WiFi protocol flaw allows attackers to hijack network traffic

Cybersecurity researchers have discovered a fundamental security flaw in the design of the IEEE 802.11 WiFi protocol standard, allowing attackers to trick access points into leaking network frames in plaintext form.
WiFi frames are data containers consisting of a header, data payload, and trailer, which include information such as the source and destination MAC address, control, and management data.
These frames are ordered in queues and transmitted in a controlled matter to avoid collisions and to maximize data exchange performance by monitoring the busy/idle states of the receiving points.
The researchers found that queued/buffered frames are not adequately protected from adversaries, who can manipulate data transmission, client spoofing, frame redirection, and capturing.
“Our attacks have a widespread impact as they affect various devices and operating systems (Linux, FreeBSD, iOS, and Android) and because they can be used to hijack TCP connections or intercept client and web traffic,” reads the technical paper published yesterday by Domien Schepers and Aanjhan Ranganathan of Northeastern University, and Mathy Vanhoef of imec-DistriNet, KU Leuven.
Power-saving flaw
The IEEE 802.11 standard includes power-save mechanisms that allow WiFi devices to conserve power by buffering or queuing frames destined for sleeping devices.
When a client station (receiving device) enters sleep mode, it sends a frame to the access point with a header that contains the power-saving bit, so all frames destined for it are queued.
The standard, however, does not provide explicit guidance on managing the security of these queued frames and does not set limitations like how long the frames can stay in this state.
Once the client station wakes up, the access point dequeues the buffered frames, applies encryption, and transmits them to the destination.
An attacker can spoof the MAC address of a device on the network and send power-saving frames to access points, forcing them to start queuing frames destined for the target. Then, the attacker transmits a wake-up frame to retrieve the frame stack.
The transmitted frames are usually encrypted using the group-addressed encryption key, shared among all the devices in the WiFi network, or a pairwise encryption key, which is unique to each device and used to encrypt frames exchanged between two devices.
However, the attacker can change the security context of the frames by sending authentication and association frames to the access point, thus forcing it to transmit the frames in plaintext form or encrypt them with an attacker-provided key.
This attack is possible using custom tools created by the researchers called MacStealer, which can test WiFi networks for client isolation bypasses and intercept traffic destined for other clients at the MAC layer.
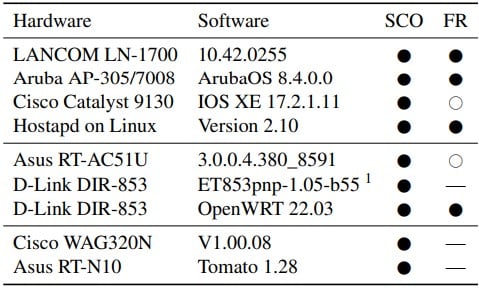
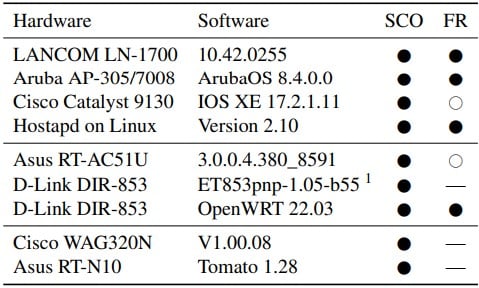
The researchers report that network device models from Lancom, Aruba, Cisco, Asus, and D-Link are known to be affected by these attacks, with the complete list below.
The researchers warn that these attacks could be used to inject malicious content, such as JavaScript, into TCP packets.
“An adversary can use their own Internet-connected server to inject data into this TCP connection by injecting off-path TCP packets with a spoofed sender IP address,” warn the researchers.
“This can, for instance, be abused to send malicious JavaScript code to the victim in plaintext HTTP connections with as goal to exploit vulnerabilities in the client’s browser.”
While this attack could also be used to snoop on traffic, as most web traffic is encrypted using TLS, there would be a limited impact.
The technical details and research are available in USENIX Security 2023 paper, which will be presented at the upcoming BlackHat Asia conference on May 12, 2023.
Cisco acknowledges flaw
The first vendor to acknowledge the impact of the WiFi protocol flaw is Cisco, admitting that the attacks outlined in the paper may be successful against Cisco Wireless Access Point products and Cisco Meraki products with wireless capabilities.
However, Cisco believes says that the retrieved frames are unlikely to jeopardize the overall security of a properly secured network.
Still, the firm recommends applying mitigation measures like using policy enforcement mechanisms through a system like Cisco Identity Services Engine (ISE), which can restrict network access by implementing Cisco TrustSec or Software Defined Access (SDA) technologies.
“Cisco also recommends implementing transport layer security to encrypt data in transit whenever possible because it would render the acquired data unusable by the attacker,” reads the Cisco security advisory.
Currently, there are no known cases of malicious use of the flaw discovered by the researchers.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![Cobalt Strike Beacon Detected - 47[.]106[.]229[.]212:443 10 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)