Beware password-spraying fancy bears
The NSA, FBI, and CISA, in cooperation with the UK’s National Cyber Security Centre (NCSC), have issued a report that describes in detail why, and how, they think that a Russian military unit is behind large-scale brute-force attacks on the cloud-IT resources of government and private sector companies around the world. The report states:
Since at least mid-2019 through early 2021, Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS), military unit 26165, used a Kubernetes® cluster to conduct widespread, distributed, and anonymized brute force access attempts against hundreds of government and private sector targets worldwide.
The agencies are pointing their collective fingers at military unit 26165 of the Russian General Staff Main Intelligence Directorate (commonly know as GRU), which you will find often referred to as Fancy Bear, APT28, Strontium, and some other names.
The targets
Most of the named activity is aimed at organizations using Microsoft Office 365 cloud services, but the attacks are certainly not limited to those. They also targeted other service providers and on-premises email servers using a variety of different protocols. I use the present tense on purpose as these attacks are almost certainly still ongoing.
The campaign is said to have targeted hundreds of US and foreign organizations, including US government and defense entities. While the sum of the targeting is global in nature, it has predominantly focused on entities in the US and Europe.
The method
The report includes a graphic that explains the most prevalent attack method.
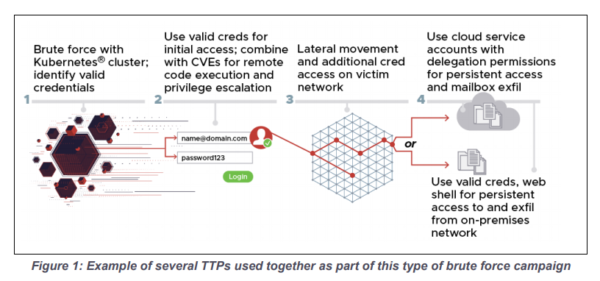
Some attacks used known vulnerabilities that allowed remote code execution (RCE), while others started by trying to identify valid credentials through password spraying. Password spraying involves using a limited list of credentials against a large number of accounts, a brute-force tactic that’s useful if you don’t really care which accounts you take over.
The attacks were launched from a Kubernetes cluster. A Kubernetes cluster is a “container orchestration” system for running a large number of containerized applications. The applications in the cluster used TOR and commercial VPN services to avoid revealing their IP addresses.
Once initial access had been secured, attackers used a variety of well-known tactics, techniques, and procedures (TTPs) to escalate privileges, establish persistence, move laterally, and collect additional information.
If any of the cloud service credentials the attackers discovered were sufficiently privileged, they were used to exfiltrate data. Where this was not an option, for example when mail was not handled in the cloud, the threat actor used a modified and obfuscated version of the reGeorg web shell to maintain persistent access on a target’s Outlook Web Access server. The reGeorg webshell creates a socks proxy for intranet penetration and as such can be used as a means to gain persistence.
Mitigation and detection
The report contains a number of mitigation methods but makes a special plea for multi-factor authentication (MFA).
Network managers should adopt and expand usage of multi-factor authentication to help counter the effectiveness of this capability. Additional mitigations to ensure strong access controls include time-out and lock-out features…
MFA stops password spraying and other forms of brute-force attacks in their tracks. It doesn’t matter how long your password list is, or how many password attempts you make—if you don’t have a user’s second authentication factor, such as a numeric code or fingerprint, you cannot get access. Time-out and lock-out features are useful for strengthening weak passwords by reducing the number of guesses an attacker can make.
The report also mentions the mandatory use of strong passwords as a useful mitigation. It is, but if that were easy, the other mitigations wouldn’t be necessary. Aim for strong passwords, but plan for bad ones.
Other mitigation methods mentioned in the report include:
- Implementing a Zero-Trust security model.
- Captcha, when human interaction is required.
- Analytics for detecting anomalous authentication activity.
For detection purposes the report lists a few incomplete or truncated versions of legitimate User-Agent strings that the attackers used:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:63.0) Gecko/20100101 Firefox/63.0
Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_1) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.1 Safari/605.1.15
Microsoft Office/14.0 (Windows NT 6.1; Microsoft Outlook 14.0.7162; Pro
Microsoft Office/14.0 (Windows NT 6.1; Microsoft Outlook 14.0.7166; Pro)
Microsoft Office/14.0 (Windows NT 6.1; Microsoft Outlook 14.0.7143; Pro)
Microsoft Office/15.0 (Windows NT 6.1; Microsoft Outlook 15.0.4605; Pro)The report also provides a Yara rule matches the reGeorg variant web shell used by the actors.
rule reGeorg_Variant_Web shell
{
strings:
$pageLanguage = "<%@ Page Language="C#""
$obfuscationFunction = "StrTr"
$target = "target_str"
$IPcomms = "System.Net.IPEndPoint"
$addHeader = "Response.AddHeader"
$socket = "Socket"
condition:
5 of them
}
The report warns that the rule does not uniquely GRU activity since the web shell is publicly available.
The post Beware password-spraying fancy bears appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[LYNX] - Ransomware Victim: ozsoft[.]com[.]au 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
