Another one bites the dust: Avaddon ransomware group shuts down operation
Are you seeing some pattern here?
In what could be a called “shocking news” on Friday, BleepingComputer revealed that the gang behind the Avaddon ransomware shut down its operations after releasing more than 2,000 decryption keys to the technology news site.
BleepingComputer claimed they received an anonymous tip purporting to be from the FBI, containing a password and a link to a password-protected ZIP file.
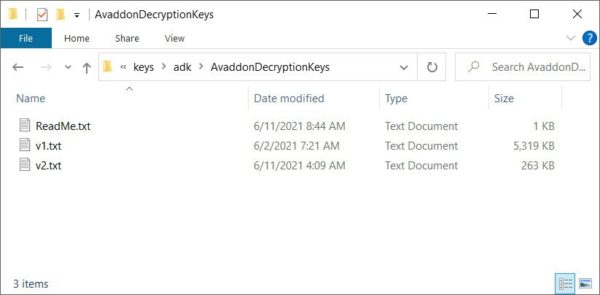
If you may recall, Avaddon is a big game hunting (BGH), ransomware-as-a-service (RaaS) tool that the US Federal Bureau of Investigation (FBI) and the Australian Cyber Security Centre (ACSC) warned organizations about last month.
Malwarebytes detects this ransomware as Ransom.Avaddon.
Avaddon ransomware attack victims
While various sectors in Australia were noted to be particularly targeted, the Avaddon strain has been instrumental in the successful network compromise of the Asian division of the AXA Group, one of the biggest cyber insurance companies in the world. Avaddon threat actors were able to extract information about what appears to be client info: passports, bank account information, ID cards, contracts, fraud-related hospital files, and other medical reports containing sensitive data about patients, and more.
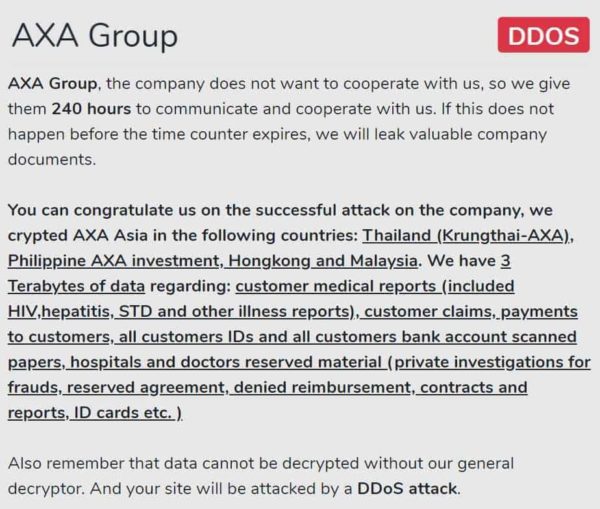
Coincidentally, this attack came close to a week after the insurance giant announced that it would cease covering customers in France who pay up after being attacked by ransomware. An insurance company refusing to cover for any monetary loss over a cyberattack will no doubt significantly increase the likelihood of victim companies refusing to cough up money to ransomware gangs.
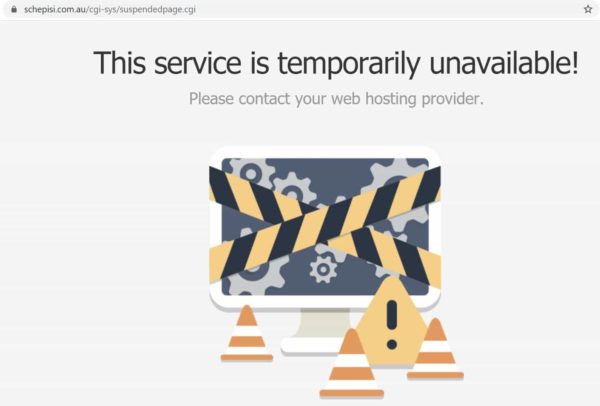
Schepisi Communication, an Australia-based telecom service provider, was also hit by Avaddon last month after its platinum partner, Telstra, fell victim to a ransomware attack by the same group. The criminals claimed to have access to data of a large amount of SIM cards, mobile devices, contracts, and banking information to name a few. When the company refused to pay the demand, their official website was downed by distributed denial of service (DDoS) attacks, taking their website offline for several days.
Avaddon threat actors are also not one to shy away from going after organizations in the healthcare industry. According a threat report from eSentire, a leading Managed Detection and Response (MDR) service provider, Avaddon has targeted the Capital Medical Center in Washington, Bridgeway Senior Healthcare in New Jersey, and an intensive care online network.
A domino effect? Or a simple coincidence?
After DarkSide called it quits from the pressures of the US government following their attack against Colonial Pipeline, reading about Avaddon—considered to be a “second tier ransomware operator”—would make one think that there is cause for celebration. Indeed, this is a win and something we should be grateful for.
Let us not forget, however, that any time a ransomware gang decides to shut down, more gangs appear (If you’re on Twitter and follow several malware/ransomware hunters, you’ll agree).
It is also a known fact that ransomware actors have the habit of rebranding under the guise of shutting down—or to simply avoid US sanctions—so it won’t be far off to think that this is all a ruse. And speaking of sanctions, as of this writing, there is nothing that links Avaddon’s demise to the increased attention the US government has given ransomware groups lately. It’s likely then that this is all just part of the normal flow of events when groups give up from time to time. That said, this could be one of those wait-and-see scenarios.
Nonetheless, we welcome any ransomware gang quitting as good news. But perhaps, at the same time, we’re also left wondering: Is there a quiet chaos going on right now within and among the underground ransomware gangs? Will they start dropping like flies? Will we be left with our old, insecure ways if or when ransomware attacks do plummet?
Well, let’s wait and see.
The post Another one bites the dust: Avaddon ransomware group shuts down operation appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


