The nature of cyber incidents

Kaspersky provides incident response services and trainings to organizations around the world. In our annual incident response report, we share our observations and statistics based on investigation of real-life incidents. The report contains anonymized data collected by the Kaspersky Global Emergency Response Team (GERT), which is our main incident response and digital forensics unit. Researchers from Europe, Asia, North and South America, Africa, and Middle East work on Kaspersky GERT.
Since 2020, when the COVID-19 pandemic forced organizations to switch to working from home, our services have adapted to the new normal. In 2021, 98% or our incident response services were provided remotely.
2021 in numbers
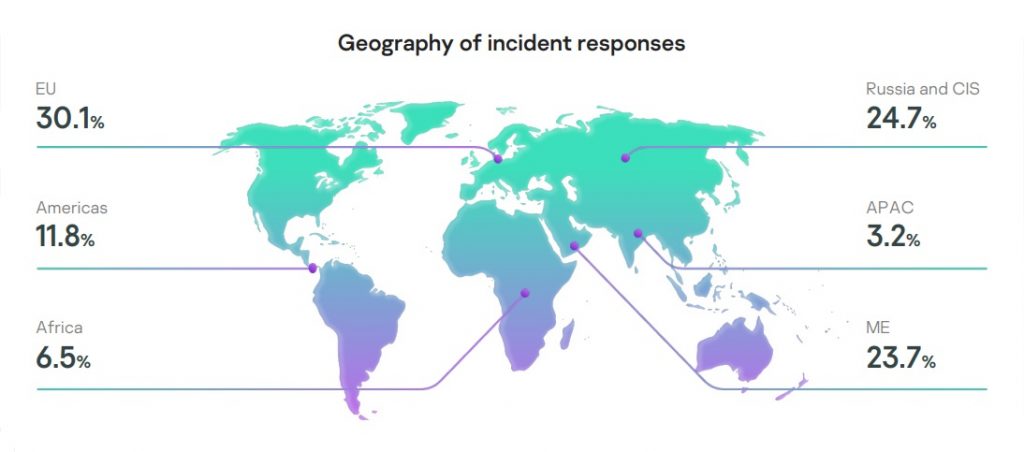
- The majority of requests for incident response services came from our customers in Europe (30.1%), the CIS (24.7%), and the Middle East (23.7%).
- Industrial (30.1%), governmental (19.4%) and financial (12.9%) organizations remain the most targeted ones.
- In 53.6% of cases, exploitation of vulnerabilities in public-facing applications was the initial infection vector.
- 51.9% of incidents were ransomware attacks, and in 62.5% of those cases, cybercriminals had had access to target systems for more than a month before they started file encryption.
- In 40% of incidents, cybercriminals used legitimate tools.
More details on cyberincidents and response measures can be found in the full version of the report. It includes following information:
- Review of 2021 trends
- Reasons for organizations to suspect an incident and request response
- Initial access vectors
- Exploits and tools used by cybercriminals
- Attack durations and response times
- Recommendations on protection against the threats
To download the full report (in PDF), please fill in the form below. Note that if you have strict security settings enabled in your browser, you will need to add this page to exceptions to see the form.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


