ShadowSyndicate hackers linked to multiple ransomware ops, 85 servers

Security researchers have identified infrastructure belonging to a threat actor now tracked as ShadowSyndicate, who likely deployed seven different ransomware families in attacks over the past year.
Group-IB analysts working together with Bridewell and independent researcher Michael Koczwara attribute with various degrees of confidence ShadowSyndicate’s use of the Quantum, Nokoyawa, BlackCat/ALPHV, Clop, Royal, Cactus, and Play ransomware in multiple breaches observed since July 2022.
Based on their findings, researchers believe that the threat actor could be an initial access broker (IAB), although evidence suggests that ShadowSyndicate is an affiliate to multiple ransomware operations.
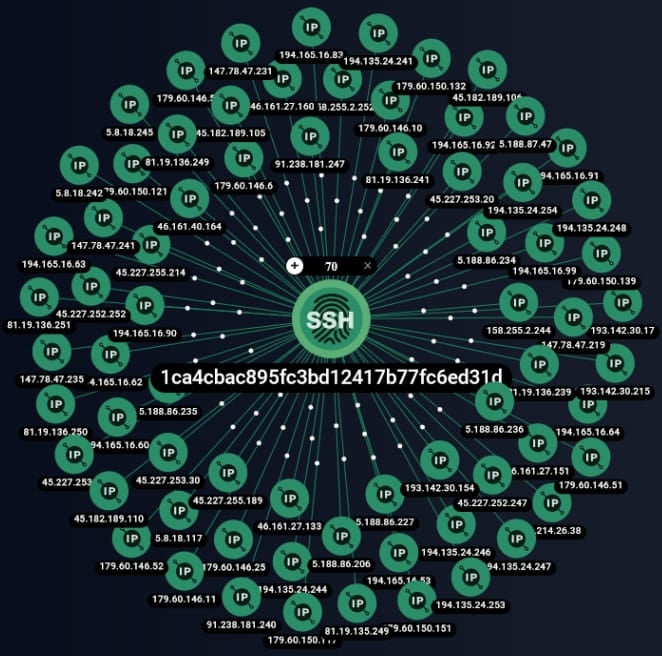
The researchers base their conclusions on a distinct SSH fingerprint they discovered on 85 IP servers, most of them tagged as Cobalt Strike command and control machines.
“We have dubbed the threat actor that uses the SSH fingerprint 1ca4cbac895fc3bd12417b77fc6ed31d ShadowSyndicate (previous name Infra Storm)” – Group-IB
The analysts first saw the fingerprint on July 16, 2022, and it was still in use in August 2023.

ShadowSyndicate arsenal
The team of researchers relied on various tools for their investigation, which included discovery engines like Shodan and Censys, along with various OSINT techniques. This allowed them to discover an extensive ShadowSyndicate activity footprint.
Looking at the ShadowSyndicate servers identified based on the SSH fingerprint, the researchers “came across eight different Cobalt Strike watermarks [license keys].”
The eight Cobalt Strike servers communicated with Cactus, Royal, Quantum, Nokoyawa, Play, Clop, and BlackCat/ALPHV ransomware deployed on various victim networks.
The researchers also discovered Cobalt Strike configurations deployed on two servers, but only one of them on a machine featuring the ShadowSyndicate SSH fingerprint.
In some attacks, ShadowSyndicate used the Sliver penetration tool that was previously regarded as a potential replacement for Cobalt Strike.
Other tools seen in ShadowSyndicate attacks include the IcedID malware loader, the Matanbuchus MaaS loader, and the Meterpreter Metasploit payload.
Server analysis
The analysts tested the hypothesis that all 85 servers with the same SSH key fingerprint linked to ShadowSyndicate are connected to a single hosting provider but found 18 different owners, 22 distinct network names, and 13 different locations.

Analysis of Cobalt Strike C2 parameters like detection date, watermarks, or sleep time settings helped produce high-confidence evidence that links ShadowSyndicate to Quantum, Nokoyawa, and ALPHV/BlackCat ransomware.
Specifically, the analysts linked the servers to a Quantum attack from September 2022, three Nokoyawa attacks from Q4 2022 and April 2023, and an ALPHV attack from February 2023.
Group-IB and the mentioned collaborating parties has found additional evidence that connects ShadowSyndicate with less confidence to Ryuk, Conti, Trickbot, Royal, Clop, and Play malware operations.
For Clop particularly, Group-IB’s report mentions that at least 12 IP addresses formerly linked to the notorious ransomware operators were transferred to ShadowSyndicate since August 2022 and are now utilized for Cobalt Strike.
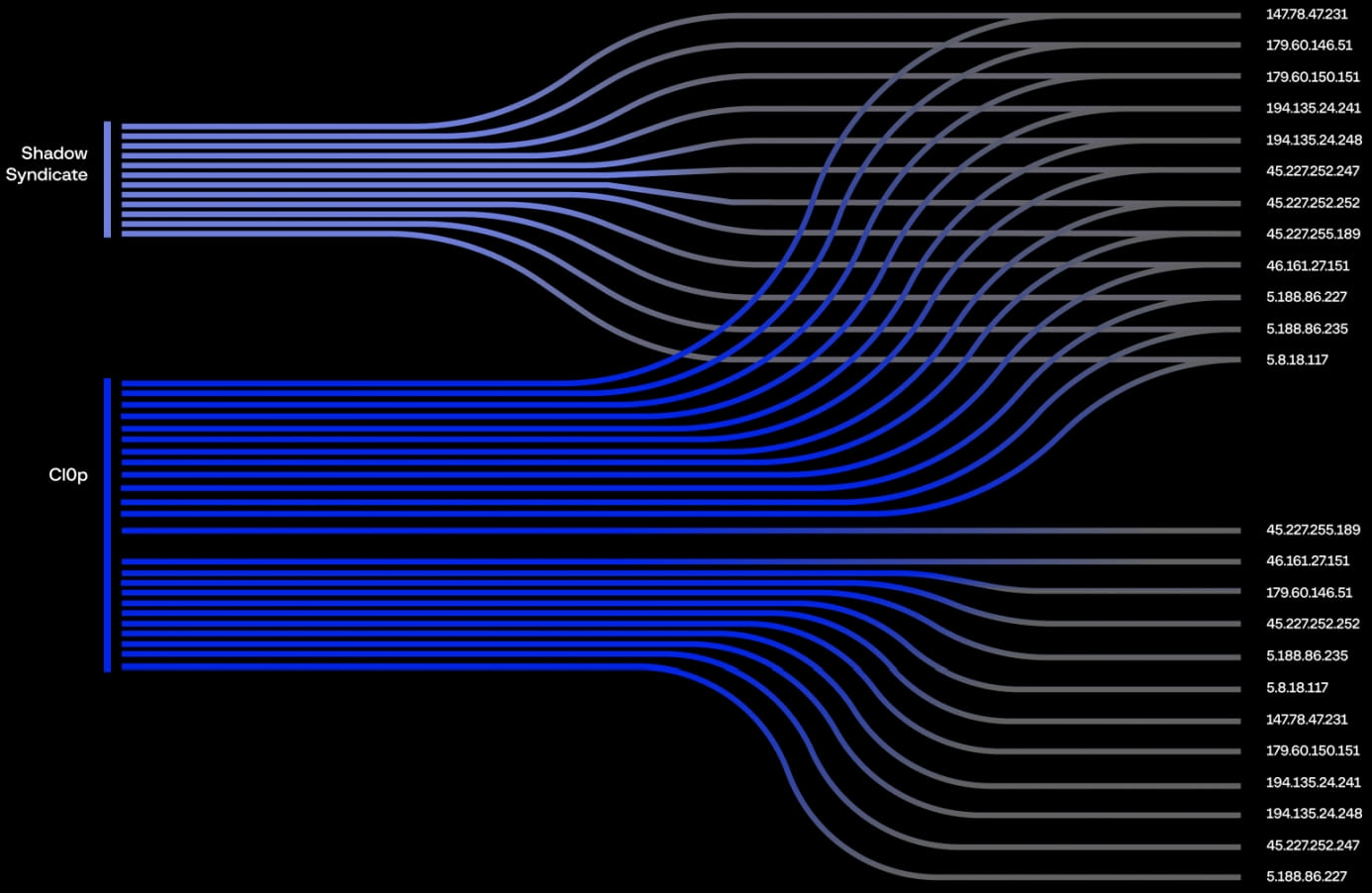
Despite the many findings that suggest a potential connection, a high-confidence direct link between ShadowSyndicate and Clop remains elusive.
Group-IB’s intelligence experts conclude that ShadowSyndicate is likely an affiliate working with various ransomware-as-a-service (RaaS) operations. However, additional evidence is needed to support this theory.
Nevertheless, this work is crucial in identifying and combating cybercrime, and in this spirit, the cyberintelligence firm invites external researchers to openly collaborate with them and help uncover the remaining obscure parts.
For details that could help defenders detect and attribute ShadowSyndicate activity, Group-IB has published a report today with technical data from their research.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

