Experts Uncover Year-Long Cyber Attack on IT Firm Utilizing Custom Malware RDStealer
A highly targeted cyber attack against an East Asian IT company involved the deployment of a custom malware written in Golang called RDStealer.
“The operation was active for more than a year with the end goal of compromising credentials and data exfiltration,” Bitdefender security researcher Victor Vrabie said in a technical report shared with The Hacker News.
Evidence gathered by the Romanian cybersecurity firm shows that the campaign started in early 2022. The target was an unspecified IT company located in East Asia.
In the early phases, the operation relied on readily available remote access trojans like AsyncRAT and Cobalt Strike, before transitioning to bespoke malware in late 2021 or early 2022 in a bid to thwart detection.
A primary evasion tactic concerns the use of Microsoft Windows folders that are likely to be excluded from scanning by security software (e.g., System32 and Program Files) to store the backdoor payloads.
One of the sub-folders in question is “C:\Program Files\Dell\CommandUpdate,” which is the directory for a legitimate Dell application called Dell Command | Update.
Bitdefender said all the machines infected over the course of the incident were manufactured by Dell, suggesting that the threat actors deliberately chose this folder to camouflage the malicious activity.
This line of reasoning is bolstered by the fact that the threat actor registered command-and-control (C2) domains such as “dell-a[.]ntp-update[.]com” with the goal of blending in with the target environment.
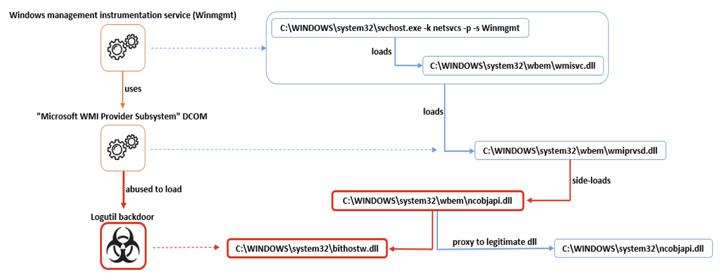
The intrusion set is characterized by the use of a server-side backdoor called RDStealer, which specializes in gathering clipboard content and keystroke data from the host.
But what makes it stand out is its capability to “monitor incoming RDP [Remote Desktop Protocol] connections and compromise a remote machine if client drive mapping is enabled.”
Thus when a new RDP client connection is detected, commands are issued by RDStealer to exfiltrate sensitive data, such as browsing history, credentials, and private keys from apps like mRemoteNG, KeePass, and Google Chrome.
“This highlights the fact that threat actors actively seek credentials and saved connections to other systems,” Bitdefender’s Marin Zugec said in a second analysis.
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
Join the WebinarWhat’s more, the connecting RDP clients are infected with another Golang-based custom malware known as Logutil to maintain a persistent foothold on the victim network using DLL side-loading techniques and facilitate command execution.
Not much is known about the threat actor other than the fact that it has been active dating back to at least 2020.
“Cybercriminals continually innovate and explore novel methods to enhance the reliability and stealthiness of their malicious activities,” Zugec said.
“This attack serves as a testament to the increasing sophistication of modern cyber attacks, but also underscores the fact that threat actors can leverage their newfound sophistication to exploit older, widely adopted technologies.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below




To keep up to date follow us on the below channels.







![[APT73] - Ransomware Victim: www[.]fpj[.]com[.]py 9 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
