Thousands of Apache Superset servers exposed to RCE attacks

Apache Superset is vulnerable to authentication bypass and remote code execution at default configurations, allowing attackers to potentially access and modify data, harvest credentials, and execute commands.
Apache Superset is an open-source data visualization and exploration tool initially developed for Airbnb before it became a top-level project at the Apache Software Foundation in 2021.
According to a new report by Horizon3, Apache Superset used a default Flask Secret Key to sign authentication session cookies. As a result, attackers can use this default key to forge session cookies that allow them to log in with administrator privileges to servers that did not change the key.
While the Apache documentation does tell admins to change the secret keys, Horizon3 says that this dangerous default configuration is currently detectable in about 2,000 internet-exposed servers belonging to universities, corporations of varying sizes, government organizations, and more.
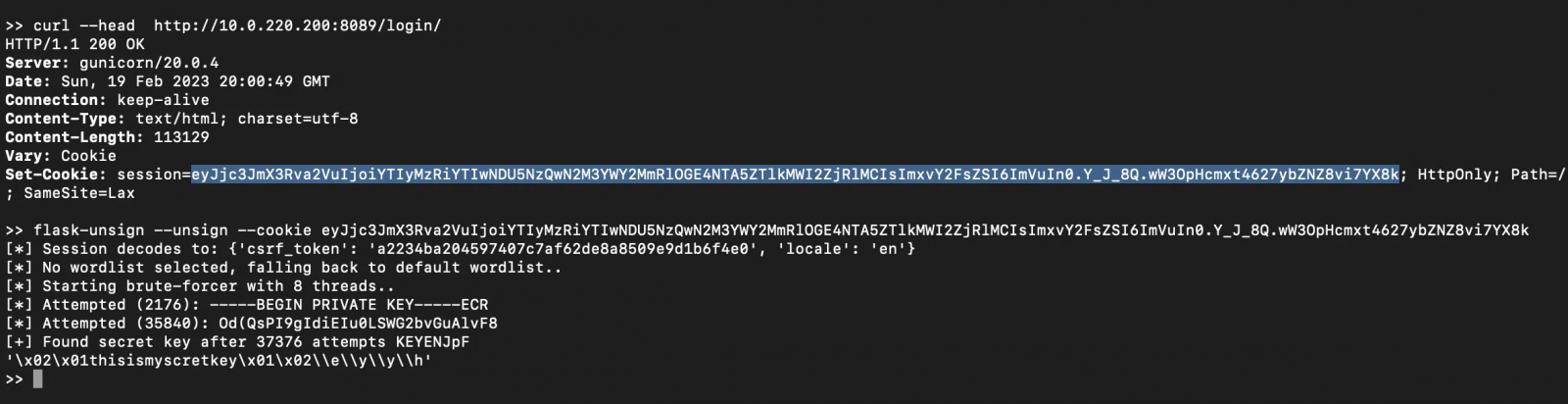

This widely used default Flask secret key is known to attackers who may use flask-unsign and forge their own cookies to gain administrator access on the target, accessing connected databases or executing arbitrary SQL statements on the application server.
“We are not disclosing any exploit methods at this time, though we think it’ll be straightforward for interested attackers to figure it out,” warns Horizon3.
It is important to note that if administrators have changed the default key with one unknown to the attackers, their installations are not vulnerable to this attack.
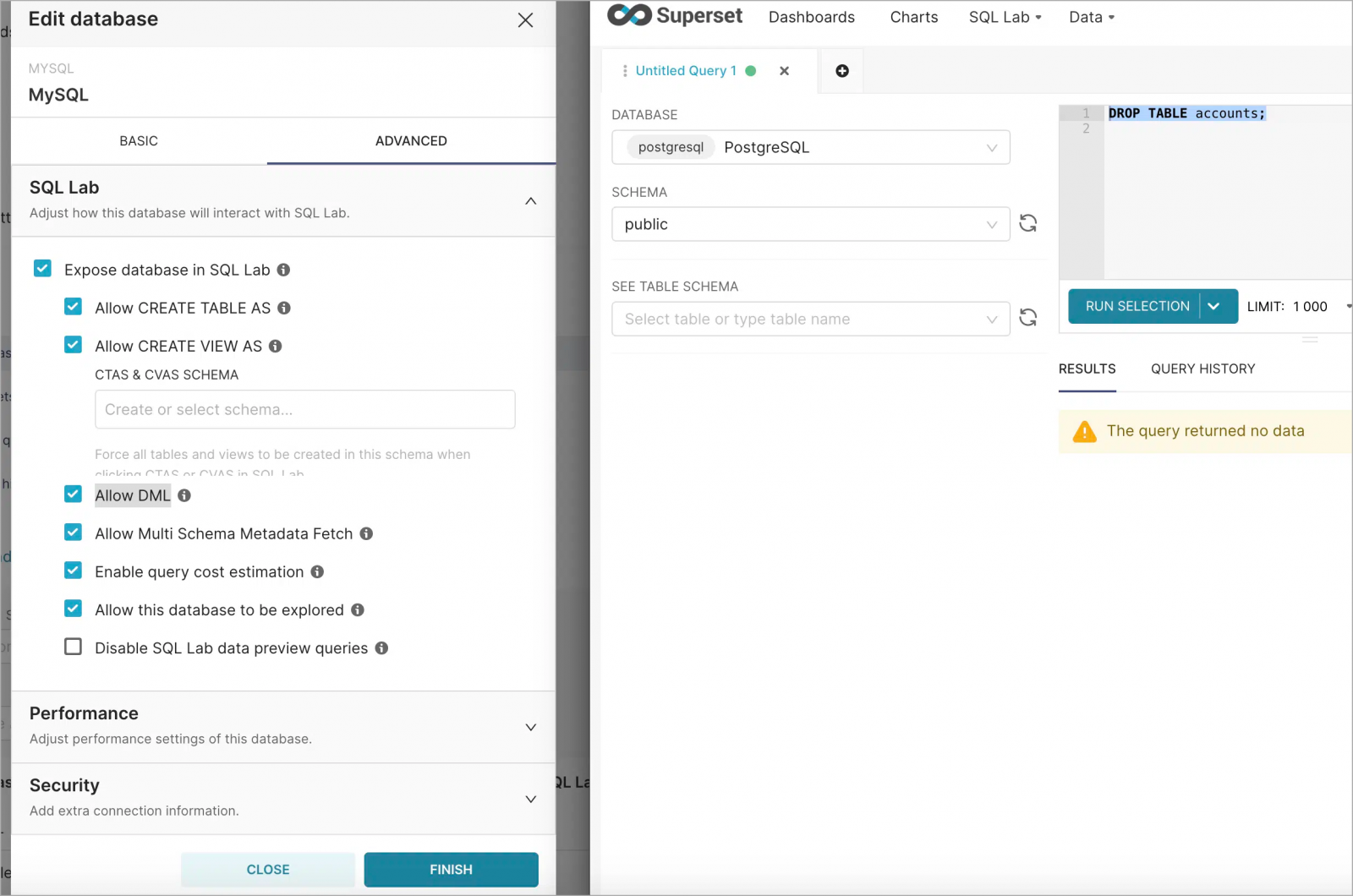

Discovery and Impact
The flaw was discovered by the Horizon3 team on October 11, 2021, and reported to the Apache Security team.
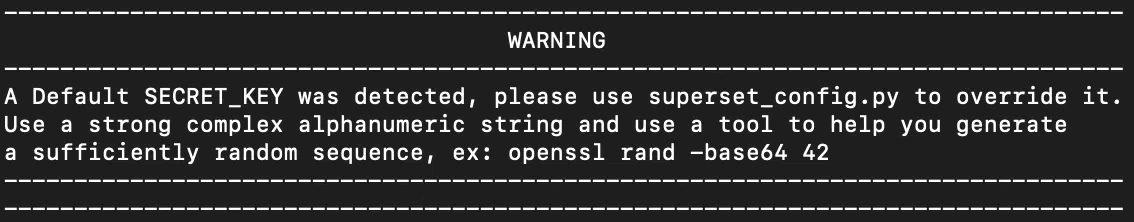
On January 11, 2022, the software developers released version 1.4.1, which changed the default ‘SECRET_KEY’ to a new string, and a warning was added to logs when the default string was detected on startup.
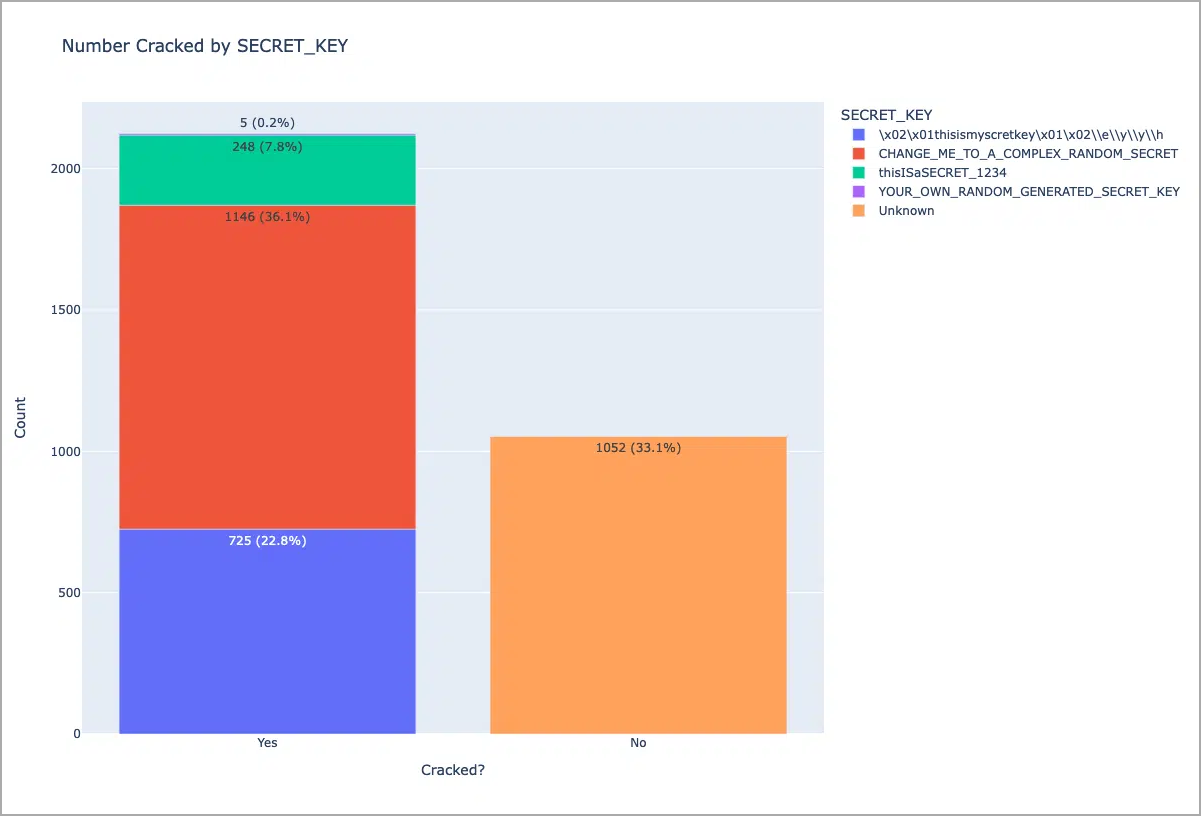
Horizon3 also found two other default keys used in documentation and templates and used Shodan to search for instances using those four keys.
At the time, Horizon3 found that roughly 2,124 (67% of the total) were misconfigured.
Horizon3 contacted Apache again and raised the issues, and in February 2023, the researchers began sending warnings to organizations of the need to change their configuration.
Eventually, on April 5, 2023, the Superset team released version 2.1, which does not allow the server to start up if it’s using a default ‘SECRET_KEY.’
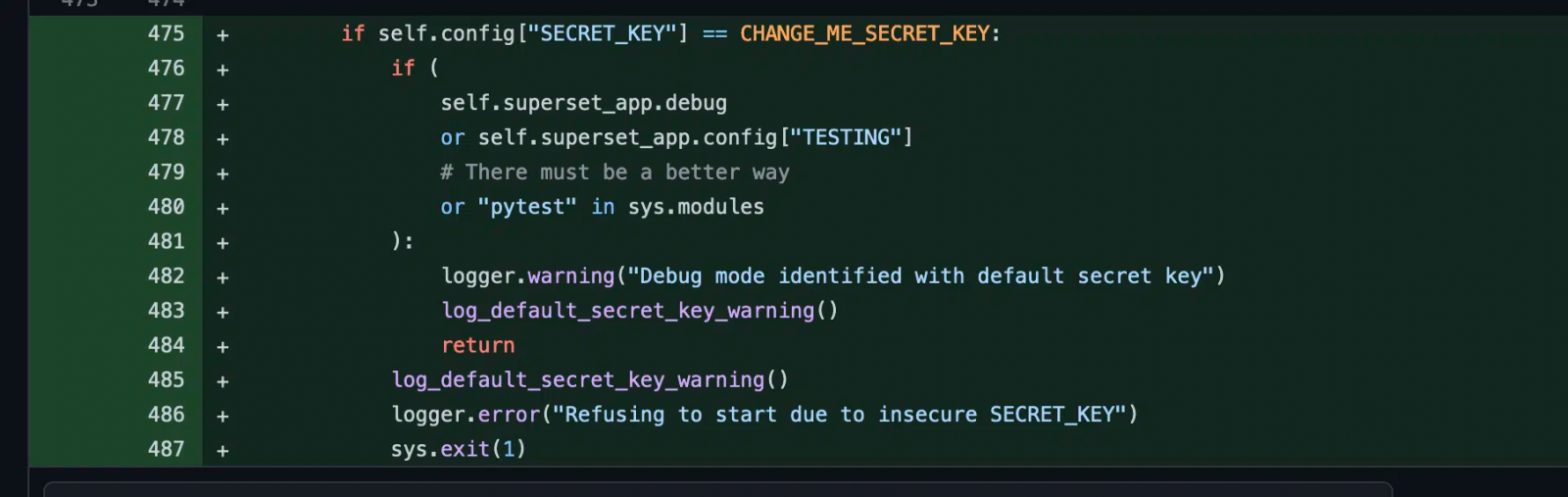
Although this drastic solution prevents new risky deployments, it does not fix existing misconfigurations, which according to Horizon3, are still present in over 2,000 cases.
The security company has shared a script on GitHub that Apache Superset admins can use to determine if their instance is vulnerable to attacks.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below




To keep up to date follow us on the below channels.





