The Week in Ransomware – May 19th 2023 – A Shifting Landscape

In the ever-shifting ransomware landscape, we saw new ransomware gangs emerge, threat actors return from a long absence, operations shifting extortion tactics, and a flurry of attacks on the enterprise.
Over the past few weeks, we have reported on new ransomware operations that have emerged in enterprise attacks, including the new Cactus, Akira, RA Group operations.
This week a relatively new operation named Abyss hit L3Harris, a $17 billion defense company, shifting them into the spotlight.
We also learned about MalasLocker, a ransomware operation targeting Zimbra servers since March. The hackers also have an unusual extortion tactic, demanding victims donate to an approved charity to receive a decryptor and prevent a data leak.
Whether or not the ransomware gang will keep to the arrangement or if this is just an interesting marketing campaign is too soon to tell.
As for shifting extortion tactics, a joint FBI and CISA report confirmed that the BianLian ransomware operation has switched to extortion-only attacks after Avast released a decryptor.
We also learned about new attacks and significant developments in previous ones:
- Capita has started to tell its customers to assume that their data has been stolen.
- PharMerica disclosed that a Money Message ransomware attack exposed the data for 5.8 million patients.
- LACROIX announced getting hit by a ransomware attack on May 12th.
- ScanSource finally confirmed that its multi-day outage was due to a ransomware attack.
- LockBit ransomware claimed an attack on the pharmaceutical network Farmalink.
- Looks like Dish Networks paid a ransom, as they say they confirmed the attackers deleted all stolen data.
Finally, researchers and law enforcement released new reports:
- Microsoft warned that the notorious FIN7 threat actors have returned, now using the CLOP ransomware in attacks.
- A new report about researchers going undercover in the Qilin ransomware operation.
- A technical analysis of the new CryptNet ransomware.
Contributors and those who provided new ransomware information and stories this week include: @serghei, @LawrenceAbrams, @PolarToffee, @malwrhunterteam, @DanielGallagher, @Ionut_Ilascu, @demonslay335, @billtoulas, @Seifreed, @BleepinComputer, @fwosar, @VK_Intel, @struppigel, @BrettCallow, @TalosSecurity, @CrowdStrike, @pcrisk, @GroupIB, @zscaler, @MsftSecIntel, and @juanbrodersen.
May 13th 2023
Capita warns customers they should assume data was stolen
Business process outsourcing firm Capita is warning customers to assume that their data was stolen in a cyberattack that affected its systems in early April.
May 15th 2023
Hypervisor Jackpotting, Part 3: Lack of Antivirus Support Opens the Door to Adversary Attacks
In April 2023, for example, CrowdStrike Intelligence identified a new RaaS program named MichaelKors, which provides affiliates with ransomware binaries targeting Windows and ESXi/Linux systems. Other RaaS platforms capable of targeting ESXi environments, such as Nevada ransomware, have also been launched.
New RA Group ransomware targets U.S. orgs in double-extortion attacks
A new ransomware group named ‘RA Group’ is targeting pharmaceutical, insurance, wealth management, and manufacturing firms in the United States and South Korea.
Ransomware gang steals data of 5.8 million PharMerica patients
Pharmacy services provider PharMerica has disclosed a massive data breach impacting over 5.8 million patients, exposing their medical data to hackers.
You’ve been kept in the dark (web): exposing Qilin’s RaaS program
In this blog, we aim to provide a detailed breakdown of the ransomware group – Qilin (aka Agenda ransomware). This group, discovered in August 2022, has been targeting companies in critical sectors with ransomware written in the Rust* and Go languages* (Golang).
Cyber attack contained at LACROIX
LACROIX announces that during the night of Friday 12 May to Saturday 13 May, it intercepted a targeted cyber attack on the French (Beaupréau), German (Willich) and Tunisian (Zriba) sites of the Electronics activity. Measures to secure all the Group’s other sites were immediately taken.
New STOP ransomware variant
PCrisk found a new STOP ransomware variant that appends the .xash extension.
New VoidCrypt ransomware variant
PCrisk found a new VoidCrypt ransomware variant that appends the .cyb extension and drops a ransom note named Dectryption-guide.txt.
New Phobos ransomware variant
PCrisk found a new Phobos ransomware variant that appends the .blackrock extension.
May 16th 2023
Russian ransomware affiliate charged with attacks on critical infrastructure
The U.S. Justice Department has filed charges against a Russian citizen named Mikhail Pavlovich Matveev (also known as Wazawaka, Uhodiransomwar, m1x, and Boriselcin) for involvement in three ransomware operations that targeted victims across the United States.
Technical Analysis of CryptNet Ransomware
Zscaler ThreatLabz has been tracking a new ransomware group known as CryptNet that emerged in April 2023. The group claims to exfiltrate data prior to performing file encryption and hosts a data leak site hosted on a Tor hidden service that currently contains two victims.
New STOP ransomware variants
PCrisk found new STOP ransomware variants that append the .xatz and .xaro extensions.
New MedusaLocker ransomware variant
PCrisk found a new MedusaLocker ransomware variant that appends the .olsavelock31 (the number may differ) extension and drops a ransom note named How_to_back_files.html.
May 17th 2023
MalasLocker ransomware targets Zimbra servers, demands charity donation
A new ransomware operation is hacking Zimbra servers to steal emails and encrypt files. However, instead of demanding a ransom payment, the threat actors claim to require a donation to charity to provide an encryptor and prevent data leaking.
FBI confirms BianLian ransomware switch to extortion only attacks
A joint Cybersecurity Advisory from government agencies in the U.S. and Australia, and published by the Cybersecurity and Infrastructure Security Agency (CISA,) is warning organizations of the latest tactics, techniques, and procedures (TTPs) used by the BianLian ransomware group.
ScanSource says ransomware attack behind multi-day outages
Technology provider ScanSource has announced it has fallen victim to a ransomware attack impacting some of its systems, business operations, and customer portals.
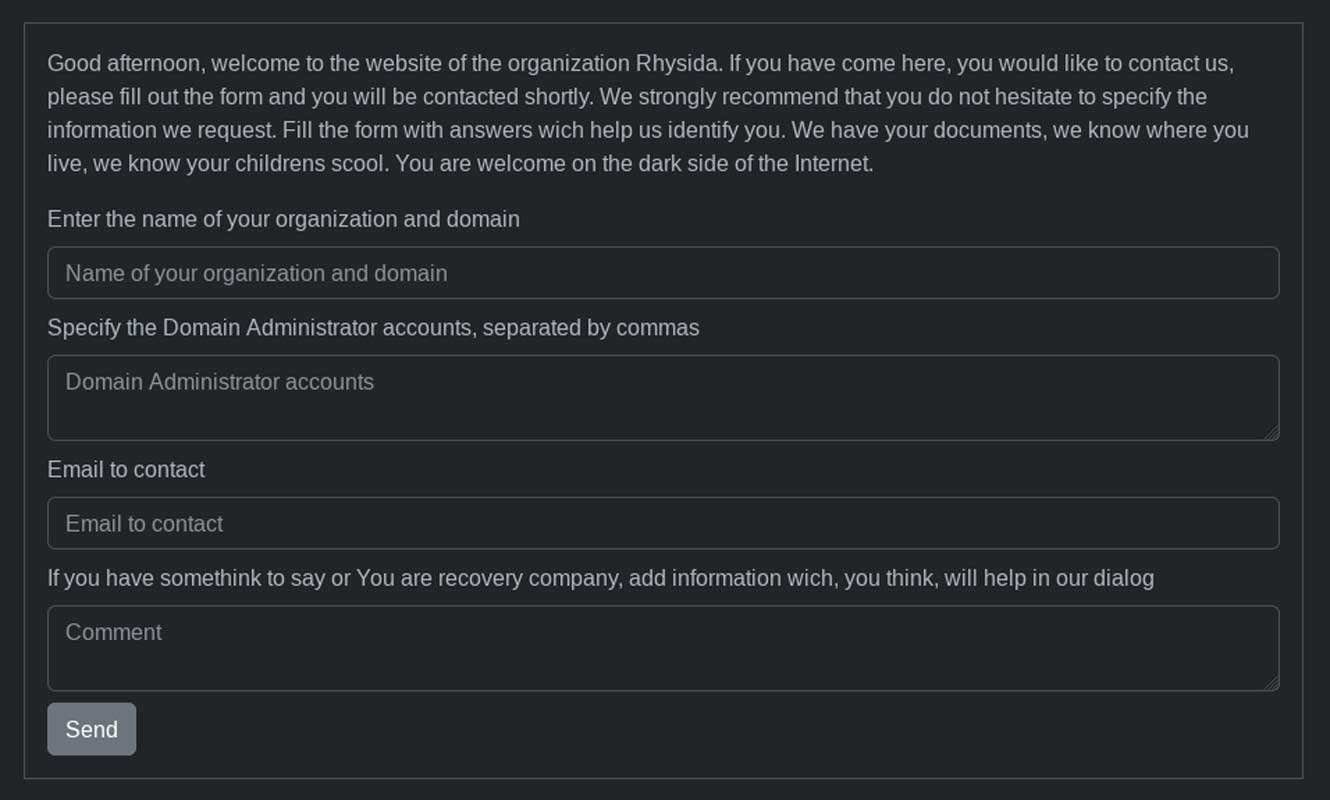
New Rhysida ransomware
MalwareHunterTeam found the new Rhysida ransomware operation.

May 18th 2023
Cyber ??attack on pharmacies: hackers give a month to pay the ransom or publish the stolen information
Lockbit , the group of cybercriminals that carried out the attack against the Farmalink prescription drug sales system , gave a period of about one month to negotiate the payment of a ransom and return the stolen information. After that period, they will publish the data.
New Snatch ransomware variant
PCrisk found a new Snatch ransomware variant that appends the .adfuhbazi extension and drops a ransom note named HOW TO RESTORE YOUR ADFUHBAZI FILES.TXT.
May 19th 2023
Dish Network likely paid ransom after recent ransomware attack
Dish Network, an American television provider, most likely paid a ransom after being hit by a ransomware attack in February based on the wording used in data breach notification letters sent to impacted employees.
Microsoft: Notorious FIN7 hackers return in Clop ransomware attacks
A financially motivated cybercriminal group known as FIN7 resurfaced last month, with Microsoft threat analysts linking it to attacks where the end goal was the deployment of Clop ransomware payloads on victims’ networks.
New AlphaWare ransomware
PCrisk found a new AlphaWare ransomware that appends the .Alphaware extension and drops a ransom note named readme.txt.
That’s it for this week! Hope everyone has a nice weekend!
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below




To keep up to date follow us on the below channels.





![[KILLSEC] - Ransomware Victim: BluMed Health 10 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
