Daily Vulnerability Trends: Sat Jun 11 2022
| CVE NAME | CVE Description |
| CVE-2022-31626 | No description provided |
| CVE-2022-26937 | Windows Network File System Remote Code Execution Vulnerability. |
| CVE-2022-31402 | ITOP v3.0.1 was discovered to contain a cross-site scripting (XSS) vulnerability via /itop/webservices/export-v2.php. |
| CVE-2022-32275 | Grafana 8.4.3 allows reading files via (for example) a /dashboard/snapshot/%7B%7Bconstructor.constructor’/.. /.. /.. /.. /.. /.. /.. /.. /etc/passwd URI. |
| CVE-2021-0146 | Hardware allows activation of test or debug logic at runtime for some Intel(R) processors which may allow an unauthenticated user to potentially enable escalation of privilege via physical access. |
| CVE-2022-32250 | net/netfilter/nf_tables_api.c in the Linux kernel through 5.18.1 allows a local user (able to create user/net namespaces) to escalate privileges to root because an incorrect NFT_STATEFUL_EXPR check leads to a use-after-free. |
| CVE-2019-13382 | UploaderService in SnagIT 2019.1.2 allows elevation of privilege by placing an invalid presentation file in %PROGRAMDATA%\TechSmith\TechSmith Recorder\QueuedPresentations and then creating a symbolic link in %PROGRAMDATA%\Techsmith\TechSmith Recorder\InvalidPresentations that points to an arbitrary folder with an arbitrary file name. TechSmith Relay Classic Recorder prior to 5.2.1 on Windows is vulnerable. The vulnerability was introduced in SnagIT Windows 12.4.1. |
| CVE-2022-32276 | No description provided |
| CVE-2022-1588 | ** REJECT ** DO NOT USE THIS CANDIDATE NUMBER. Reason: This CVE has been rejected as it was incorrectly assigned. All references and descriptions in this candidate have been removed to prevent accidental usage. |
| CVE-2022-30287 | No description provided |
| CVE-2022-1609 | No description provided |
| CVE-2016-2388 | The Universal Worklist Configuration in SAP NetWeaver AS JAVA 7.4 allows remote attackers to obtain sensitive user information via a crafted HTTP request, aka SAP Security Note 2256846. |
| CVE-2022-29225 | Envoy is a cloud-native high-performance proxy. In versions prior to 1.22.1 secompressors accumulate decompressed data into an intermediate buffer before overwriting the body in the decode/encodeBody. This may allow an attacker to zip bomb the decompressor by sending a small highly compressed payload. Maliciously constructed zip files may exhaust system memory and cause a denial of service. Users are advised to upgrade. Users unable to upgrade may consider disabling decompression. |
| CVE-2022-31813 | Apache HTTP Server 2.4.53 and earlier may not send the X-Forwarded-* headers to the origin server based on client side Connection header hop-by-hop mechanism. This may be used to bypass IP based authentication on the origin server/application. |
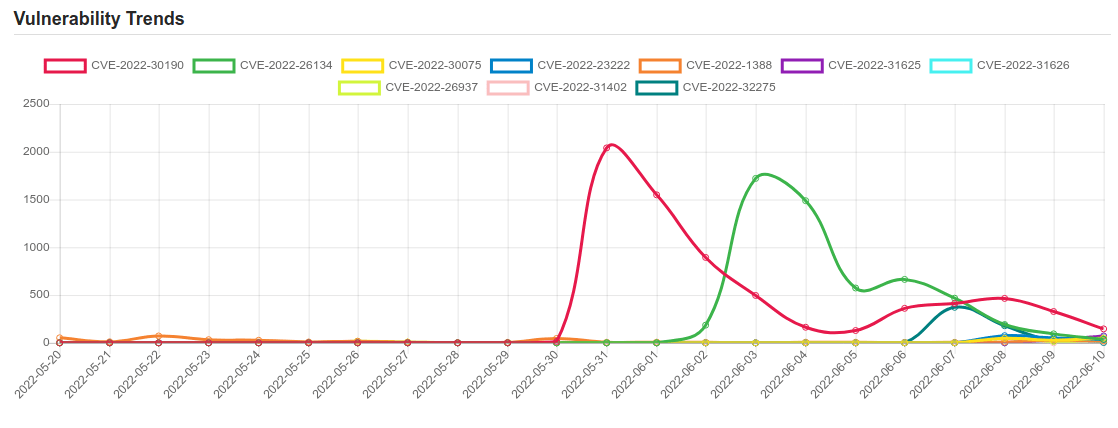
| CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. |
| CVE-2022-26134 | In affected versions of Confluence Server and Data Center, an OGNL injection vulnerability exists that would allow an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance. The affected versions are from 1.3.0 before 7.4.17, from 7.13.0 before 7.13.7, from 7.14.0 before 7.14.3, from 7.15.0 before 7.15.2, from 7.16.0 before 7.16.4, from 7.17.0 before 7.17.4, and from 7.18.0 before 7.18.1. |
| CVE-2022-30075 | In TP-Link Router AX50 firmware 210730 and older, import of a malicious backup file via web interface can lead to remote code execution due to improper validation. |
| CVE-2022-23222 | kernel/bpf/verifier.c in the Linux kernel through 5.15.14 allows local users to gain privileges because of the availability of pointer arithmetic via certain *_OR_NULL pointer types. |
| CVE-2022-1388 | On F5 BIG-IP 16.1.x versions prior to 16.1.2.2, 15.1.x versions prior to 15.1.5.1, 14.1.x versions prior to 14.1.4.6, 13.1.x versions prior to 13.1.5, and all 12.1.x and 11.6.x versions, undisclosed requests may bypass iControl REST authentication. Note: Software versions which have reached End of Technical Support (EoTS) are not evaluated |
| CVE-2022-31625 | No description provided |
If you like the site, please consider joining the telegram channel and supporting us on Patreon using the button below.


![[CLOAK] - Ransomware Victim: Pe*************[.]lk 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)