Ashok – A OSINT Recon Tool, A.K.A Swiss Army Knife
Reconnaissance is the first phase of penetration testing which means gathering information before any real attacks are planned So Ashok is an Incredible fast recon tool for penetration tester which is specially designed for Reconnaissance” title=”Reconnaissance”>Reconnaissance phase. And in Ashok-v1.1 you can find the advanced google dorker and wayback crawling machine.

Main Features
- Wayback Crawler Machine
- Google Dorking without limits
- Github Information Grabbing
- Subdomain Identifier
- Cms/Technology Detector With Custom Headers
Installation
~> git clone https://github.com/ankitdobhal/Ashok
~> cd Ashok
~> python3.7 -m pip3 install -r requirements.txt
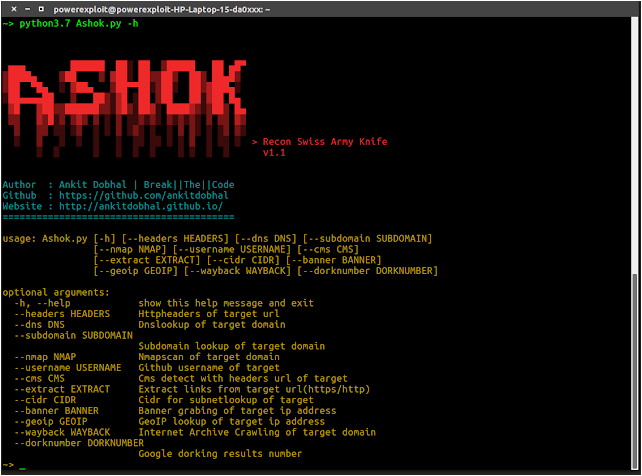
How to use Ashok?
A detailed usage guide is available on Usage section of the Wiki.
But Some index of options is given below:
- Extract Http Headers from single url
- Dump internet-archive machine with json output for single url
- Google dorking using number of results as dorknumber
- Dns Lookup of single target domain
- Subdomain Lookup of single target domain
- Port Scan using nmap of single target domain
- Extract data using Github username of target
- Detect Cms of target url
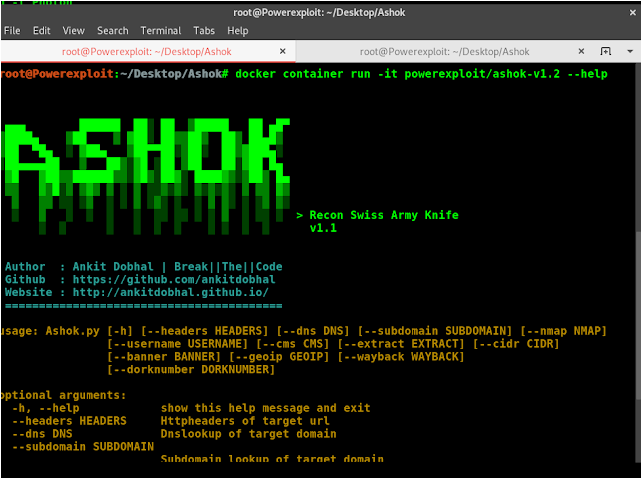
Docker
Ashok can be launched using a lightweight Python3.8-Alpine Docker image.
$ docker pull powerexploit/ashok-v1.2
$ docker container run -it powerexploit/ashok-v1.2 --help
Credits
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![[Palo Alto Networks Security Advisories] PAN-SA-2025-0016 Chromium: Monthly Vulnerability Update (October 2025) 5 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

