Critical Security Vulnerability Discovered in WooCommerce Stripe Gateway Plugin
A security flaw has been uncovered in the WooCommerce Stripe Gateway WordPress plugin that could lead to the unauthorized disclosure of sensitive information.
The flaw, tracked as CVE-2023-34000, impacts versions 7.4.0 and below. It was addressed by the plugin maintainers in version 7.4.1, which shipped on May 30, 2023.
WooCommerce Stripe Gateway allows e-commerce websites to directly accept various payment methods through Stripe’s payment processing API. It boasts of over 900,000 active installations.
According to Patch security researcher Rafie Muhammad, the plugin suffers from what’s called an unauthenticated Insecure direct object references (IDOR) vulnerability, which allows a bad actor to bypass authorization and access resources.
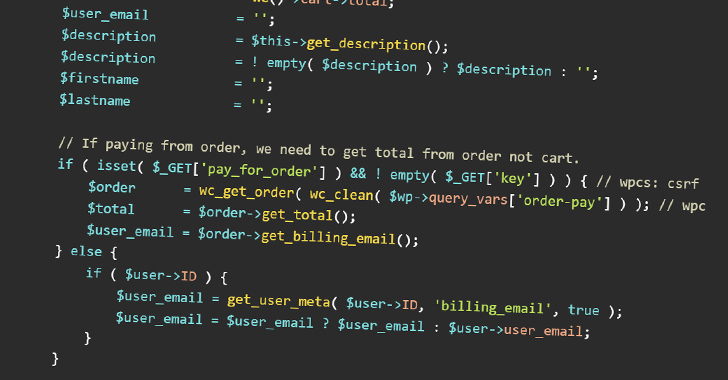
Specially, the problem stems from the insecure handling of order objects and a lack of adequate access control mechanism in the plugin’s ‘javascript_params’ and ‘payment_fields’ functions of the plugin.
“This vulnerability allows any unauthenticated user to view any WooCommnerce order’s PII data including email, user’s name, and full address,” Muhammad said.
The development comes weeks after the WordPress core team released 6.2.1 and 6.2.2 to address five security issues, including an unauthenticated directory traversal vulnerability and an unauthenticated cross-site scripting flaw, three of which were uncovered during a third-party security audit.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.






![[SAFEPAY] - Ransomware Victim: frapack[.]de 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)