BianLian ransomware gang shifts focus to pure data extortion

The BianLian ransomware group has shifted its focus from encrypting its victims’ files to only exfiltrating data found on compromised networks and using them for extortion.
This operational development in BianLian was reported by cybersecurity company Redacted, who have seen signs of the threat group attempting to craft their extortion skills and increase the pressure on the victims.
BianLian is a ransomware operation that first appeared in the wild in July 2022, successfully breaching multiple high-profile organizations.







In January 2023, Avast released a free decryptor to help victims recover files encrypted by the ransomware.
Recent BianLian attacks
Redacted reports that BianLian operators have kept their initial access and lateral movement techniques the same and continue to deploy a custom Go-based backdoor that gives them remote access on the compromised device, albeit a slightly improved version of it.
The threat actors post their victims in masked form as quickly as 48 hours after the breach on their extortion site, giving them roughly ten days to pay the ransom.
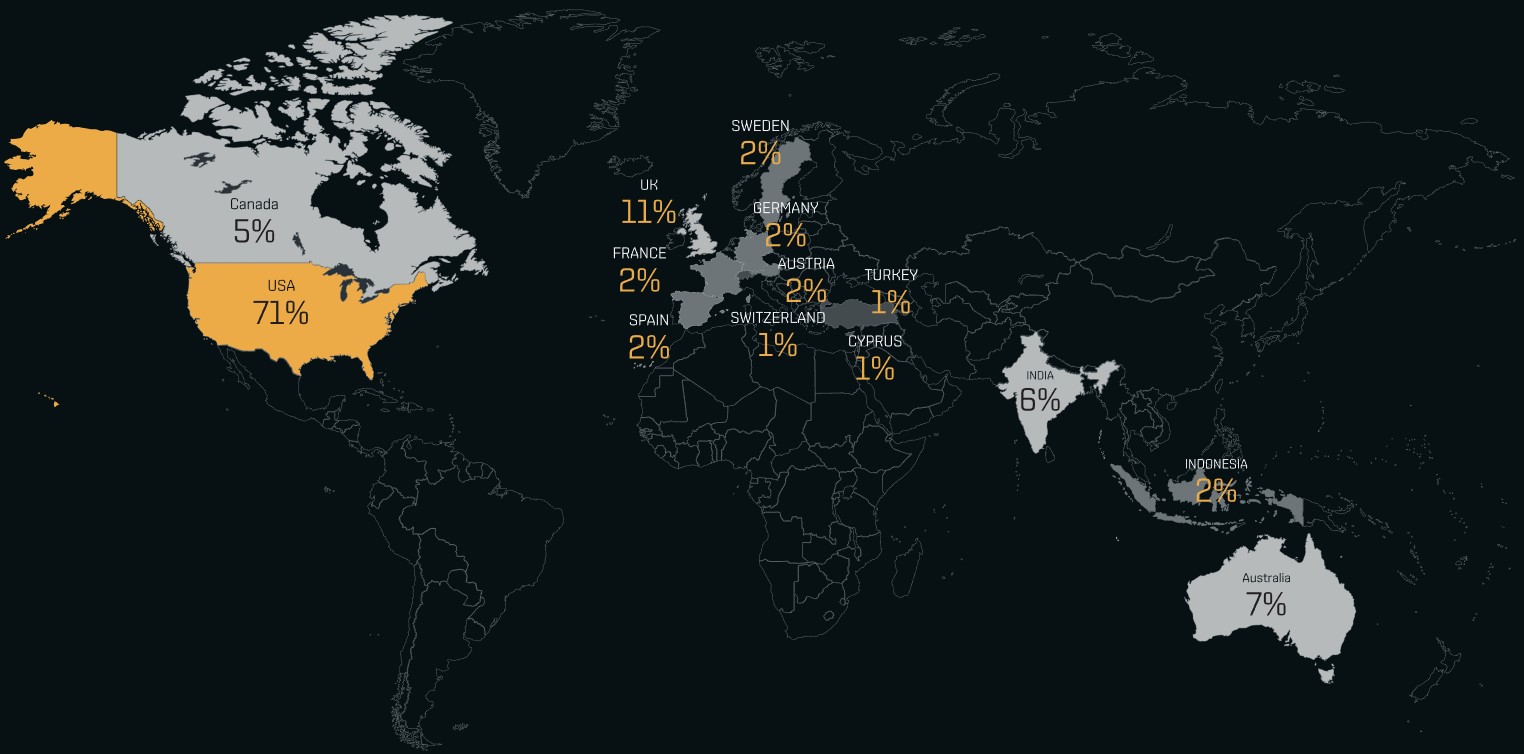
As of March 13, 2023, BianLian has listed a total of 118 victim organizations on their extortion portal, with the vast majority (71%) being U.S.-based companies.
The main difference seen in recent attacks is that BianLian attempts to monetize its breaches without encrypting the victim’s files. Instead, it now solely relies on threatening to leak the stolen data.
“The group promises that after they are paid, they will not leak the stolen data or otherwise disclose the fact the victim organization has suffered a breach. BianLian offers these assurances based on the fact that their “business” depends on their reputation,” mentions Redacted in the report.
“In several instances, BianLian made reference to legal and regulatory issues a victim would face were it to become public that the organization had suffered a breach. The group has also gone so far as to include specific references to the subsections of several laws and statutes.”
Redacted has found that in many cases, the law references made by BianLian operators were applicable in the victim’s region, indicating that the threat actors are honing their extortion skills by analyzing a victim’s legal risks to formulate strong arguments.
It is unknown if BianLian abandoned the encryption tactic because Avast broke their encryptor or because this event helped them realize they didn’t need that part of the attack chain to extort victims into paying ransoms.
It should be mentioned that when Avast released its free decryptor, BianLian downplayed its importance, saying it would only work on early “summer 2022” versions of the ransomware and would corrupt files encrypted by all subsequent builds.
Extortion without encryption
Encrypting files, data theft, and threatening to leak stolen files is known as a “double extortion” tactic, which serves as an additional form of coercion for ransomware gangs looking to increase pressure on their victims.
However, through the natural exchange between threat actors and victims, ransomware gangs realized that, in many cases, sensitive data leak was an even stronger payment incentive for victims.
This gave birth to encryption-less ransomware operations such as the late Babuk and SnapMC, and extortion operations that claim to not engage in file encryption themselves (or at all), like RansomHouse, Donut, and Karakurt.
Still, most ransomware groups continue using encryption payloads in their attacks, as the business disruption caused by encrypting devices puts even greater pressure on many victims.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





