Avaddon ransomware campaign prompts warnings from FBI, ACSC
Both the Australian Cyber Security Centre (ACSC) and the US Federal Bureau of Investigation (FBI) have issued warnings about an ongoing cybercrime campaign that is using Avaddon ransomware.
The FBI states that is has received notifications of unidentified cyber actors using Avaddon ransomware against US and foreign private sector companies, manufacturing organizations, and healthcare agencies.
In a separate advisory (pdf), the ACSC says it is also aware of an ongoing ransomware campaign using the Avaddon Ransomware malware. This campaign is actively targeting Australian organizations in a variety of sectors.
Avaddon ransomware
Ransom.Avaddon is sold to criminal affiliates as a Ransomware-as-a-Service (RaaS) strain. It has been around since 2019 and in June of 2020 it got some real traction due to a malspam campaign. Later it started promoting higher rates for its affiliates using adverts on networks and RDP. Avaddon ransomware performs an encryption in offline mode using AES-256 + RSA-2048 to encrypt files. When encrypted the files get the .avdn extension.
No current decryptor
In you’ve heard about an Avaddon decryptor, don’t get your hopes up. It’s true that in February 2021 a researcher found a flaw in the Avaddon encryption routine that allowed them to create a free decryptor. However, one day later the ransomware developer posted a message that the flaw was fixed. So, the decryptor only works for older infections. If you have been affected by Avaddon since then, it will not work.
FBI description of Avaddon
Avaddon is used in targeted, “big game” ransomware attacks using familiar tactics. According to the FBI, Avaddon ransomware actors have compromised victims through remote access login credentials—such as Remote Desktop Protocol (RDP) and Virtual Private Networks (VPN). After Avaddon actors gain access to a victim’s network, they map the network and identify backups for deletion and/or encryption. The malware escalates privileges, contains anti-analysis protection code, enables persistence on a victim system, and verifies the victim is not located in the Commonwealth of Independent States (CIS). Finally, a copy of the victim’s data is exfiltrated before the victim’s systems are encrypted.
Not afraid of law enforcement
Like many other ransomware operators hailing from the CIS they act as if they have nothing to fear from law enforcement. And as long as they do not attack organizations in their home country that is unfortunately probably true. Some Russian gangs have even been getting aggressive against law enforcement in the US. Statistics of how many police departments have been hit by ransomware attacks are hard to come by, as is information on whether departments ever pay a ransom. Homeland Security Secretary Alejandro Mayorkas has called ransomware a threat to national security and said the issue is a top priority of the White House. That sentiment was echoed in a recent report by the Ransomware Task Force.
Ransomware as a Service (RaaS)
Avaddon is offered as a Ransomware-as-a-Service (RaaS), a system that sees affiliates do the dirty work and use the ransomware however they like, provided they return a percentage of their profits to the Avaddon developers. The ACSC notes that Avaddon also has an active presence on underground dark web cybercrime forums, where it advertises the malware to potential affiliates. Avaddon threat actors also use a data leak site to identify victims who fail or refuse to pay ransom demands.
Typically, with RaaS you will see affiliates run different distribution vectors and look over each other’s shoulder to see what is working best. Probably because of this model we have seen Ransom.Avaddon spread by a botnet, in malspam campaigns, by exploit kits (RIG-EK), and recently by brute forcing RDP and VPN credentials.
Additional threats
Like many other ransomware operators Avaddon has also increased pressure on its victims by threatening to publicize exfiltrated data on the dark web, and by performing DDoS attacks. The extortion/data leak process typically follows these steps:
- Leak warning: After initially gaining access to a victim network, Avaddon actors leave a ransom note on the victim’s network and post a “leak warning” to the Avaddon dark web leak website. The warning consists of screenshots from files and proof of access to the victim’s network.
- 5 percent leak: If the victim does not quickly pay the ransom within 3 to 5 days, Avaddon actors increase the pressure on victims by leaking a portion of the stolen files. The Avaddon actors leak this data by uploading a small .zip file to Avaddon’s dark web leak website.
- Full leak: If the ransom is not paid after the 5 percent leak, Avaddon actors post all their exfiltrated data in large .zip files in the “Full dumps” section of the Avaddon dark web leak website.
Detection and protection
Malwarebytes detects Ransom.Avaddon and protects user by means of real-time protection, both by using detection rules as well as patented anti-ransomware technology.
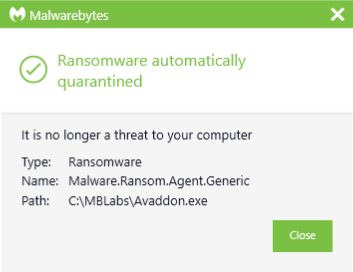
Stay safe, everyone!
The post Avaddon ransomware campaign prompts warnings from FBI, ACSC appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[INCRANSOM] - Ransomware Victim: State Bar of Texas (www[.]texasbar[.]com) 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)