Credentials Are Still King Leaked Credentials Data Breaches And Dark Web Markets

Infostealer malware is one of the most substantial and underappreciated risk vectors for corporate information security teams. Infostealers infect computers, steal all of the credentials saved in the browser along with active session cookies and other data, then export it back to command and control (C2) infrastructure before, in some cases, self-terminating.
This article will explore the ways in which threat actors utilize credentials to break into privileged IT infrastructure to create data breaches and distribute ransomware.
Infostealers aren’t the only credential threat however. Leaked credentials from traditional sources are still a prominent and substantial risk to organizations.
It comes as no surprise that most users reuse passwords across dozens of applications, creating a perfect opportunity for threat actors to brute force their way into SaaS and on-premise applications.
At Flare we currently monitor more than forty million stealer logs, a number that is growing by millions every month and looks set to increase even more rapidly in 2024. In addition, we monitor more than 14 billion leaked credentials found from dumps across the dark web.
This gives us a unique perspective into how threat actors are acquiring, distributing, and using leaked credentials.
Types of Leaked Credentials
To better understand leaked credentials it is helpful to “tier” them into categories based on the method in which they are leaked, and the risk that they pose to the organization.
Jason Haddix pioneered this approach to enable security professionals to clearly communicate the risks associated with credential leaks in an easy and consumable way for managers and corporate executives.
Tier 1 Leaked Credentials
Tier 1 leaked credentials result from a third-party application/service breaches, and all of the users of that service having their passwords compromised and distributed in a data dump on the dark web. This is what most people think of when they talk about “leaked credentials.”
As an example, let’s say the fictional corporation Scatterholt has user logins with hundreds of thousands of consumer logins. Attackers breach Scatterholt and access the identity and access management system, then they steal these credentials and leak them onto the dark web.
It’s easy enough for Scatterholt corporation to force a password reset across all users, but chances are these users have reused the same password across many services.
This leak allows threat actors to use brute forcing/pentesting tools to attempt to brute force credentials for thousands of users on other applications that they may have used the same password for.
Defending Against Tier 1 Leaked Credentials
There are numerous well-researched defenses that organizations can use to reduce risk. First and most importantly: monitor a leaked credentials database for corporate employee emails. This alone can make a massive difference as threat actors deliberately seek out passwords associated with corporate email addresses to facilitate data breaches.
Secondly, require users to routinely reset passwords on a time-schedule so that if a specific password is breached, they will have already rotated other corporate credentials.
Finally, we recommend employing a password manager with a policy that requires employees to randomize passwords to various applications and store them with the manager, reducing the risk that employees will only make small changes to passwords.
The Special Case of Combolists
Combolists are typically composed of credential pairs that are either organized by service, or geographically, which are then used by cybercriminals in combination with Brute Forcing tools to attempt to gain access to various services.
Source: Flare
These credentials usually come from previous known breaches, or stealer logs, or sometimes totally made up; the original source is never totally clear, but the sheer amount of credentials one can acquire through combolists combined with frequent password reuse on the user’s part still makes them a considerable attack vector.
Tier 2
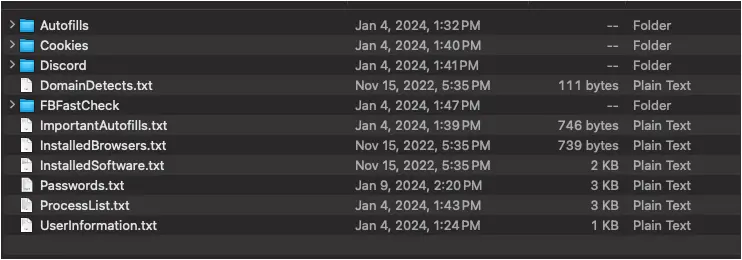
Tier 2 leaked credentials pose a special degree of risk to companies. These are credentials harvested directly from the user through infostealer malware that steals all passwords saved in the browser.
We consider tier 2 leaked credentials to be of significantly increased risk to both the company and the user for the following reasons:
- A single stealer log will contain all of the credentials the user saved in their browser. This creates a perfect opportunity for threat actors to socially engineer the victim, the IT help desk, or even the company using the victims information.
- These logs contain the plain text username, password, and host for the credentials, often for hundreds of different logins. Threat actors have an enormous advantage when they can see dozens of password variations that the user uses.
- These logs often contain form fill data with answers to secret questions which can be effectively used to bypass websites with secret questions.
Source: Flare
Tier 3 Leaked Credentials
This tier of leaks is also from stealer logs, but pose extreme risk to the organization. Fresh stealer logs often have active session cookies in them which can be easily used by actors for session hijacking attacks in which they impersonate the victim and potentially bypass 2FA and MFA controls.
Finding a fresh stealer log being distributed with corporate credentials should immediately prompt an incident investigation, as it is highly likely that the passwords are working and that actors could directly access corporate resources.
Source: Flare
Defending Against Tier 3 Leaked Credentials
Where possible limit TTL for corporate applications to reduce the risk of session cookies still being valid if distributed as a result of an infostealer infection.
Multi-Factor Authentication isn’t a Silver Bullet
If you aren’t monitoring for leaked credentials and you likely have single-factor authentication for many of your employees since many of them will have exposed passwords.
Many people are under the impression that having two-factor authentication enabled is protection enough from stolen credentials, but the reality, as we’ve witnessed many times over, is that threat actors are very conscious of the barrier 2FA imposes and have techniques and strategies to get over the hurdle.
Whether through social engineering of employees, or using 2FA bots to capture the one-time code/password from their victims, or even SIM-swapping, there is a surprising amount of ways to bypass multi-factor authentication controls that are actively used in the wild.
The best defense against those types of attacks feature the use of authenticator apps, which feature temporary rotating codes rather than the one-time passwords users may get via email or SMS, as these applications are usually much more secure, and to a certain extent ensure the user in question has control of (usually) a second device.
Worried about Credentials? Flare Can Help
Flare monitors more than 14 billion leaked credentials distributed on the dark web and hundreds of millions leaked through infostealer malware.
Our platform sets up in 30 minutes and provides robust detection for leaked employee credentials across hundreds of forums, channels, and marketplaces.
Sponsored and written by Flare.
