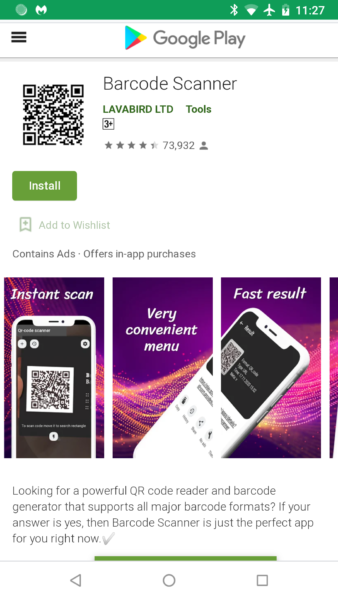
Barcode Scanner app on Google Play infects 10 million users with one update
Late last December we started getting a distress call from our forum patrons. Patrons were experiencing ads that were opening via their default browser out of nowhere. The odd part is none of them had recently installed any apps, and the apps they had installed came from the Google Play store. Then one patron, who goes by username Anon00, discovered that it was coming from a long-time installed app, Barcode Scanner. An app that has 10,000,000+ installs from Google Play! We quickly added the detection, and Google quickly removed the app from its store.
Simple scanner turns evil
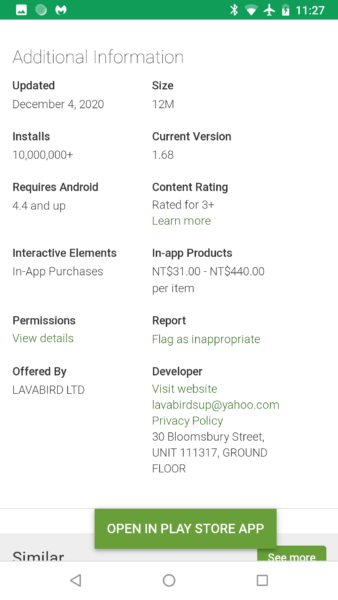
Many of the patrons had the app installed on their mobile devices for long periods of time (one user had it installed for several years). Then all of sudden, after an update in December, Barcode Scanner had gone from an innocent scanner to full on malware! Although Google has already pulled this app, we predict from a cached Google Play webpage that the update occurred on December 4th, 2020.
Malicious intent
The majority of free apps on Google Play include some kind of in-app advertizing. They do this by including an ad SDK to the code of the app. Usually at the end of the app’s development. Paid-for versions simply do not have this SDK included.
Ad SDKs can come from various third-party companies and provide a source of revenue for the app developer. It’s a win-win situation for everyone. Users get a free app, while the app developers and the ad SDK developers get paid.
But every once in a while, an ad SDK company can change something on their end and ads can start getting a bit aggressive. Sometimes even landing the apps that use it in the Adware category. When this happens, it is not the app developers’ doing, but the SDK company. I explain this method to say that in the case of Barcode Scanner, this was not the case.
No, in the case of Barcode Scanner, malicious code had been added that was not in previous versions of the app. Furthermore, the added code used heavy obfuscation to avoid detection. To verify this is from the same app developer, we confirmed it had been signed by the same digital certificate as previous clean versions. Because of its malign intent, we jumped past our original detection category of Adware straight to Trojan, with the detection of Android/Trojan.HiddenAds.AdQR.
Bad behavior
The toughest part of malware analysis can be replicating what our users are experiencing. That wasn’t a problem with Barcode Scanner, it went into action within minutes of install. Watch the short video below to see its malicious behavior:
Removed from Play, but not from mobile device
Removing an app from the Google Play store does not necessarily mean it will be removed from affected mobile devices. Unless Google Play Protect removes it after the fact, it remains on the device. This is exactly what users are experiencing with Barcode Scanner. Thus, until they install a malware scanner like Malwarebytes for Android, or manually remove the app, it will continue to display ads.
Lying dormant
It is hard to tell just how long Barcode Scanner had been in the Google Play store as a legitimate app before it became malicious. Based on the high number of installs and user feedback, we suspect it had been there for years. It is frightening that with one update an app can turn malicious while going under the radar of Google Play Protect. It is baffling to me that an app developer with a popular app would turn it into malware. Was this the scheme all along, to have an app lie dormant, waiting to strike after it reaches popularity? I guess we will never know.
App Information
App Name: Barcode Scanner
MD5: A922F91BAF324FA07B3C40846EBBFE30
Package Name: com.qrcodescanner.barcodescanner
The post Barcode Scanner app on Google Play infects 10 million users with one update appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.