Royal Mail cyberattack linked to LockBit ransomware operation

A cyberattack on Royal Mail, UK’s largest mail delivery service, has been linked to the LockBit ransomware operation.
Yesterday, the Royal Mail disclosed that they suffered a cyber incident that forced them to halt international shipping services.
“Royal Mail is experiencing severe service disruption to our international export services following a cyber incident,” disclosed Royal Mail in a service update.
While Royal Mail did not provide any details on the cyberattack, they said they were working with external cybersecurity experts and have notified UK regulators and law enforcement.
LockBit ransomware encryptor used in the attack
As first reported by The Telegraph, the attack on Royal Mail is now confirmed to be a ransomware attack by the LockBit operation, or at least someone using their encryptors.
The Telegraph reports that the ransomware attack encrypted devices used for international shipping and caused ransom notes to be printed on printers used for customs dockets.
BleepingComputer has seen an unredacted version of the printed ransom notes and can confirm that they include the Tor websites for the LockBit ransomware operation.
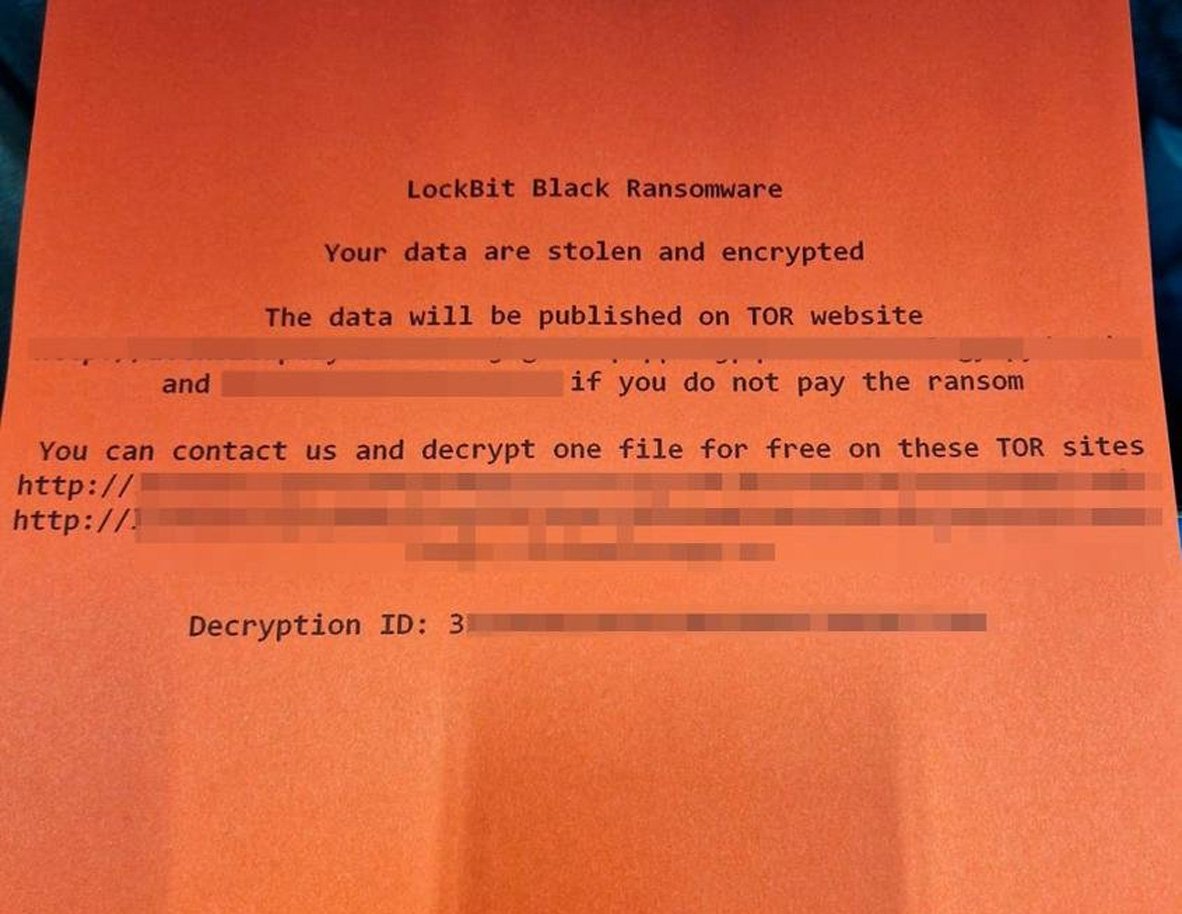

Source: Daniel Card on Twitter
The ransom note states it was created by “LockBit Black Ransomware,” which is the operation’s latest encryptor name as it includes code and features from the now-shut down BlackMatter ransomware gang.
The note also contains multiple links to the LockBit ransomware operation’s Tor data leak sites and negotiation sites, including a ‘Decryption ID’ required to log in to chat with the threat actors.
However, BleepingComputer has been told by multiple security researchers that this “Decryption ID” does not work.
It is unclear if the ransomware gang deleted the ID after news of the circulating ransom notes or if they moved negotiations to a new ID to avoid scrutiny by researchers and journalists.
BleepingComputer reached out to LockBitSupport, the public-facing representative of the ransomware operation, and was told that they did not attack Royal Mail and they blamed it on other threat actors using their leaked builder.
In September, the LockBit 3.0 ransomware builder was leaked on Twitter. This allowed other threat actors to launch ransomware operations based on the LockBit’s encryptor.
LockBitSupp’s explanation does not explain why Royal Mail’s ransom notes included links to LockBit’s Tor negotiation and data leak sites rather than the other threat actor’s sites who are allegedly using the builder.
However, if LockBitSupp is telling the truth and other threat actors used the leaked builder in the attack, then it would mean this was likely a destructive attack rather than one for personal gain, as there is no way to contact the actual attackers.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below


To keep up to date follow us on the below channels.









![[APT73] - Ransomware Victim: gureco[.]pl 9 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)