Adblocker promises to blocks ads, injects them instead
Researchers at Imperva uncovered a new ad injection campaign based on an adblocker named AllBlock. The AllBlock extension was available at the time of writing for Chrome and Opera in the respective web stores.
While disguising your adware as an adblocker may seem counterintuitive, it is actually a smart thing to do. But let’s have a look at what they did and how, first.
AllBlock
As we mentioned, AllBlock is advertised as an adblocker on its site. It promises to block advertisements on YouTube and Facebook, among others.
When you’re installing the Chrome extension, the permissions it asks for make sense for an adblocker.
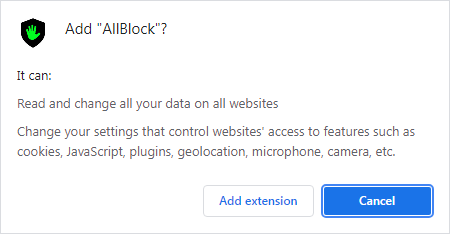
Even though that may seem like a lot to allow, and it is almost a carte blanche, any adblocker that you expect to work effectively will need a full set of permissions to at least “read and change all your data on all websites.”
What Imperva found is that the extension replaces all the URLs on the site a user is visiting with URLs that lead to an affiliate. This ad injection technique means that when the user clicks on any of the modified links on the webpage, they will be redirected to an affiliate link. Via this affiliate fraud, the attacker earns money when specific actions like registration or sale of the product take place.
Ad injection
Ad injection is the name for a set of techniques by which ads are inserted in webpages without getting the permission of site owners or paying them. Some of the most commonly seen tactics are:
- Replacing existing ads with ads provided by the attacker
- Adding ads to sites that normally have none
- Adding or changing affiliate codes so the attacker gets paid instead of the affiliate that had permission to advertise on a site
To pull this off, malicious browser extensions, malware, and stored cross-site scripting (XSS) are the most commonly found techniques.
In this case it was a malicious extension that used some interesting methods.
To make the extension look legitimate, the developers actually implemented ad blocking functionality. Further, the code was not obfuscated and nothing immediately screams malware.
All the URLs that are present in a visited website are sent to a remote server. This server replies with a set of URLs to replace them with. The reading and replacing of the URLs is done by the extension which was given permissions to do so.
To avoid detection, the threat actor has taken a few more measures besides looking harmless. The malicious javascript file detects debugging, it clears the debug console every 100 ms, and major search engines (with a special focus on Russian engines) are excluded.
A part of the code in the bg.js script that is part of the extension makes an HTTP request to allblock.net/api/stat/?id=nfofcmcpljmjdningbllljenopcmdhjf and receives a JSON response with two base64 encoded properties “data” and “urls”. The “data” part is the code that gets injected on every site the affected browser opens, and the “urls” part looks like this:
{"youtubeInput":["*://*.youtube.com/get_video_info*adunit*","*://*.g.doubleclick.net/pagead*","*://*.youtube.com/pagead*","*://*.googlesyndication.com/pagead*","*://*.google.com/pagead*","*://*.youtube.com/youtube*ad_break*"],"vkInput":["https://vk.com/al_video.php?act=ad_event*","https://vk.com/al_video.php?act=ads_stat*","https://vk.com/ads_rotate*","https://ad.mail.ru/*","https://ads.adfox.ru/*"]}Conclusion
The extension the Imperva team found actually blocks ads, but it also runs a background script that injects a snippet of JavaScript code into every new tab that a user opens in the affected browser. The end goal is to make money by replacing legitimate URLs on the website with URLs of their own. These URLs include affiliate codes, so they get paid if you click on one of those links and benefit from any sales that may come out of these clicks.
Ad blockers that are able to block advertisements on popular social media like YouTube and Facebook may seem like the holy grail to some users. To those that are interested in ad blocking and haven’t found the right program yet, please read “How to block ads like a pro.”
And as we have mentioned before, it makes sense to give ad blockers the permissions that they need to do their job. So we feel the need to emphasize that you should only give those permission to extensions that you actually trust, not just because you think “it” needs them.
Ad blocker campaigns
The Imperva team writes on their blog that they believe that there is a larger campaign taking place that may utilize different delivery methods and more extensions.
In our own Malwarebytes’ research we have found a series of adblockers that were pushed out through websites showing fake alerts like this one.
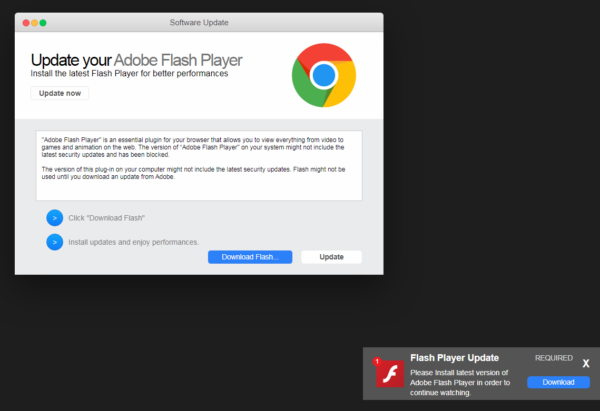
We could not find anything wrong with these extensions, and we also found that they were all using the publicly available Adguard blocklist. So we didn’t really follow up on them because, same as the one described above, they looked legitimate. The only thing that really made them look suspicious was that they were promoted through these “fake alert” sites.
For now it is hard to tell whether we have been tracking the same or similar campaigns. Since I haven’t seen the bg.js script before they may be completely different, but I will try and contact the Imperva team and compare notes. If anything interesting comes out of that, we will let you know.
Stay safe, everyone!
The post Adblocker promises to blocks ads, injects them instead appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![Brute Ratel C4 Detected - 18[.]177[.]187[.]233:80 7 brute_ratel_c4](https://www.redpacketsecurity.com/wp-content/uploads/2022/07/brute_ratel_c4-300x300.jpg)
![Cobalt Strike Beacon Detected - 118[.]89[.]73[.]78:4433 8 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)