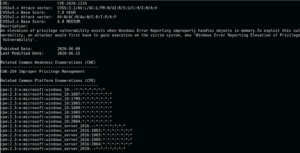
cve_manager_VS – A Collection Of Python Apps And Shell Scripts To Email An Xlsx Spreadsheet Of New Vulnerabilities In The NIST CVE Database And Their Associated Products On A Daily Schedule
A collection of python apps and shell scripts to email an xlsx spreadsheet of new vulnerabilities in the NIST CVE...