SolarWinds advanced cyberattack: What happened and what to do now
Over the weekend we learned more about the sophisticated attack that compromised security firm FireEye, the US Treasury and Commerce departments and likely many more victims.
Threat actors hacked into IT company SolarWinds in order to use its software channel to push out malicious updates onto 18,000 of its Orion platform customers. This scenario, referred to as a supply-chain attack, is perhaps the most devious and difficult to detect as it relies on software that has already been trusted and that can be widely distributed at once.
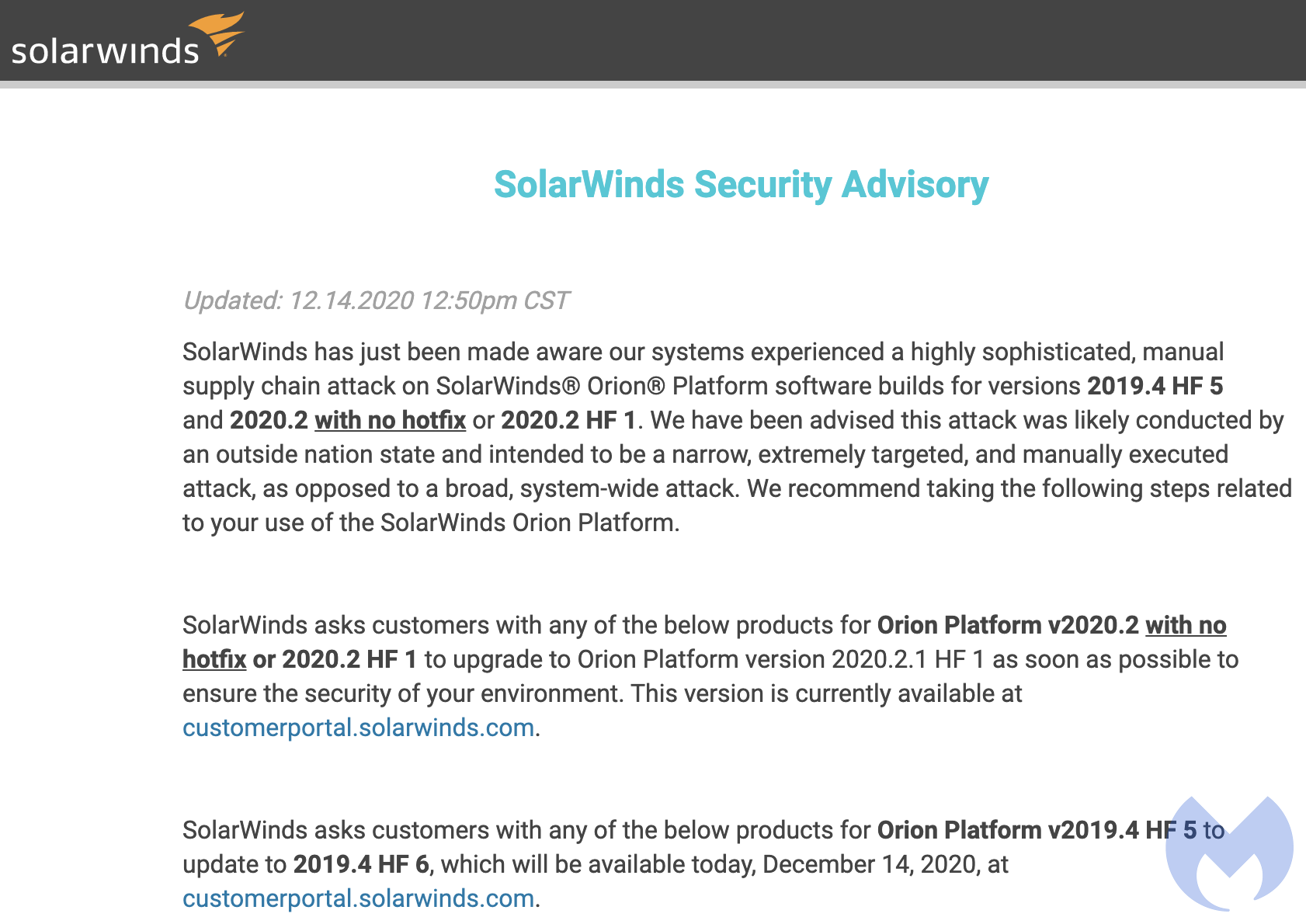

The Department of Homeland Security has issued an emergency directive to order all federal agencies to take immediate steps in putting affected SolarWinds Orion products offline and reporting back any incident by Monday.
We do know that the threat actors were in for a much bigger prize than the offensive tools stolen from security firm FireEye, although this incident helped to uncover a very advanced operation with deep ramifications. As this story is still unfolding we will keep our customers informed of any newer developments.
Call to action
- Immediately isolate any systems running the Orion platform versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020.
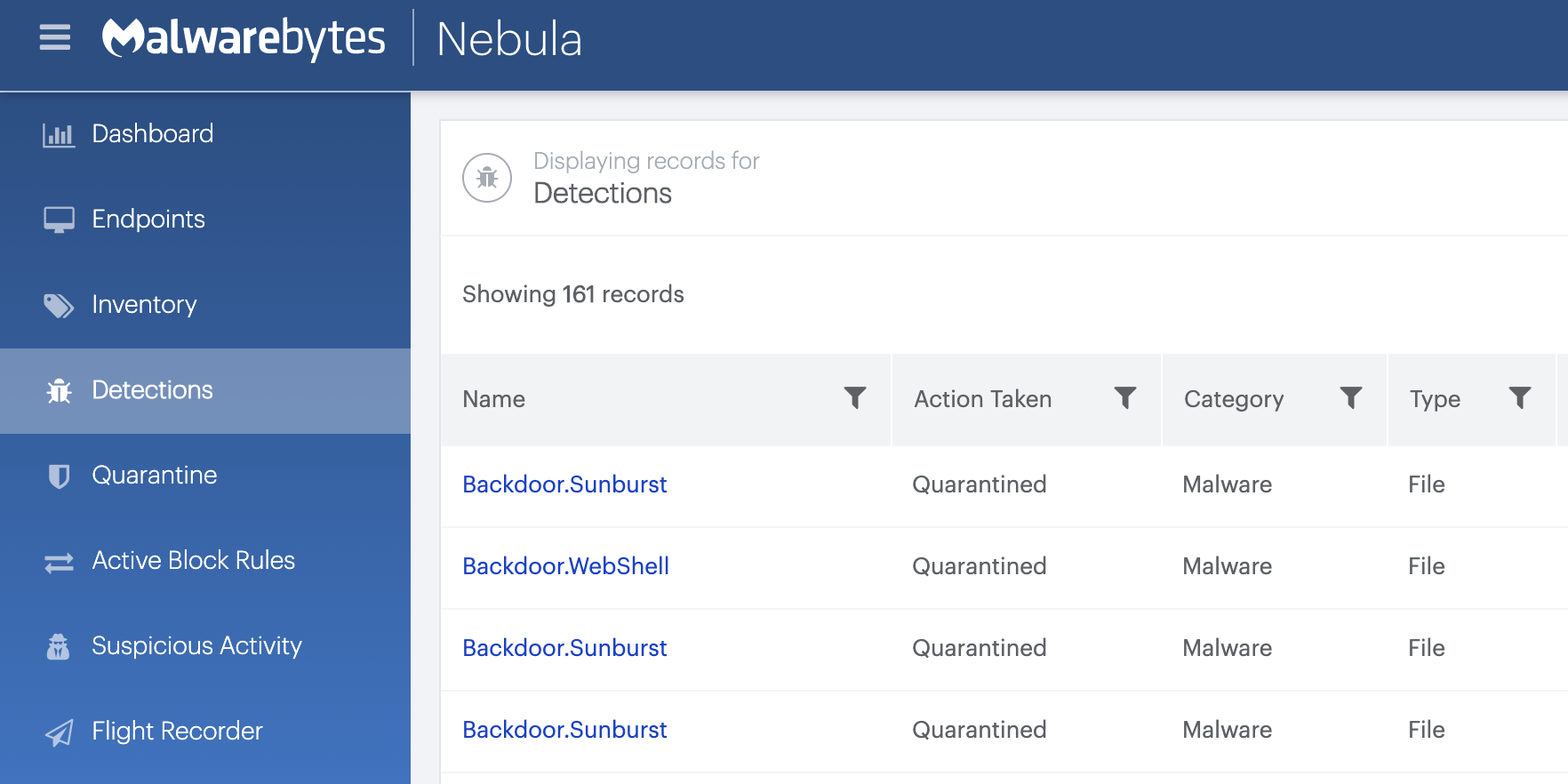
- Scan your premises using Malwarebytes and look for any detection, and in particular Backdoor.Sunburst and Backdoor.WebShell.
- Use the Indicators of Compromise at the end of this blog to hunt within your logs, telemetry and other SIEM data to give a timeline perspective to any potential intrusion.
- Perform a comprehensive security sweep to review and harden your physical and cloud infrastructure.
- Upgrade to Orion Platform version 2020.2.1 HF 1 and restore systems once you feel confident with the previous steps.

Further reading
- SolarWinds: SolarWinds Security Advisory
- FireEye: Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor
- Microsoft: Customer Guidance on Recent Nation-State Cyber Attacks
Indicators of Compromise (IOCs)
This list has been put together from several sources. Kudos to FireEye and Microsoft for sharing IOCs and TTPs so quickly.
SolarWinds.Orion.Core.BusinessLayer.dll
32519b85c0b422e4656de6e6c41878e95fd95026267daab4215ee59c107d6c77
dab758bf98d9b36fa057a66cd0284737abf89857b73ca89280267ee7caf62f3b
eb6fab5a2964c5817fb239a7a5079cabca0a00464fb3e07155f28b0a57a2c0ed
c09040d35630d75dfef0f804f320f8b3d16a481071076918e9b236a321c1ea77
ac1b2b89e60707a20e9eb1ca480bc3410ead40643b386d624c5d21b47c02917c
019085a76ba7126fff22770d71bd901c325fc68ac55aa743327984e89f4b0134
ce77d116a074dab7a22a0fd4f2c1ab475f16eec42e1ded3c0b0aa8211fe858d6
a25cadd48d70f6ea0c4a241d99c5241269e6faccb4054e62d16784640f8e53bc
d3c6785e18fba3749fb785bc313cf8346182f532c59172b69adfb31b96a5d0af
CORE-2019.4.5220.20574-SolarWinds-Core-v2019.4.5220-Hotfix5.msp
d0d626deb3f9484e649294a8dfa814c5568f846d5aa02d4cdad5d041a29d5600
appweblogoimagehandler.ashx.b6031896.dll
c15abaf51e78ca56c0376522d699c978217bf041a3bd3c71d09193efa5717c71
Network indicators
avsvmcloud[.]com
deftsecurity[.]com
freescanonline[.]com
thedoccloud[.]com
websitetheme[.]com
highdatabase[.]com
incomeupdate[.]com
databasegalore[.]com
panhardware[.]com
zupertech[.]com
13.59.205[.]66
54.193.127[.]66
54.215.192[.]52
34.203.203[.]23
139.99.115[.]204
5.252.177[.]25
5.252.177[.]21
204.188.205[.]176
51.89.125[.]18
167.114.213[.]199
Additional hunting rules: https://github.com/fireeye/sunburst_countermeasures/tree/main/rules
The post SolarWinds advanced cyberattack: What happened and what to do now appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: Zimmerman & Frachtman PA Law Firm 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

