New ‘MetaStealer’ malware targets Intel-based macOS systems

A new information stealer malware named ‘MetaStealer’ has appeared in the wild, stealing a wide variety of sensitive information from Intel-based macOS computers.
MetaStealer, not to be confused with the ‘META’ info-stealer that saw some popularity last year, is a Go-based malware capable of evading Apple’s built-in antivirus tech XProtect, targeting business users.
SentinelOne reports it has been tracking the malware for the past couple of months, seeing an unusual involvement of social engineering in its distribution.
Although the malware has some similarities with Atomic Stealer, another Go-based macOS targeting info-stealer, the code overlap is limited, and the delivery methods are different.
Therefore, SentinelOne concludes that MetaStealer is a separate operation.
Arrival on macOS systems
SentinelOne found a malware sample on VirusTotal with a comment stating the MetaStealer threat actors are contacting businesses and impersonating the company’s clients to distribute the malware.
“I was targeted by someone posing as a design client, and didn’t realize anything was out of the ordinary. The man I’d been negotiating with on the job this past week sent me a password protected zip file containing this DMG file, which I thought was a bit odd,” reads the VirusTotal comment.
“Against my better judgement I mounted the image to my computer to see its contents. It contained an app that was disguised as a PDF, which I did not open and is when I realized he was a scammer.”
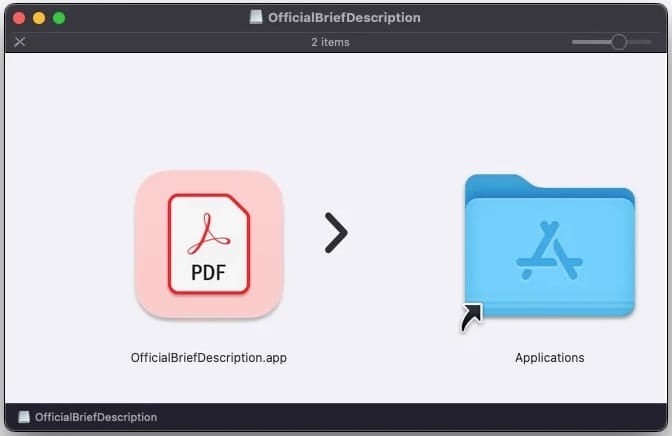
Attached to the phishing emails are disk image files that, when mounted on the filesystem, contain deceptively named executables that appear as PDF files to trick the victim into opening them.

SentinelOne has observed DMGs named after Adobe software or client work, including the following:
- Advertising terms of reference (MacOS presentation).dmg
- CONCEPT A3 full menu with dishes and translations to English.dmg
- AnimatedPoster.dmg
- Brief_Presentation-Task_Overview-(SOW)-PlayersClub.dmg
- AdobeOfficialBriefDescription.dmg
- Adobe Photoshop 2023 (with AI) installer.dmg
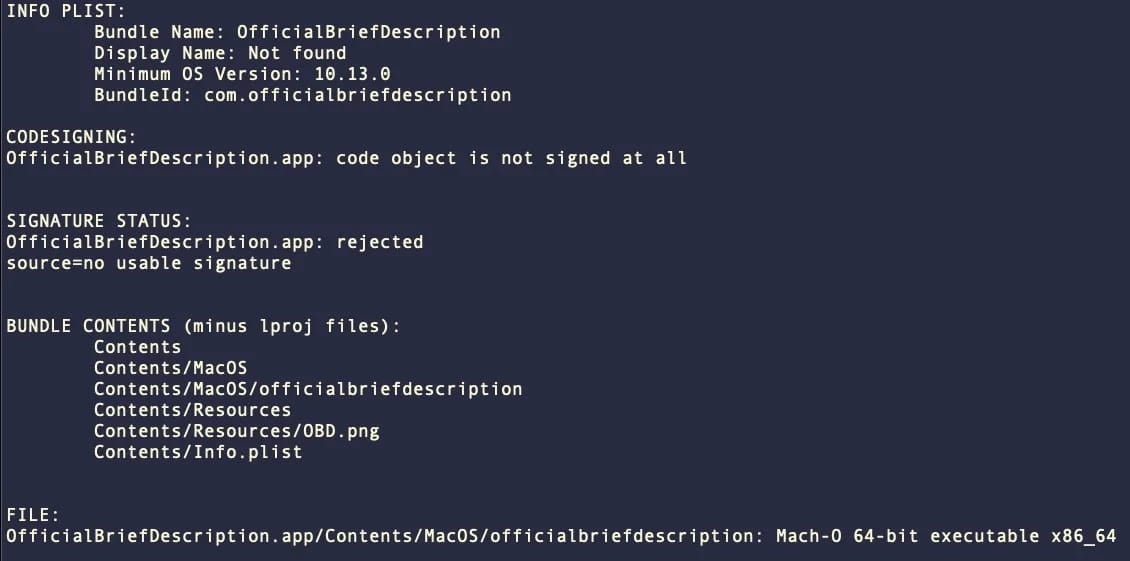
The malware’s application bundles contain the bare essentials, namely an Info.plist file, a Resources folder with an icon image, and a macOS folder with the malicious Mach-O executable.
None of the samples examined by SentinelOne were signed, despite some versions featuring an Apple Developer ID.

MetaStealer capabilities
MetaStealer attempts to steal information stored on the compromised systems, including passwords, files, and app data, and then attempts to exfiltrate them via TCP over port 3000.
Specifically, the malware features functions allow for exfiltrating the keychain and extracting saved passwords, stealing files from the system, and targeting Telegram and Meta (Facebook) services.
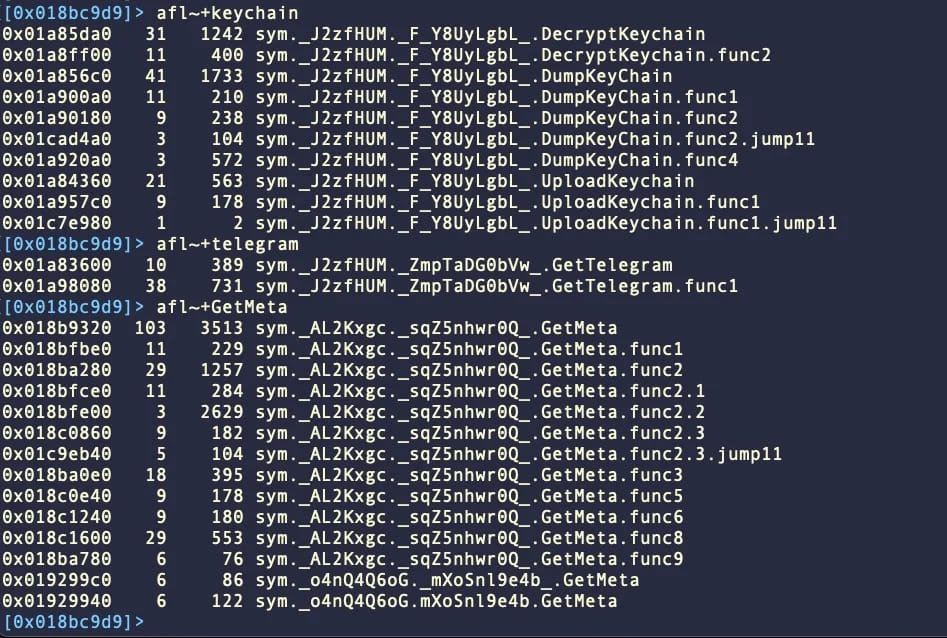
The keychain is a system-level password management system for macOS, managing credentials for websites, applications, WiFi networks, certificates, encryption keys, credit card information, and even private notes.
Hence, the exfiltration of keychain contents is a powerful feature that could give the attackers access to sensitive data.
In its current version, MetaStealer only runs on Intel x86_64 architecture, which means it cannot compromise macOS systems running on Apple Silicon processors (M1, M2) unless the victim uses Rosetta to run the malware.
This mitigates the threat and limits it to an ever-reducing number of potential victims as Intel-based Apple computers are being phased out.
However, MetaStealer might release a new version that adds native support for Apple Silicon, so it’s a threat to watch out for.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[RANSOMHUB] - Ransomware Victim: Jornstax[.]com 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
