Facebook Messenger phishing wave targets 100K business accounts per week

Hackers use a massive network of fake and compromised Facebook accounts to send out millions of Messenger phishing messages to target Facebook business accounts with password-stealing malware.
The attackers trick the targets into downloading a RAR/ZIP archive containing a downloader for an evasive Python-based stealer that grabs cookies and passwords stored in the victim’s browser.
In a new report by Guardio Labs, researchers warn that roughly one out of seventy targeted accounts is ultimately compromised, translating to massive financial losses.
Facebook Messenger phishing
The hackers start by sending Messenger phishing messages to Facebook business accounts pretending to be copyright violations or requests for more information about a product.
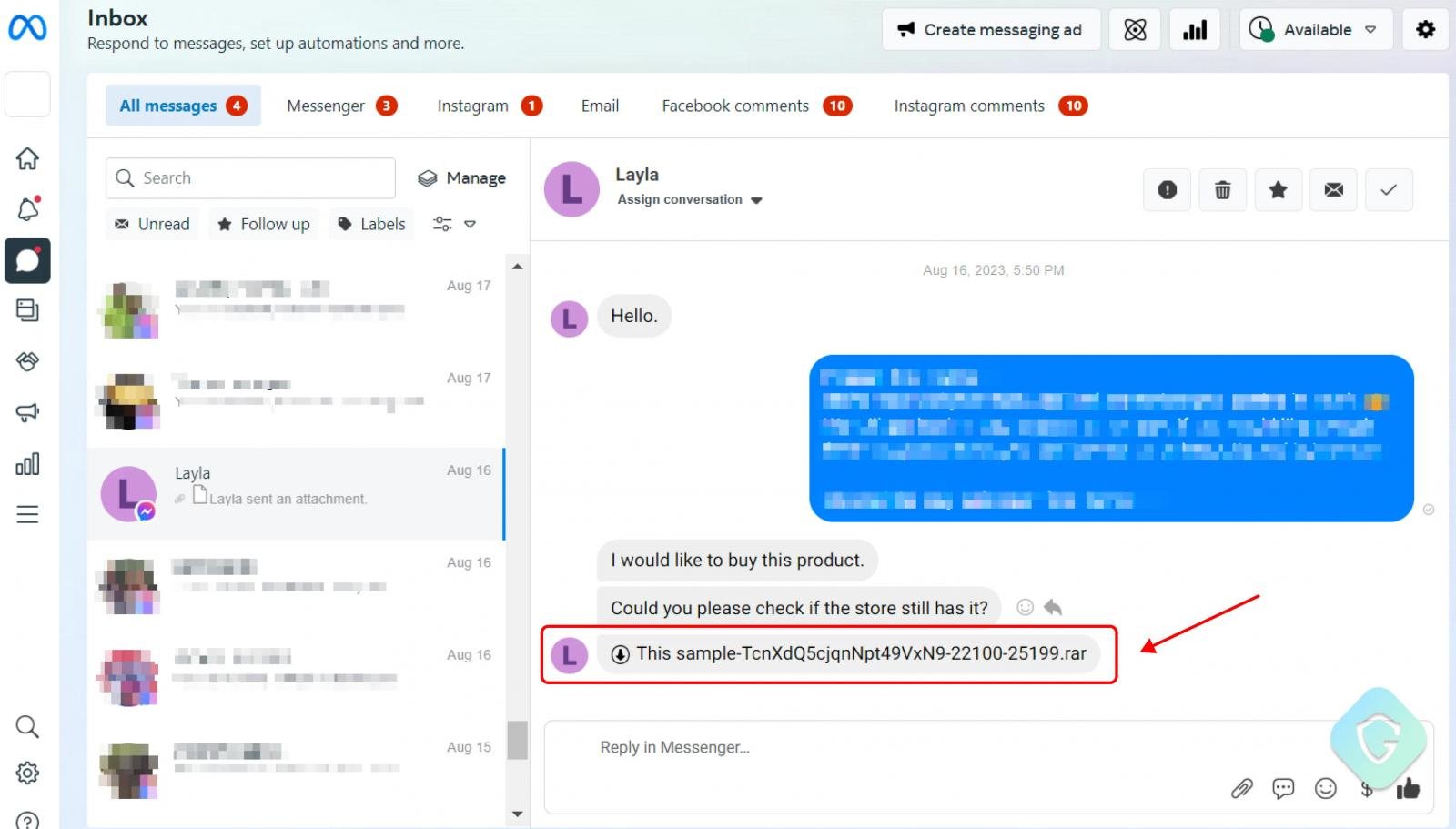

The attached archive contains a batch file that, if executed, fetches a malware dropper from GitHub repositories to evade blocklists and minimize distinctive traces.
Along with the payload (project.py), the batch script also fetches a standalone Python environment required by the infostealing malware and adds persistence by setting the stealer binary to execute at system startup.
The project.py file features five layers of obfuscation, making it challenging for AV engines to catch the threat.


The malware collects all the cookies and login data stored on the victim’s web browser into a ZIP archive named ‘Document.zip’. It then sends the stolen information to the attackers via Telegram or Discord bot API.
Finally, the stealer wipes all cookies from the victim’s device to log them out of their accounts, giving the scammers enough time to hijack the newly compromised account by changing the passwords.
As it can take a while for social media companies to respond to emails about hijacked accounts, it gives the threat actors time to conduct fraudulent activities with the hacked accounts.
Scale of the campaign
Although the attack chain isn’t novel, the scale of the campaign observed by Guardio Labs is alarming.
The researchers report roughly 100,000 phishing messages per week, sent mainly to Facebook users in North America, Europe, Australia, Japan, and Southeast Asia.
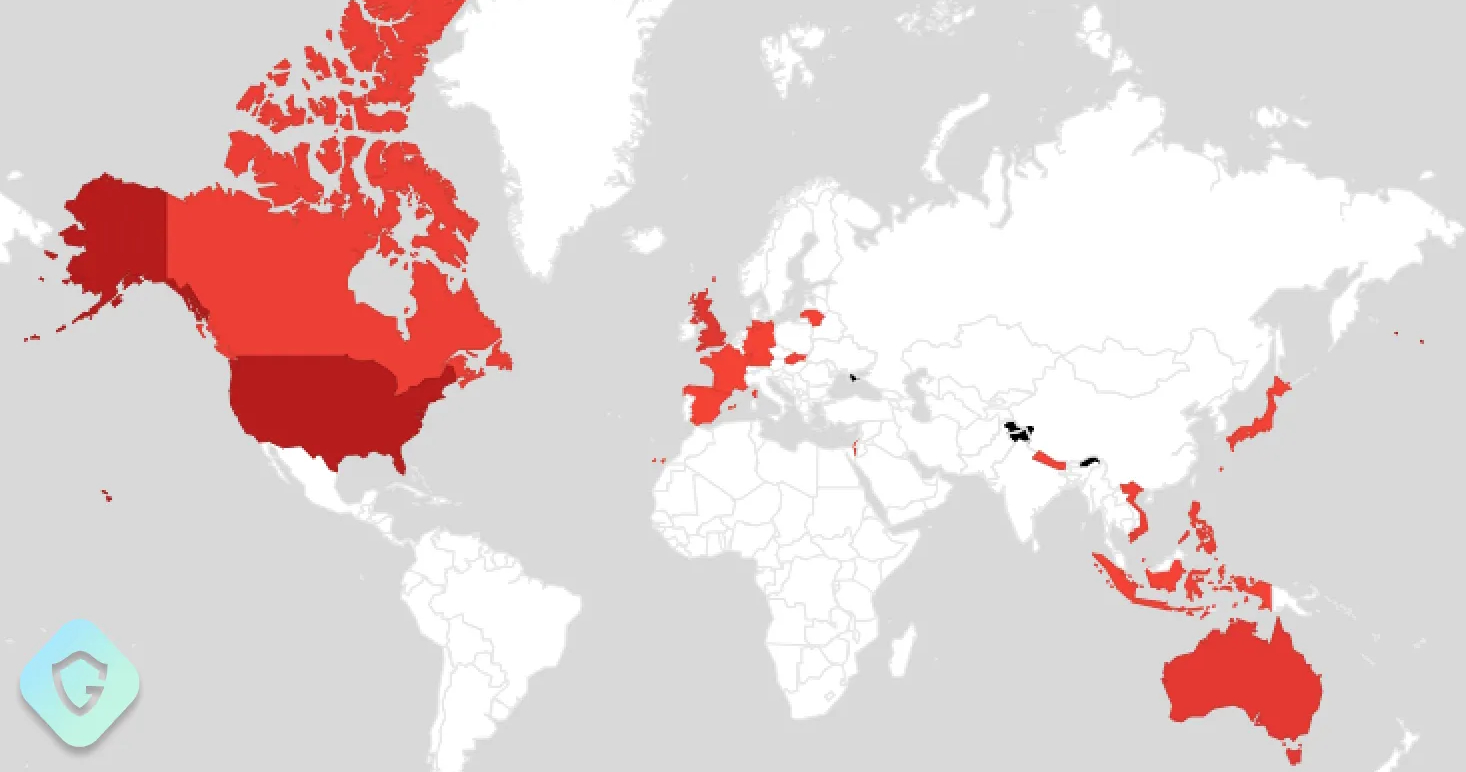
Guardio Labs reports that the scale of the campaign is such that approximately 7% of all of Facebook’s business accounts have been targeted, with 0.4% having downloaded the malicious archive.
To be infected by the malware, the users still have to execute the batch file, so the number of hijacked accounts is unknown, but it could be significant.
Linked to Vietnamese hackers
Guardio attributes this campaign to Vietnamese hackers due to strings in the malware and the use of the “Coc Coc” web browser, which the researchers say is popular in Vietnam.
“This python stealer reveals the Vietnamese origin of these threat actors,’ explains Guardio.
“The message “Thu Spam lần thứ” which is sent to the Telegram bot appended with a counter of execution time, translates from Vietnamese as “Collect Spam for the X time”.”
Vietnamese threat groups have targeted Facebook with large-scale campaigns this year, monetizing stolen accounts mainly by reselling them via Telegram or dark web markets.
In May 2023, Facebook announced it had disrupted a Vietnam-originated campaign that deployed a new info-stealer malware named ‘NodeStealer’ that snatched browser cookies.
In April 2023, Guardio Labs reported again about a Vietnamese threat actor who abused Facebook’s Ads service to infect approximately half a million users with info-stealing malware.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[RANSOMHUB] - Ransomware Victim: allconstructiongroupwv[.]com 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)