GoBruteforcer: New Golang-Based Malware Breaches Web Servers Via Brute-Force Attacks
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet.
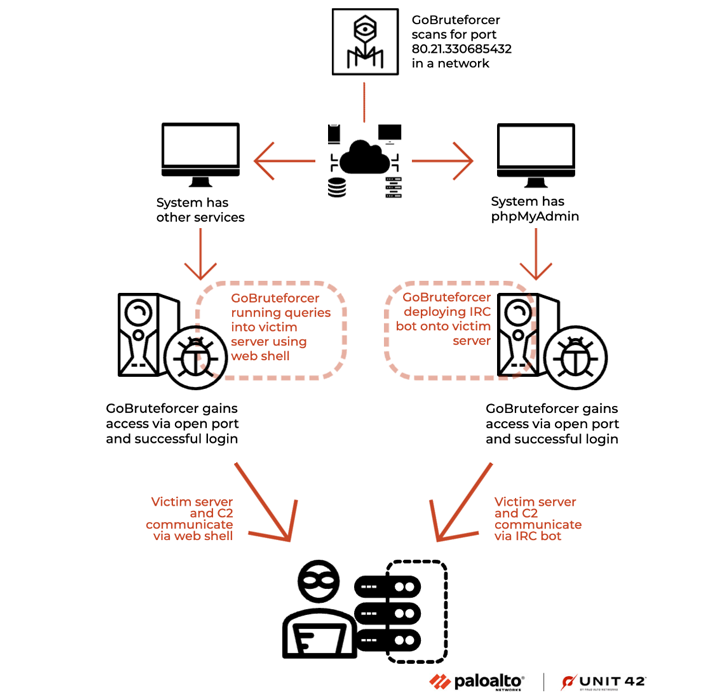
“GoBruteforcer chose a Classless Inter-Domain Routing (CIDR) block for scanning the network during the attack, and it targeted all IP addresses within that CIDR range,” Palo Alto Networks Unit 42 researchers said.
“The threat actor chose CIDR block scanning as a way to get access to a wide range of target hosts on different IPs within a network instead of using a single IP address as a target.”
GoBruteforcer is mainly designed to single out Unix-like platforms running x86, x64 and ARM architectures, with the malware attempting to obtain access via a brute-force attack using a list of credentials hard-coded into the binary.
If the attack proves to be successful, an internet relay chat (IRC) bot is deployed on the victim server to establish communications with an actor-controlled server.
GoBruteforcer also leverages a PHP web shell already installed in the victim server to glean more details about the targeted network.
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
RESERVE YOUR SEATThat said, the exact initial intrusion vector used to deliver both GoBruteforcer and the PHP web shell is undetermined as yet. Artifacts collected by the cybersecurity company suggest active development efforts to evolve its tactics and evade detection.
The findings are yet another indication of how threat actors are increasingly adopting Golang to develop cross-platform malware. What’s more, GoBruteforcer’s multi-scan capability enables it to breach a broad set of targets, making it a potent threat.
“Web servers have always been a lucrative target for threat actors,” Unit 42 said. “Weak passwords could lead to serious threats as web servers are an indispensable part of an organization. Malware like GoBruteforcer takes advantage of weak (or default) passwords.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below



To keep up to date follow us on the below channels.