Anatsa Banking Trojan Targeting Users in US, UK, Germany, Austria, and Switzerland
A new Android malware campaign has been observed pushing the Anatsa banking trojan to target banking customers in the U.S., U.K., Germany, Austria, and Switzerland since the start of March 2023.
“The actors behind Anatsa aim to steal credentials used to authorize customers in mobile banking applications and perform Device-Takeover Fraud (DTO) to initiate fraudulent transactions,” ThreatFabric said in an analysis published Monday.
The Dutch cybersecurity company said Anatsa-infected Google Play Store dropper apps have accrued over 30,000 installations to date, indicating that the official app storefront has become an effective distribution vector for the malware.
Anatsa, also known by the name TeaBot and Toddler, first emerged in early 2021, and has been observed masquerading as seemingly innocuous utility apps like PDF readers, QR code scanners, and two-factor authentication (2FA) apps on Google Play to siphon users’ credentials. It has since become one of the most prolific banking malware, targeting over 400 financial institutions across the world.
The trojan features backdoor-like capabilities to steal data and also performs overlay attacks in order to steal credentials as well as log activities by abusing its permissions to Android’s accessibility services API. It can further bypass existing fraud control mechanisms to carry out unauthorized fund transfers.
“Since transactions are initiated from the same device that targeted bank customers regularly use, it has been reported that it is very challenging for banking anti-fraud systems to detect it,” ThreatFabric noted.
In the latest campaign observed by ThreatFabric, the dropper app, once installed, makes a request to a GitHub page that points to another GitHub URL hosting the malicious payload, which aims to trick victims by disguising themselves as app add-ons. It’s suspected that users are routed to these apps through sketchy advertisements.
A notable aspect of the dropper is its use of the restricted “REQUEST_INSTALL_PACKAGES” permission, which has been repeatedly exploited by rogue apps distributed via the Google Play Store to install additional malware on the infected device. The names of the apps are as follows –
- All Document Reader & Editor (com.mikijaki.documents.pdfreader.xlsx.csv.ppt.docs)
- All Document Reader and Viewer (com.muchlensoka.pdfcreator)
- PDF Reader – Edit & View PDF (lsstudio.pdfreader.powerfultool.allinonepdf.goodpdftools)
- PDF Reader & Editor (com.proderstarler.pdfsignature)
- PDF Reader & Editor (moh.filemanagerrespdf)
All the five dropper apps in question are said to have been updated after their initial publication, likely in a stealthy attempt to slip the malicious functionality after passing the app review process during the first submission.
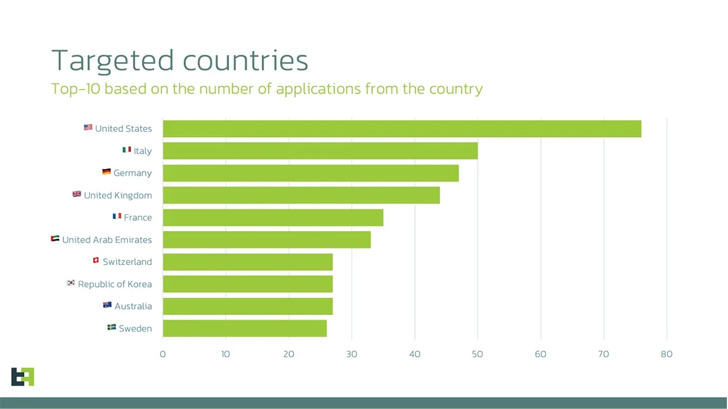
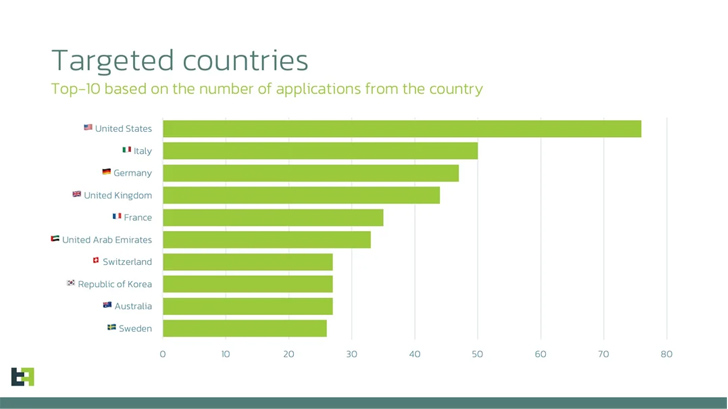
The list of top countries that are of interest to Anatsa based on the number of financial applications targeted include the U.S., Italy, Germany, the U.K., France, the U.A.E., Switzerland, South Korea, Australia, and Sweden. Also present in the list are Finland, Singapore, and Spain.
“The latest campaign by Anatsa reveals the evolving threat landscape that banks and financial institutions face in today’s digital world,” ThreatFabric said. “The recent Google Play Store distribution campaigns […] demonstrate the immense potential for mobile fraud and the need for proactive measures to counter such threats.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.