CheckXSS – Detect XSS vulnerability in Web Applications
Detect XSS vulnerability in Web Applications
Screenshots
Easy Installation
As simple as below, Just one line of code:
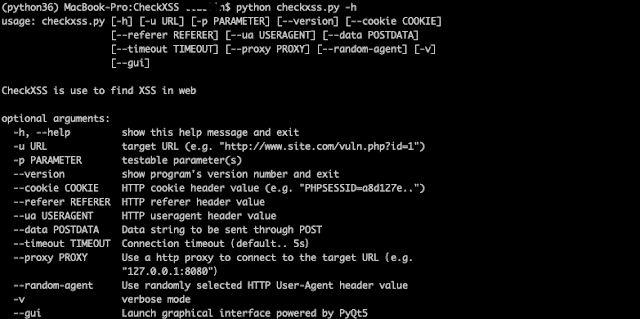
curl -L -s https://raw.githubusercontent.com/Jewel591/CheckXSS/master/docs/install.sh|bashUsage Instructionspython3.6 checkxss.py -h
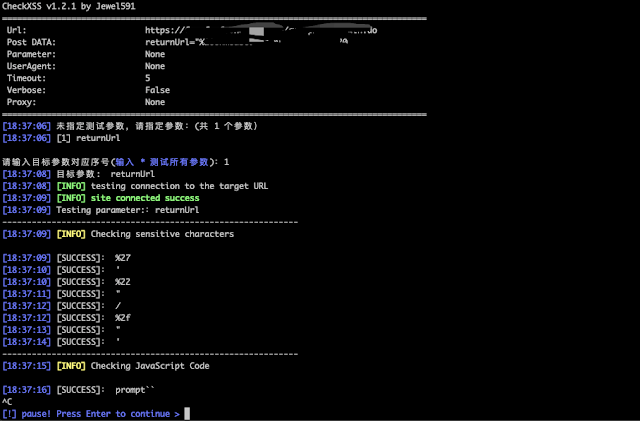
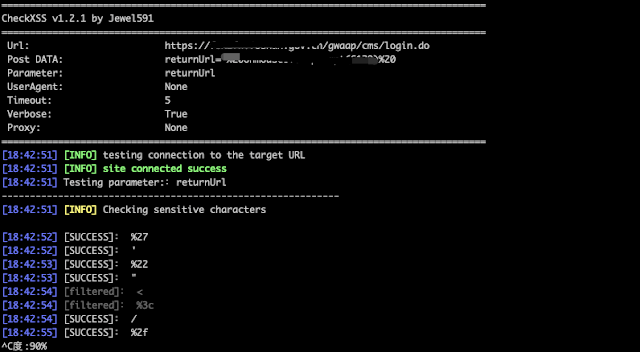
Support POST and GET request methods, support parameter injection detection in cookie, referer, useragent fields For example, test the returnUrl parameter in POST data:python3.6 checkxss.py -u "https://example.com/login.do" --data="returnUrl=utest" -p returnUrl
Features
- Support url encoding bypass
- Support unicode encoding of HTML tag attribute value to bypass
- Support HTML encoding to bypass the HTML tag attribute value
- Support for flexible replacement of () ‘”to bypass
- Case bypass
Contributing
Contributions, issues and feature requests are welcome!
Feel to check issues page
Maintainers
@Jewel591
Download CheckXSS
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![Cobalt Strike Beacon Detected - 140[.]143[.]132[.]170:80 9 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
