Microsoft links data wiping attacks to new Russian GRU hacking group

Microsoft has linked a threat group it tracks as Cadet Blizzard since April 2023 to Russia’s Main Directorate of the General Staff of the Armed Forces (also known as GRU).
The company previously connected this new GRU hacking group with the destructive WhisperGate data-wiping attacks in Ukraine that started on January 13, 2022, more than a month before the Russian invasion of Ukraine in February 2022.
Cadet Blizzard was also behind the defacement of Ukrainian websites in early 2022 and several hack-and-leak operations that were promoted on a low-activity Telegram channel known as ‘Free Civilian.’
The group is believed to have started operations in 2020, prioritizing targeting of government services, law enforcement, non-profit/non-governmental organizations, IT service providers/consulting, and emergency services in Ukraine.
“Microsoft assesses that Cadet Blizzard operations are associated with the Russian General Staff Main Intelligence Directorate (GRU) but are separate from other known and more established GRU-affiliated groups such as Forest Blizzard (STRONTIUM) and Seashell Blizzard (IRIDIUM),” Microsoft said.
“A month before Russia invaded Ukraine, Cadet Blizzard foreshadowed future destructive activity when it created and deployed WhisperGate, a destructive capability that wipes Master Boot Records (MBRs), against Ukrainian government organizations.”
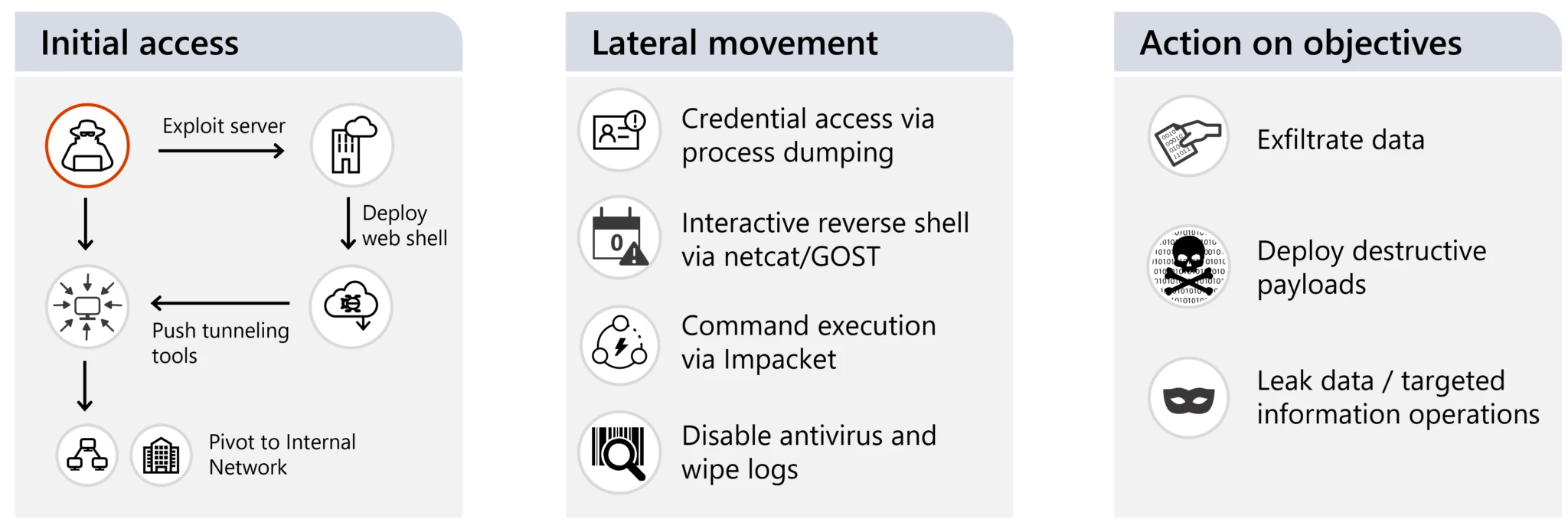
Microsoft says that Cadet Blizzard’s attacks have a relatively lower success rate when compared to other GRU-affiliated hacking groups like APT28 (Strontium, Fancy Bear) and Sandworm (Iridium).
While Cadet Blizzard fell off the radar after June 2022, the group resurfaced in early 2023, with its more recent cyber operations seeing occasional success. However, they still failed to match the impact their GRU counterparts’ attacks achieved.
Since the 2022 defacements and data-wiping attacks and starting in February 2023, the GRU hacking group has been behind a barrage of attacks targeting Ukrainian government organizations and IT providers.
For instance, Redmond linked at least one incident in a series of breaches reported by the Computer Emergency Response Team of Ukraine (CERT-UA) in February, saying that it found evidence of backdoors planted by Russian state hackers on multiple government websites following breaches going as far back as December 2021.
CERT-UA linked the attacks to Ember Bear, a group that it believes has been active since at least March 2021, with attacks targeting Ukrainian organizations with information stealers, backdoors, and data wipers camouflaged as ransomware primarily delivered via phishing emails.
“Cadet Blizzard is active seven days a week and has conducted its operations during its primary targets’ off-business hours when its activity is less likely to be detected,” said Tom Burt, Microsoft’s Corporate Vice President of Customer Security & Trust.
“In addition to Ukraine, it also focuses on NATO member states involved in providing military aid to Ukraine.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![Cobalt Strike Beacon Detected - 120[.]27[.]235[.]78:81 9 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
![[QILIN] - Ransomware Victim: 1sthealthinc[.]com 13 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)