CISA releases free ‘Decider’ tool to help with MITRE ATT&CK mapping

The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has released ‘Decider,’ an open-source tool that helps defenders and security analysts quickly generate MITRE ATT&CK mapping reports.
The MITRE ATT&CK framework is a standard for identifying and tracking adversary tactics and techniques based on cyberattack observations, allowing defenders to adjust their security posture accordingly.
By having a common standard, organizations can quickly share comprehensive and accurate information about newly discovered or emerging threats and help hinder their effectiveness.
CISA recently published a “best practices” guide about MITRE ATT&CK mapping, highlighting the importance of using the standard.
Decider was developed in partnership with the Homeland Security Systems Engineering and Development Institute and MITRE and was made available for free via CISA’s GitHub repository.
“Today, CISA released Decider, a free tool to help the cybersecurity community map threat actor behavior to the MITRE ATT&CK framework,” reads a CISA announcement.
“Created in partnership with the Homeland Security Systems Engineering and Development Institute (HSSEDI) and MITRE, Decider helps make mapping quick and accurate through guided questions, a powerful search and filter function, and a cart functionality that lets users export results to commonly used formats.”
The tool asks user-guided questions about the observed adversary activity and generates the corresponding MITRE ATT&CK report.
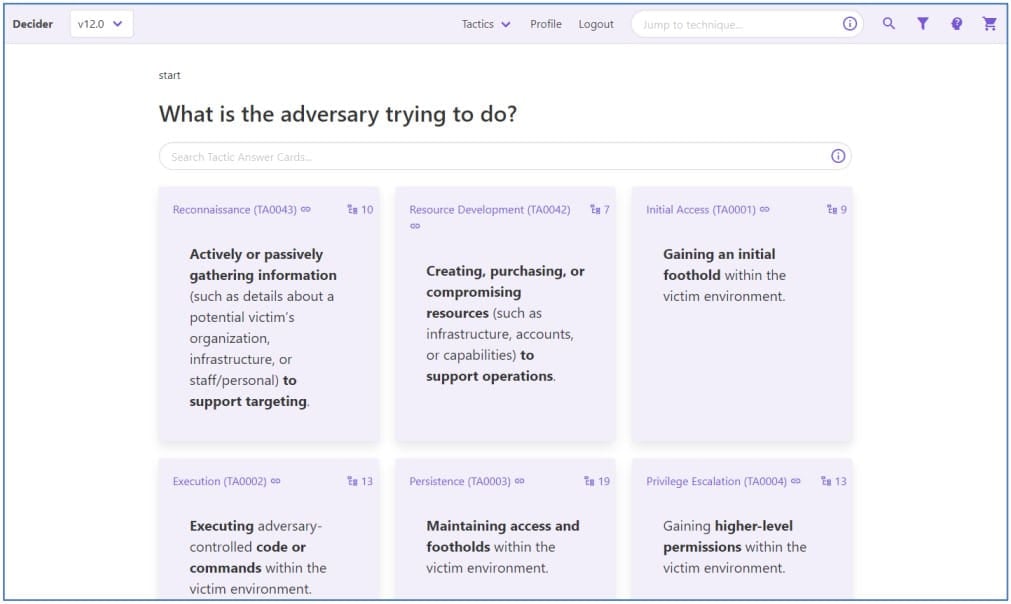

For example, a question might be “What is the adversary trying to do?” to which a possible answer is “Gain an initial foothold within the environment,” which corresponds to the Initial Access tactic.
The questions will continue until a subtechnique is reached for all tactics, or at least a technique, in case no subtechnique fits the particular activity.
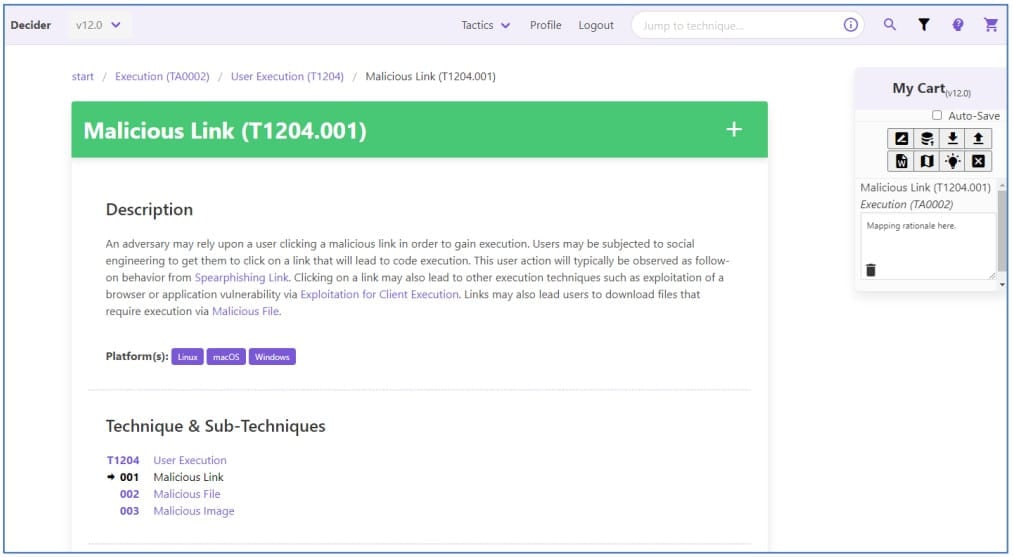

The defender can use the generated MITRE ATT&CK report to develop targeted defense tactics or export it in common formats and share it with others in the industry to prevent the proliferation of the identified threat.
As CISA explains in a fact sheet published alongside the release of Decider, MITRE ATT&CK mapping reports can help pass to the next stages of threat response, including:
- Visualizing the findings in ATT&CK Navigator
- Sharing the findings with others by publishing threat intelligence reports
- Finding sensors and analytics to detect those techniques
- Discovering mitigations that help prevent techniques from working in the first place
- Compiling threat emulation plans to validate defenses
CISA urges the cybersecurity community to download and use Decider and submit their feedback, bug reports, or even feature suggestions.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below


To keep up to date follow us on the below channels.









![[HUNTERS] - Ransomware Victim: Ace Laboratories Limited 10 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
