3 Challenges in Building a Continuous Threat Exposure Management (CTEM) Program and How to Beat Them
If you’re a cybersecurity professional, you’re likely familiar with the sea of acronyms our industry is obsessed with. From CNAPP, to CWPP, to CIEM and all of the myriad others, there seems to be a new initialism born each day.
In this article, we’ll look at another trending acronym – CTEM, which stands for Continuous Threat Exposure Management – and the often-surprising challenges that come along with seeing a CTEM program through to maturity. While the concept of CTEM isn’t brand spanking new, having made its in-print debut in July of 2022, we are now at the point where many organizations are starting to try to operationalize the programs that they’ve been setting into motion over the last few months. And as organizations start to execute their carefully designed plans, they may find themselves bumping up against some unexpected challenges which can lead to setbacks.
What is Continuous Threat Exposure Management (CTEM)?#
But first, to backtrack, let’s just quickly review what CTEM is and isn’t.
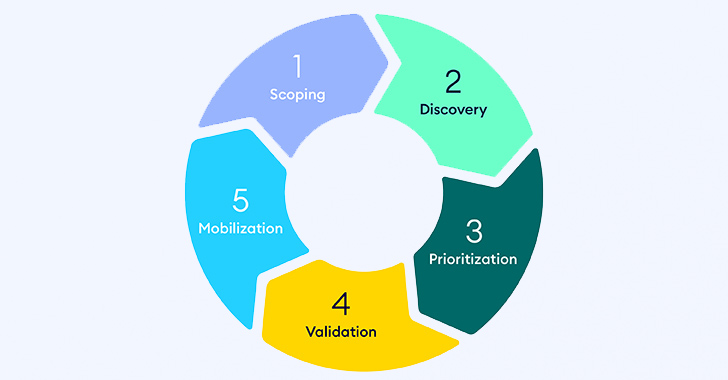
Continuous Threat Exposure Management is not a technology and you can’t go to a vendor in hopes of finding a CTEM solution (or, at least not with just one single tool). What CTEM is, instead, is a continuous 5-stage program or framework intended to help organizations monitor, evaluate, and reduce their level of exploitability and validate that their analysis and remediation processes are optimal. According to a Gartner® report, “The objective of CTEM is to get a consistent, actionable security posture remediation and improvement plan that business executives can understand and architecture teams can act upon.” (Gartner, 21 July 2022, Implement a Continuous Threat Exposure Management (CTEM) Program)

Download our new whitepaper, Establishing a Modern Exposure Management Program, and discover:
- Why critical vulnerability does not equal risk
- The different types of exposures impacting organizational security posture
- The key fundamentals of a modern exposure management program designed for an evolving risk landscape
- And more!
What are the Goals of CTEM?#
The Gartner report further states, “Technology-centric attack surfaces and vulnerability self-assessment projects generate rarely-actioned reports and long lists of generic remediations. Vulnerability management programs rarely keep up with the aggregate volume of their own organization, leading to quickly expanding attack surfaces”. (Gartner, 21 July 2022, Implement a Continuous Threat Exposure Management (CTEM) Program) These factors, coupled with some other key drivers, such as the difficulty in maintaining security posture over time amid an ever-mushrooming attack surface, mean that traditional methods for holistically ensuring security are growing less effective all the time.
According to Gartner, “The objective of CTEM is to get a consistent, actionable security posture remediation and improvement plan that business executives can understand and architecture teams can act upon.” (Gartner, 21 July 2022, Implement a Continuous Threat Exposure Management (CTEM) Program). When properly implemented, CTEM can help organizations continually improve their security posture by identifying and remediating potentially problematic areas before they can be leveraged by attackers.
3 Challenges on the Road to Meeting CTEM#
Fabulous. So what are you waiting for?
Hold up; setting up a CTEM program is a great initiative – but there are some challenges in implementation that need to be addressed in order for execution to be successful. Accounting for them earlier on in the implementation stages could save time and frustration down the road.
Challenge 1 – Getting non-security and security on the same page#
It’s a well-known fact that IT/infrastructure/DevOps/application, etc. teams and security teams don’t always speak the same language; this is problematic in numerous ways but when implementing new programs or undertakings, this disconnect can become even more problematic. In implementing CTEM, this can translate into a lack of understanding of who from the non-security team owns what, and not being aligned on SLA expectations, among other issues.
The problem here is that fully communicating the need is hard, especially when teams are bogged down with loads of “URGENT!” projects – and, to them, CTEM is just another one of those projects. This lack of understanding can disincentivize them from actually doing what needs to be done.
How to fix – From the very earliest stages, bring stakeholders from non-security teams into the conversation. It’s not good enough just to provide them with a to-do list. Instead, sit with them and explain the goals you’re trying to achieve so that they have a proper understanding of what is being done. Ask for their input and find out what they’ll need from you or other teams in the organization to make their lives easier. Additionally, sharing cyber attack news with them will make them more aware of the business impact that they could have, and how it actually ties back into their part of the business.
Challenge 2 – Seeing the bird’s eye view#
A comprehensive CTEM program covers many different areas, from Cloud, to AD, to software vulnerabilities, to network security and basically everything else. Each one of these exists in its own silo and has its own owners, their own tooling and their own list of issues to fix. The goal of CTEM is to unite all of them into one holistic view with all areas informing the others. In practicality, that means aggregating all information and using it to understand priorities and responsibilities.
But getting a baseline of understanding is challenging as each of these areas requires different expertise. The last thing you’d want is to have a program that has been painstakingly built and executed but fails to understand the risks that each area presents – or worse, forgets to include any particular area of issue.
How to fix – Define someone as the “point person” – the one person who can take the bird’s eye view and become a high-level master at understanding how all the covered areas converge and impact each other. This person doesn’t need to understand the tiniest bits and bites of how each tool works or what each category of security issue encompasses, but they should be able to grasp the entirety of the big picture so they can fully and accurately ensure that all areas are accounted for and are being continually addressed by professionals who do have deep and nuanced expertise.
Challenge 3 – Overcoming diagnostic overload #
Back to that point about all the different areas covered in CTEM; Another important aspect to note is that as they all have their own tools, they all yield alerts. And so while a primary objective of CTEM is to streamline all of the information stemming from these tools, one notable byproduct is just a whole lot of extraneous noise.
How to fix – Accept the fact that fixing everything is pretty much impossible, which means you need to prioritize and be as efficient as possible. To do this, focus on the scopes and exposures that could most likely be exploited by an attacker and which could lead to the greatest business impact. It may help to take the “crawl, walk, run” approach, i.e., start with baby steps which zero-in on a small scope and enlarge it as your program grows more mature. (Want to make meeting CTEM even easier? Get this checklist on practical tips to streamlining CTEM here.)
Conclusion #
According to Gartner, “By 2026, organizations prioritizing their security investments based on a continuous exposure management programme will be three times less likely to suffer from a breach.” (Gartner, 21 July 2022, Implement a Continuous Threat Exposure Management (CTEM) Program) And we feel that is huge. Hopefully, by ironing out some of the potential kinks along the way, your organization will be primed to meet CTEM seamlessly.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.