of devices, this change in tactic makes sense.
An ESXi VM is a bare-metal hypervisor software. Software can be characterized as “bare metal” if installed directly onto the physical machine, between the hardware and the operating system.
Siddharth Sharma and Nischay Hegde, threat researchers from Uptycs, were the first to spot and reveal BlackBasta’s tactical change in a report.
On Linux: BlackBasta 101
BlackBasta first appeared in April 2022 after the group ramped up their attacks against dozens of organizations. Although the brand seems relatively new, the way the group quickly accumulates victims, as well as their negotiation tactics, betray a level of experience not seen in fledgling and inexperienced online criminal gangs. This is probably why many cybersecurity communities associate them with known ransomware actors, particularly Conti.
Like other ransomware variants targeting Linux systems, BlackBasta encrypts the /vmfs/volumes folder. This is where virtual machines on ESXi servers are stored. Encrypting the files here will render VMs unusable.
If it cannot find this folder, however, the ransomware exits.
BlackBasta ransomware uses ChaCha20, a cryptographic algorithm known for its speed, to encrypt files. This is run in parallel with multithreading to make encryption faster, further avoid detection, and increase ransomware throughput.
Once files are encrypted, the extension .basta is appended at the end of all affected files. BlackBasta also drops the ransom note, readme.txt, which contains a unique ID and a URL to a chat support channel accessible only using Tor.
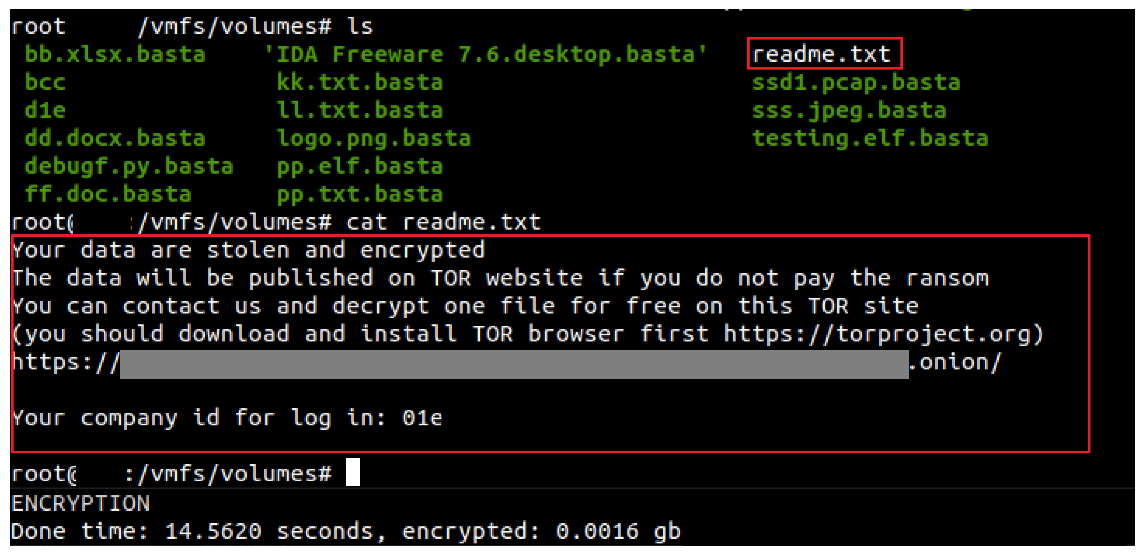
A section of the ransom note reads:
Your data are stolen and encrypted
The data will be published on TOR website if you do not pay the ransom
You can contact us and decrypt one file for free on this TOR site
(you should download and install TOR browser first https://torproject.org)
{URL redacted}Protect your Linux ESXi VM against ransomware attacks
Vincent Bariteau, Threat Intelligence Support Analyst at Malwarebytes, recommends organizations follow these best practices to protect their Linux servers against ransomware attacks if they’re using ESXi VM:
- Harden the SSH (Secure Shell) access to allow only a specific user to use it.
- Disable SSH if it’s not needed, or only make it available from a specific network/IP address via a firewall configuration.
- Ensure that you are following VMWare’s general security recommendations for ESXi.
Organizations also have the option of using a free, open-sourced tool called Lynis, which is an auditing tool.
The post BlackBasta is the latest ransomware to target ESXi virtual machines on Linux appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



