‘Redfly’ hackers infiltrated power supplier’s network for 6 months

An espionage threat group tracked as ‘Redfly’ hacked a national electricity grid organization in Asia and quietly maintained access to the breached network for six months.
These new findings come from Symantec, who found evidence of ShadowPad malware activity in the organization’s network between February 28 and August 3, 2023, along with keyloggers and specialized file launchers.
Although ShadowPad is a widely available trojan that multiple APT groups use, Symantec tracks the recent attacks separately, reporting that Redfly appears to have an exclusive focus on critical national infrastructure.
Redfly’s toolset
The ShadowPad variant seen in the attacks masquerades its components (exe and dll) as VMware files, dropping them on the victim’s filesystem.
The program also achieves persistence by creating services named after VMware again, set to launch the malicious executable and DLL upon system boot.

In general, ShadowPad is a versatile modular RAT that supports data exfiltration to the C2, keystroke recording, file searching and file operations, and remote command execution.
Multiple APTs use it because it is not associated with a single actor, making attribution and tracking harder for analysts.
In the observed attacks, Redfly used a separate keylogging tool that captured keystrokes in log files on the breached system, which the attackers retrieved manually.
Another tool the espionage hackers use is Packerloader, employed for loading and executing shellcode inside AES encrypted files capable of evading AV detection.
The attackers were seen using this tool to execute code that modified a driver file’s permissions, subsequently used for creating credential dumps in the Windows registry (for future retrieval) and wiping Windows security event logs.
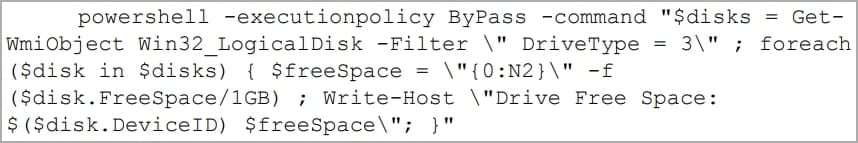
Redfly also uses PowerShell to execute commands that help them gather details about specific storage devices on the compromised system.

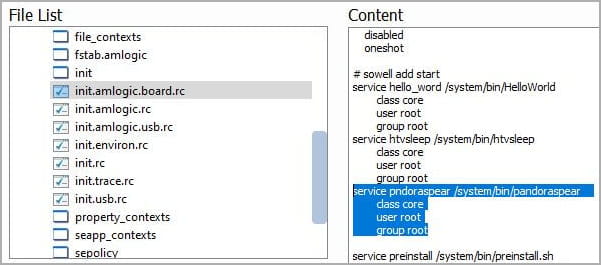
For lateral movement, the hackers use DLL side-loading and legitimate executables, scheduled tasks executing legitimate binaries, and stolen credentials.
Redfly also employed renamed versions of known tools, like ProcDump, to dump credentials from LSASS and then use them to authenticate on adjacent systems.
The lengthy dwell period seen in this attack is characteristic of espionage actors who infect systems and keep a low profile to collect as much intelligence as possible.
While the attackers’ intent to disrupt the power supply remains uncertain, the potential risk poses a significant threat.
“Attacks against CNI targets are not unprecedented. Almost a decade ago, Symantec uncovered the Russian-sponsored Dragonfly group’s attacks against the energy sector in the U.S. and Europe,” concluded Symantec’s report.
“More recently, the Russian Sandworm group mounted attacks against the electricity distribution network in Ukraine that were directed at disrupting electricity supplies.”
Such disruption could have resulted in extensive damage to the energy provider’s customers and profound economic repercussions for the entire nation.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


