Blunting RDP brute-force attacks with rate limiting
Thanks to the Malwarebytes Threat Intelligence Team for the information they provided for this article.
Not long ago, guessing a Windows Remote Desktop Protocol (RDP) password successfully was widely regarded as ransomware operators’ number one choice for breaching a target. It attracted a lot of press coverage three or four years ago, and interest in it was renewed in 2020 by the sudden addition of a million or so RDP-connected computers to the Internet, with the onset of the pandemic and wide-scale working from home.
Things have been a little quiet since, and in 2021 RDP was eclipsed—in the press at least—by ransomware gangs’ use of a whole host of different and diverting vulnerabilities, such as the ProxyLogon attack chain.
You’d be forgiven for thinking that RDP abuse was a thing of the past. It is not.
The Ransomware Delivery Protocol
RDP is a fantastically powerful feature of Windows that makes remote work and remote administration feel like it isn’t remote at all. If a Windows computer has an Internet connection, and RDP switched on, it can be used from anywhere by anyone with a valid username and password, with all the same features and access rights as if they were sat right in front of it.
RDP is so useful that millions of Internet-connected Windows computers have it enabled.
We know this because it is trivially easy to find them, and that’s a problem.
To see why, imagine that you work in an office building that doesn’t close its doors at night and instead lets criminals wander around, trying their luck at logging on to its computers. The criminals are in no hurry, they can come back night after night, so they have plenty of time to find a computer with a weak password, or to plug away at one computer trying more and more complex passwords.
The Internet is like that overly-permissive office—and thanks to RDP it has over four million computers exposed to every cybercrook in the world, and their password guessing software.
RDP password guessing has been an enormously important technique for ransomware gangs in the last few years, because it allows them to breach a victims’ network disguised as a legitimate employee. It has been so successful that it has spawned criminals who specialise in guessing RDP passwords, and markets where they can sell them to ransomware operators.
RDP brute-forcing is alive and well
The Malwarebytes Threat Intelligence team maintains RDP honeypots that track the effectiveness of Malwarebytes Brute Force Protection (BFP), a countermeasure against RDP password guessing. The honeypots provide a revealing insight into the enormous amount of RDP brute-forcing attacks happening in the background, all day, every day.
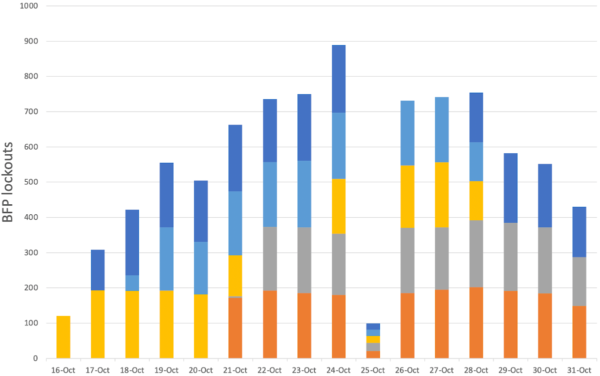
We took a slice of data from an unremarkable period of last year—the last 15 days of October 2021—to illustrate the scale of the problem.
The honeypot in our test was an Internet-connected Windows computer with RDP enabled on the non-standard port. It used out-of-the-box BFP rate-limits: Attackers were shut out for five minutes if they entered five incorrect passwords within the space of five minutes.
There is nothing about our honeypots that makes them tempting targets. If you have RDP-enabled computers, you can assume that each and every one is attracting a similar level of attention from password guessing attacks.
10,000 attacks a day
In the last 15 days of October, a five-minute BFP lockout was triggered 28,910 times, by attacks from 29 separate IP addresses. Because it takes five attempts to trigger a lockout, the total number of password attempts made against the honeypot during that test period was therefore 144,550, or about 10,000 per day. This figure is likey to be dampened considerably by the rate limiting—without it, the numbers would likely have been much higher.
The five IP addresses that probed the honeypot most frequently during that time all presisted for about ten days, in overlapping shifts. This similarity in the number of daily guesses they made, and the time they spent making guesses, may indicate that they come from the same attacker using multiple IP addresses.
Using a non-standard port is no protection
RDP normally uses port 3389. Since it is easy to scan the Internet for computers listening on port 3389 it is fairly common for RDP hardening advice to recommend assigning it a different port number.
The honeypots in this test do that: They are connected using a port from the dynamic port range, which is unlikely to be any hacker’s first guess. Despite that, our honeypots’ RDP ports receive heavy and continuous attention from brute-force password guessing programs.
It is our assessment that changing the port number does not provide any meaningful protection. It’s a cheap and easy change to make, and there is no harm in it, but you should look elsewhere for genuine hardening.
The effects of rate limiting
Rate limiting works by throttling the speed at which attackers can make password guesses, typically by shutting them out for a period of time after a small number of incorrect guesses. This is mildly inconvenient to a real user who is unlikely to make more than a handful of incorrect guesses before calling support, but represents a huge barrier for a computer program looking to race through tens or even hundreds of thousands of password attempts.
Rate limiting is what allows enormously important things like credit cards and smartphones to be secured with four- or six-digit PINs that are otherwise trivival to crack.
So how many guesses does rate limiting prevent?
In our test, attackers were shut out for five minutes if they entered five incorrect passwords within the space of five minutes. Our attackers were persistent over several days and received, on average, about 150 bans per day.
To trigger 150 bans per day, our attackers must have made 750 incorrect guesses and incurred 750 minutes of bans, leaving them 690 minutes of the day in which to guess passwords. 750 guesses in 690 minutes gives us a guessing rate of about one password every 55 seconds, or about 1,500 guesses per day.
At that guessing rate, rate limiting reduced the number of daily password attempts from 1500 to 750, halving the effectiveness of the attack and doubling the time a security team would have to react.
But 1,500 guesses per day is an extremely low guessing rate and a very poor use of an attackers’ resources. Other attackers are much more aggressive in their approach.
A few years ago I co-authored a research paper on RDP brute forcing. During our research we monitored an attacker who made 109,934 password guesses in ten days, at a rate of about 11,000 guesses per day, or about 7.5 guesses per minute.
Against that attacker, the rate limiting we used for this article would have been triggered every 40 seconds, allowing them just 1,270 guesses per day—reducing the guessing rate by 87%, giving a security team an additional two and a half months to respond to the attack.
Rate limiting is a powerful technique for limiting the effectiveness of brute-force attacks. However, in all areas of security we recommend a defense-in-depth approach over a reliance on any one tool or technique. For more information on how to protect your RDP connections read our article on how to protect your RDP access from ransomware attacks.
The post Blunting RDP brute-force attacks with rate limiting appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Cobalt Strike Beacon Detected - 166[.]108[.]234[.]74:8089 3 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)