GitHub Extends Push Protection to Prevent Accidental Leaks of Keys and Other Secrets
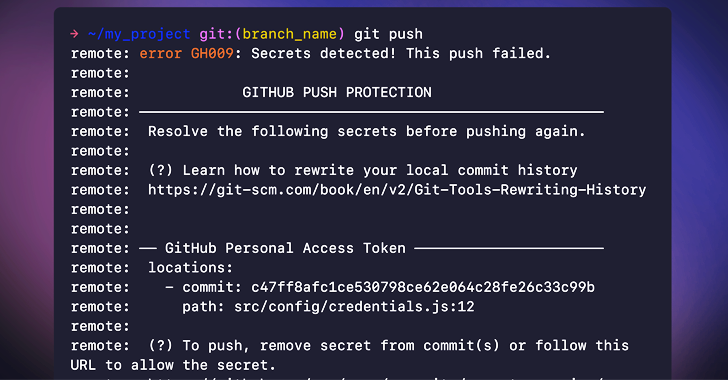
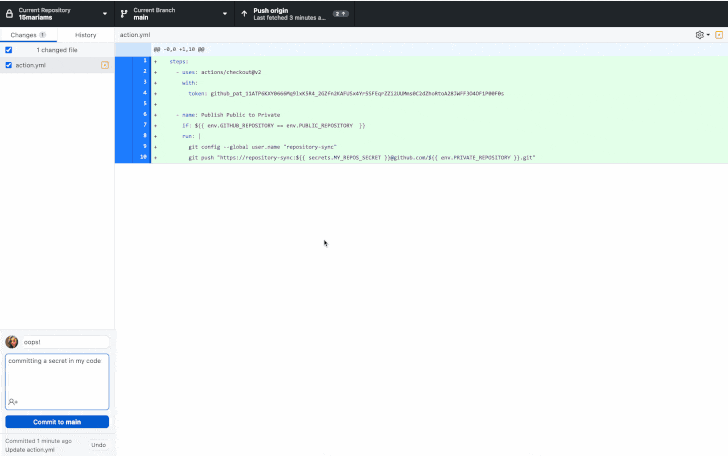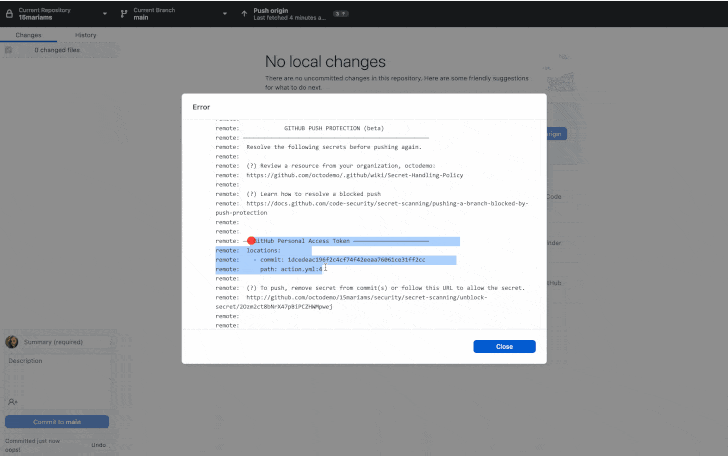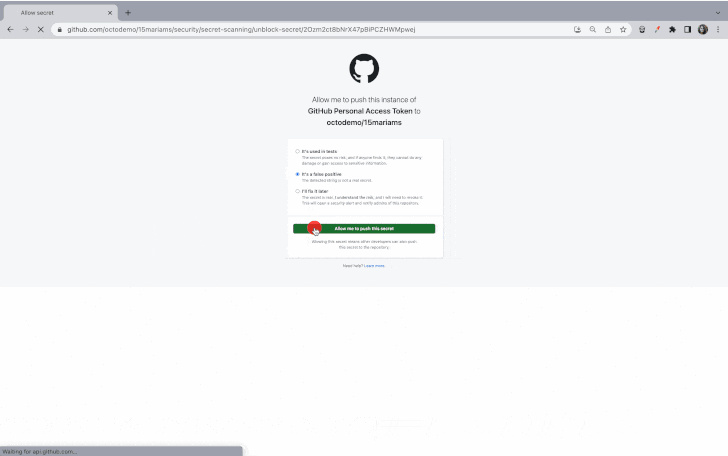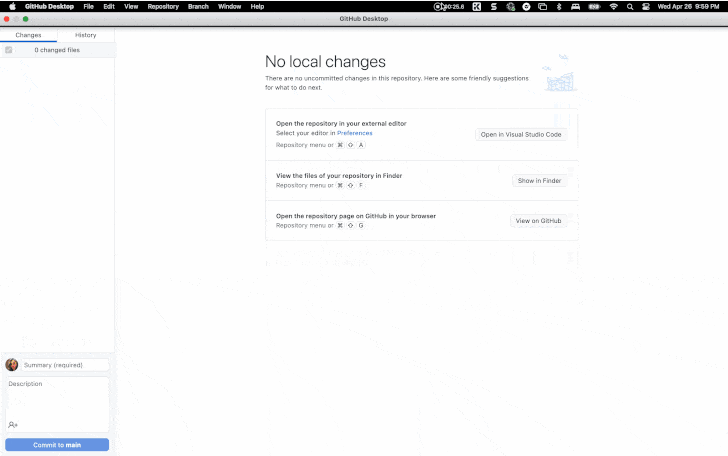
GitHub has announced the general availability of a new security feature called push protection, which aims to prevent developers from inadvertently leaking keys and other secrets in their code.
The Microsoft-owned cloud-based repository hosting platform, which began testing the feature a year ago, said it’s also extending push protection to all public repositories at no extra cost.
The functionality is designed to work hand-in-hand with the existing secret scanning feature, which scans repositories for known secret formats to prevent their fraudulent use and avert potentially serious consequences.
“Push protection prevents secret leaks without compromising the developer experience by scanning for highly identifiable secrets before they are committed,” GitHub said earlier this week.
“When a secret is detected in code, developers are prompted directly in their IDE or command line interface with remediation guidance to ensure that the secret is never exposed.”
While push protection can be bypassed by providing a reason (e.g., testing, false positive, or acceptable risk), repository and organization administrators and security managers will be notified of such events via email.
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Save My Seat!To enable the option, users can head to Settings > Select “Code security and analysis” > Enable “Secret scanning” and “Push protection.”
Push protection, since it went live in April 2022 as a beta, is estimated to have prevented 17,000 accidental secret leaks, saving more than 95,000 hours that would have otherwise been spent revoking, rotating, and remediating the compromised secrets, the company added.
The development comes nearly five months after GitHub made Secret scanning free for all public repositories, enabling users to be notified about leaked secrets in their repositories.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.