Chinese hackers use DNS-over-HTTPS for Linux malware communication

The Chinese threat group ‘ChamelGang’ infects Linux devices with a previously unknown implant named ‘ChamelDoH,’ allowing DNS-over-HTTPS communications with attackers’ servers.
The particular threat actor was first documented back in September 2021 by Positive Technologies; however, the researchers only focused on the Windows toolkit.
A report published yesterday by Stairwell and shared with BleepingComputer describes a new Linux implant written in C++ that expands the threat actor’s intrusion arsenal and, by extension, the attackers’ indicators of compromise.
The link between ChamelGang and the new Linux malware is based on a domain previously associated with the threat actor and a custom privilege elevation tool observed by Positive Technologies in past ChamelGang campaigns.
DNS-over-HTTPS for malware communication
The DNS (domain name system) protocol is used by software and operating systems to resolve human-readable hostnames into IP addresses, which are then used to make network connections.
However, DNS queries are sent as unencrypted, plain text, allowing organizations, ISPs, and others to monitor the DNS requests.
As this is considered a privacy risk and allows governments to censor the Internet, a new DNS protocol named DNS-over-HTTPS was created to encrypt DNS queries so they cannot be snooped on.
However, this is a double-edged sword, as malware can use it as an effective encrypted communication channel, making it harder for security software to monitor for malicious network communication.
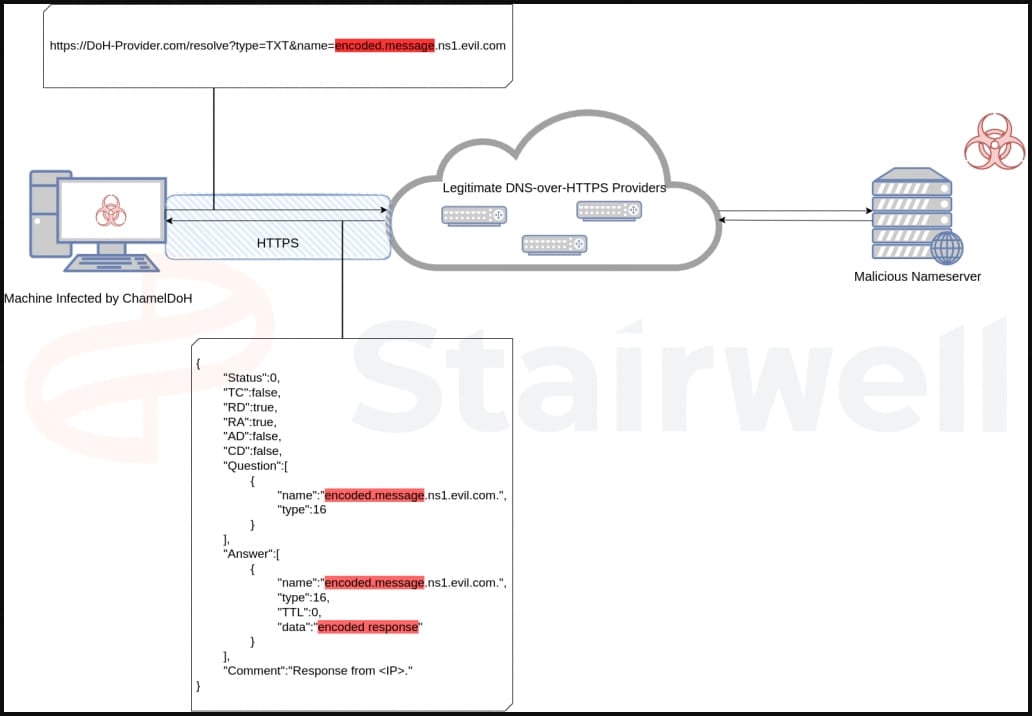
In the case of ChamelDoH, DNS-over-HTTPS provides encrypted communication between an infected device and the command and control server, making malicious queries indistinguishable from regular HTTPS traffic.
Additionally, DoH can help bypass local DNS servers by using DoH-compatible servers provided by reputable organizations, which was not seen in this case.
Finally, because the DNS requests use legitimate DoH servers from Google and Cloudflare, blocking them is practically impossible without impacting legitimate traffic.
ChamelDoH uses two keys stored in its JSON configuration, “ns_record” and “doh,” to get C2 hostnames and a list of legitimate DoH cloud providers that can be abused for performing DoH queries.
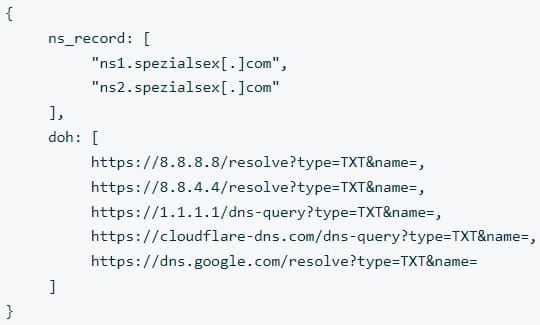
All malware’s communications are encrypted using AES128 and a modified base64 encoding that contains substitutes for non-alphanumeric characters. The transmitted data is then appended as hostnames to the listed malware command and control servers.
This modification allows the malware to issue TXT requests for domains containing the encoded command and control server (C2) communications, obscuring the nature of those requests and reducing the likelihood of being detected.
For example, when querying the TXT record, a DoH query from the malware would use <encoded_data>.ns2.spezialsec[.].com. The malicious name server receiving the query would then extract and decrypt the encoded portion to receive the exfiltrated data from the infected device.
The C2 would respond with an encoded TXT record containing the commands the malware should execute on the infected device.
Upon execution, the malware will gather basic data about its host, including the name, IP address, CPU architecture, and system version, and generate a unique ID.
Stairwell researchers found that ChamelDoH supports the following commands that its operators can issue remotely via the TXT records received in DNS-over-HTTPS requests:
- run – Execute a file/shell command
- sleep – Set the number of seconds until the next check-in
- wget – Download a file from a URL
- upload – Read and upload a file
- download – Download and write a file
- rm – Delete a file
- cp – Copy a file to a new location
- cd – Change the working directory
Stairwell’s analysis showed that ChamelDoH was first uploaded to VirusTotal in December 2022.
By the time of writing this, it is not flagged as malicious by any of the platform’s AV engines.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





